Newsfeed
Nachrichtenbote
Last week, we wrote about a ransom trojan called Trojan:W32/Ransomcrypt which encrypts documents, images, videos, et cetera and holds the files hostage for 50.
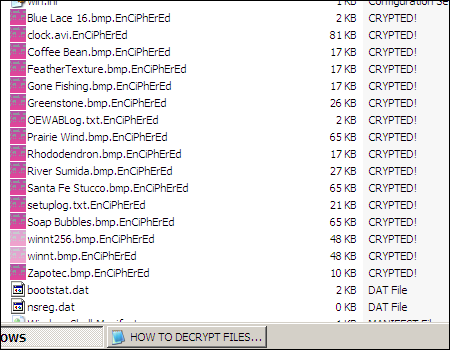
Ransomcrypt encrypts files using Tiny Encryption Algorithm (TEA). The key is formed from a "base key" which is modified based on the first character of the name of the file that is being encrypted to form a "file specific key". Both the base key and the file specific key are 16 bytes long.
Our analysts have created a decryption script, written in Python, for our support team. Fortunately, we've only seen a small number of customer cases. The decryption script works with two variants of Ransomcrypt.
• Trojan:W32/RansomCrypt.A, SHA1: b8f60c64c70f03c263bf9e9261aa157a73864aaf
• Trojan:W32/RansomCrypt.B, SHA1: 1e41e641e54bb6fb26b5706e39b90c93165bcb0b

Read the EULT here.
Download: fs_randec.zip, SHA1: 9ab467572691f9b6525cc8f76925757a543a95d8
Pay particular attention to the directive that you should first attempt to use this script on a copy of the encrypted files.
Do not use the "originals".
On 19/04/12 At 03:35 PM
Weiterlesen...

Ransomcrypt encrypts files using Tiny Encryption Algorithm (TEA). The key is formed from a "base key" which is modified based on the first character of the name of the file that is being encrypted to form a "file specific key". Both the base key and the file specific key are 16 bytes long.
Our analysts have created a decryption script, written in Python, for our support team. Fortunately, we've only seen a small number of customer cases. The decryption script works with two variants of Ransomcrypt.
• Trojan:W32/RansomCrypt.A, SHA1: b8f60c64c70f03c263bf9e9261aa157a73864aaf
• Trojan:W32/RansomCrypt.B, SHA1: 1e41e641e54bb6fb26b5706e39b90c93165bcb0b

Read the EULT here.
Download: fs_randec.zip, SHA1: 9ab467572691f9b6525cc8f76925757a543a95d8
Pay particular attention to the directive that you should first attempt to use this script on a copy of the encrypted files.
Do not use the "originals".
On 19/04/12 At 03:35 PM
Weiterlesen...
