Newsfeed
Nachrichtenbote
We have recently observed a significant increase in infections from a nasty strain of file-encrypting ransomware called CTB-Locker.
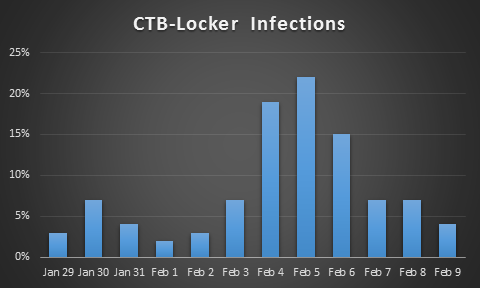
Daily CTB-Locker infections in relation to the total number of such infections this year.
CTB-Locker is most commonly spread through email spam. These emails usually contain an attached .zip file that contains a second .zip file that finally contains an .scr executable file. This executable is a malicious downloader known as Dalexis. If the user executes the .scr file, the downloader will attempt to contact a predetermined list of compromised websites hosting encrypted copies of CTB-Locker. It will then proceed to download, decrypt and execute CTB-Locker. In other cases, the malicious attachment won't be a .zip file, but instead it'll be a .cab file. Again, the .cab file is actually Dalexis which will proceed to infect the victim's computer with CTB-Locker.
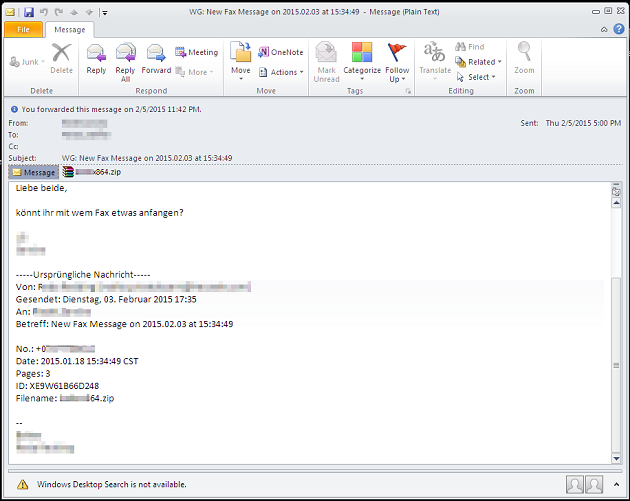
An example of spam used to spread CTB-Locker.
Upon infection, CTB-Locker will encrypt the victim's files and append the original filenames with a randomly generated 7 character long extension. Additionally, it will proceed to write a copy of itself to the users local temporary files folder with a randomly generated name of 7 characters and the extension .exe. To ensure CTB-Locker is kept running, it will create a scheduled task with a randomly generated 7 character name. Lastly, CTB-Locker will present the victim with a ransom notice and countdown timer showing how long the victim has left to pay the ransom. CTB-Locker will also change the victim's desktop background picture to an image containing the same ransom payment instructions. Finally, a copy of the same instructions will also be stored to the victim's My Documents folder as both an image and a text file, with the names Decrypt All Files [random 7 characters].bmp and Decrypt All Files [random 7 characters].txt respectively. The ransom instructions will direct the victim to pay the ransom, in Bitcoins, to a specified Bitcoin address. In most cases, we have observed the ransom to be 3 BTC (about 650USD or 575EUR).
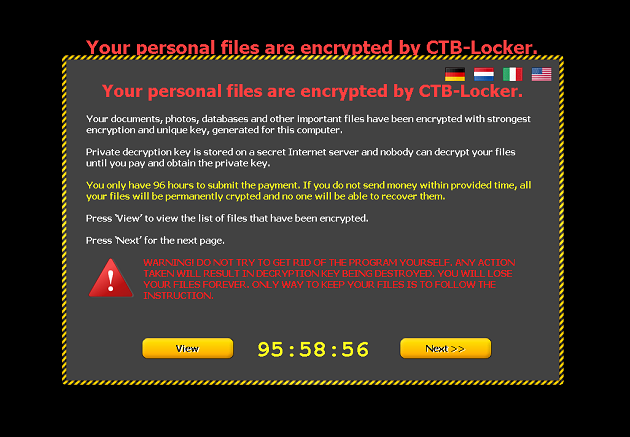
The ransom notice displayed by CTB-Locker.
There is no known way to break the encryption used by CTB-Locker. Therefore the only way for a victim to get their files back is from back ups or by receiving the decryption key from the malware operators. However, you should never pay the ransom, as you'll only help finance the criminal activities of malware operators! There is also no guarantee paying the ransom will actually get you your files back. That's entirely up to the trustworthiness of the criminals.
To protect against threats such as CTB-Locker and other file-encrypting ransomware, you should ensure you are running an up-to-date antivirus solution. You should also take care to not open executable files received as email attachments. In addition to preventative actions, it might be a good idea to attempt to minimize the damage a ransomware infection can cause. Most importantly, you should take regular back ups of all your data. If you use network shares, you should additionally be aware that CTB-Locker will search all mounted drives for files to encrypt including network storage or other mapped shares. In such cases, we recommend you consider restricting write permissions to such shares and keeping them mounted only when strictly necessary.
We detect CTB-Locker variously as Trojan.CTBLocker.Gen.1 and Trojan.Downloader.CryptoLocker.F
We also detect the malicious attachments leading to CTB-Locker as Trojan-Downloader:W32/Dalexis.B
Sample hashes:
6eb03d6cb4f9a5aae49a9d85652a4daa4f984ba8 (Dalexis)
f1897120c2bbcd5135db0295249118aa5f5eb116 (Dalexis)
81f68349b12f22beb8d4cf50ea54d854eaa39c89 (CTB-Locker)
Files suggesting a CTB-Locker infection:
%TEMP%\[random 7 characters].exe
%USERPROFILE%\My Documents\Decrypt All Files [random 7 characters].bmp
%USERPROFILE%\My Documents\Decrypt All Files [random 7 characters].txt
Any files with an extension of 7 random characters
On 09/02/15 At 03:12 PM
Weiterlesen...

Daily CTB-Locker infections in relation to the total number of such infections this year.
CTB-Locker is most commonly spread through email spam. These emails usually contain an attached .zip file that contains a second .zip file that finally contains an .scr executable file. This executable is a malicious downloader known as Dalexis. If the user executes the .scr file, the downloader will attempt to contact a predetermined list of compromised websites hosting encrypted copies of CTB-Locker. It will then proceed to download, decrypt and execute CTB-Locker. In other cases, the malicious attachment won't be a .zip file, but instead it'll be a .cab file. Again, the .cab file is actually Dalexis which will proceed to infect the victim's computer with CTB-Locker.
An example of spam used to spread CTB-Locker.
Upon infection, CTB-Locker will encrypt the victim's files and append the original filenames with a randomly generated 7 character long extension. Additionally, it will proceed to write a copy of itself to the users local temporary files folder with a randomly generated name of 7 characters and the extension .exe. To ensure CTB-Locker is kept running, it will create a scheduled task with a randomly generated 7 character name. Lastly, CTB-Locker will present the victim with a ransom notice and countdown timer showing how long the victim has left to pay the ransom. CTB-Locker will also change the victim's desktop background picture to an image containing the same ransom payment instructions. Finally, a copy of the same instructions will also be stored to the victim's My Documents folder as both an image and a text file, with the names Decrypt All Files [random 7 characters].bmp and Decrypt All Files [random 7 characters].txt respectively. The ransom instructions will direct the victim to pay the ransom, in Bitcoins, to a specified Bitcoin address. In most cases, we have observed the ransom to be 3 BTC (about 650USD or 575EUR).

The ransom notice displayed by CTB-Locker.
There is no known way to break the encryption used by CTB-Locker. Therefore the only way for a victim to get their files back is from back ups or by receiving the decryption key from the malware operators. However, you should never pay the ransom, as you'll only help finance the criminal activities of malware operators! There is also no guarantee paying the ransom will actually get you your files back. That's entirely up to the trustworthiness of the criminals.
To protect against threats such as CTB-Locker and other file-encrypting ransomware, you should ensure you are running an up-to-date antivirus solution. You should also take care to not open executable files received as email attachments. In addition to preventative actions, it might be a good idea to attempt to minimize the damage a ransomware infection can cause. Most importantly, you should take regular back ups of all your data. If you use network shares, you should additionally be aware that CTB-Locker will search all mounted drives for files to encrypt including network storage or other mapped shares. In such cases, we recommend you consider restricting write permissions to such shares and keeping them mounted only when strictly necessary.
We detect CTB-Locker variously as Trojan.CTBLocker.Gen.1 and Trojan.Downloader.CryptoLocker.F
We also detect the malicious attachments leading to CTB-Locker as Trojan-Downloader:W32/Dalexis.B
Sample hashes:
6eb03d6cb4f9a5aae49a9d85652a4daa4f984ba8 (Dalexis)
f1897120c2bbcd5135db0295249118aa5f5eb116 (Dalexis)
81f68349b12f22beb8d4cf50ea54d854eaa39c89 (CTB-Locker)
Files suggesting a CTB-Locker infection:
%TEMP%\[random 7 characters].exe
%USERPROFILE%\My Documents\Decrypt All Files [random 7 characters].bmp
%USERPROFILE%\My Documents\Decrypt All Files [random 7 characters].txt
Any files with an extension of 7 random characters
On 09/02/15 At 03:12 PM
Weiterlesen...
