Newsfeed
Nachrichtenbote
This week, we have received a number of reports on yet another ransomware, BandarChor.
This ransomware is not exactly fresh. The first infections that we've noticed related to this family came in already last November.
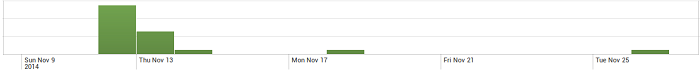
We have had reports of BandarChor being spread via email and have seen indicators that it may have been distributed by exploit kits.
Upon execution, the malware drops a copy of itself in Startup directory as well as the ransom notification image.
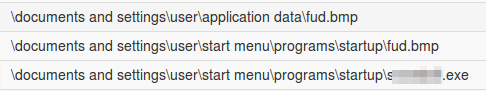
Then it proceeds in its attempt to encrypt files with various file extensions such as: doc, xls, jpg and the like.
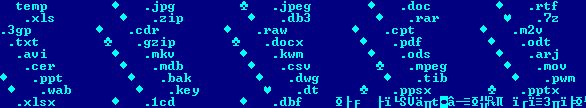
After encryption, the files will be renamed as [filename].id-[ID][email protected].
Then it reports the user's computer name and ID to a remote location via HTTP POST.
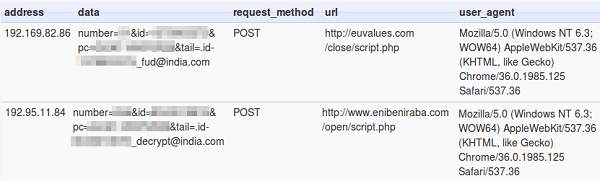
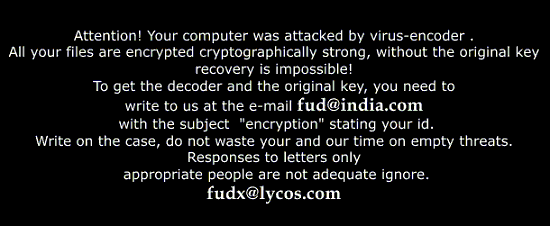
Here's what the ransom message looks like.
Here's a list of other domains that we've seen related to this threat:
martyanovdrweb.com
www.fuck-isil.com
www.ahalaymahalay.com
kapustakapaet.com
www.decryptindia.com
www.enibeniraba.com
www.netupite.com
89025840.com
xsmailsos.com
sosxsmaillockedwriteonxsmailindia.com
baitforany.com
euvalues.com
We are detecting this threat as Trojan:W32/BandarChor.
Hashes:
ba8909eef5ee280ae43b935cf4ae38ccf21bde56
afd4216e93a82feebafd3a68e9308ca4b0b54372
b4362fcd75fd071fc8237c543c56df5736b8e177
31aa8ec187e1241a94127336996f9cb38719eb9b
4b356b88fb3a3dce1f009e4e92cd4a59383e0764
5f71be645e8ac995555a891087b46ed357386dbe
de7ced27456a1e4581d6a4bf126f56061b7f9859
On 06/03/15 At 04:45 PM
Weiterlesen...
This ransomware is not exactly fresh. The first infections that we've noticed related to this family came in already last November.

We have had reports of BandarChor being spread via email and have seen indicators that it may have been distributed by exploit kits.
Upon execution, the malware drops a copy of itself in Startup directory as well as the ransom notification image.
Then it proceeds in its attempt to encrypt files with various file extensions such as: doc, xls, jpg and the like.
After encryption, the files will be renamed as [filename].id-[ID][email protected].

Then it reports the user's computer name and ID to a remote location via HTTP POST.

Here's what the ransom message looks like.

Here's a list of other domains that we've seen related to this threat:
martyanovdrweb.com
www.fuck-isil.com
www.ahalaymahalay.com
kapustakapaet.com
www.decryptindia.com
www.enibeniraba.com
www.netupite.com
89025840.com
xsmailsos.com
sosxsmaillockedwriteonxsmailindia.com
baitforany.com
euvalues.com
We are detecting this threat as Trojan:W32/BandarChor.
Hashes:
ba8909eef5ee280ae43b935cf4ae38ccf21bde56
afd4216e93a82feebafd3a68e9308ca4b0b54372
b4362fcd75fd071fc8237c543c56df5736b8e177
31aa8ec187e1241a94127336996f9cb38719eb9b
4b356b88fb3a3dce1f009e4e92cd4a59383e0764
5f71be645e8ac995555a891087b46ed357386dbe
de7ced27456a1e4581d6a4bf126f56061b7f9859
On 06/03/15 At 04:45 PM
Weiterlesen...
