Newsfeed
Nachrichtenbote
Exploit kits continue to be a critical tool for the propagation of crimeware. New exploit kits have appeared this year, and this post will discuss two of them — Archie and Astrum.
Archie EK was first described in August as a basic exploit kit, as it uses exploit modules copied from the Metasploit Framework.
We detect the exploits used by Archie EK, and so upon review of our telemetry, we can see the kit made its first appearance during the first week of July. It has remained active since then.
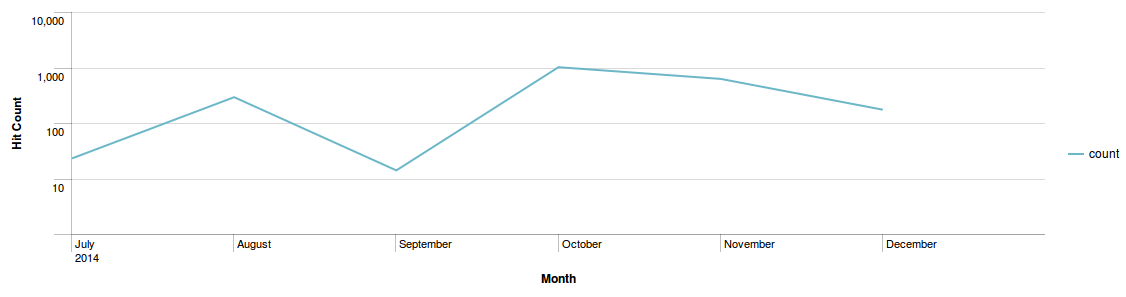
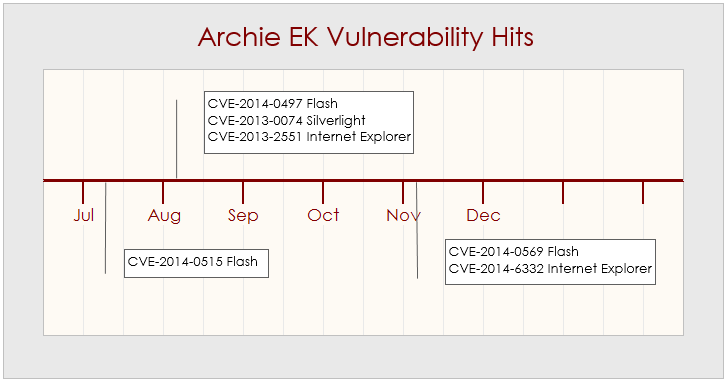
From July, we've seen hits of CVE-2014-0515 (Flash) exploit with Archie EK traffic, and then in the following month, we noticed detections of CVE-2014-0497 (Flash), CVE-2013-0074 (Silverlight), and CVE-2013-2551 (Internet Explorer) exploits. By November, Kafeine spotted new Flash vulnerability CVE-2014-0569 and IE vulnerability CVE-2014-6332 integrated in this exploit kit, which has also been evident from our upstream.
We detect exploits used by Archie EK as:
• Exploit:HTML/CVE-2013-2551.B
• Exploit:JS/ArchieEK.A
• Exploit:JS/ArchieEK.B
• Exploit:MSIL/CVE-2013-0074.E
• Exploit:SWF/CVE-2014-0515.C
• Exploit:SWF/CVE-2014-0569.A
• Exploit:SWF/Salama.D
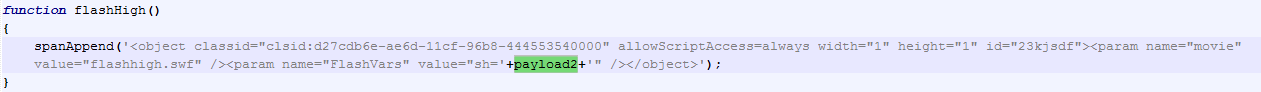
Just like other exploit kits, this kit has evolved over the months, not only in the vulnerability support but also its landing page. The early samples of Archie we encountered used straightforward filenames and variable names such as "pluginDet.js" and "payload".
Below is a code snippet of the earlier landing page:
However, during November, we started to see new samples with slight modifications attempting to add some obfuscation. It is now using random looking strings instead of simple descriptive variable names. Below is a code snippet of a recent landing page sample.
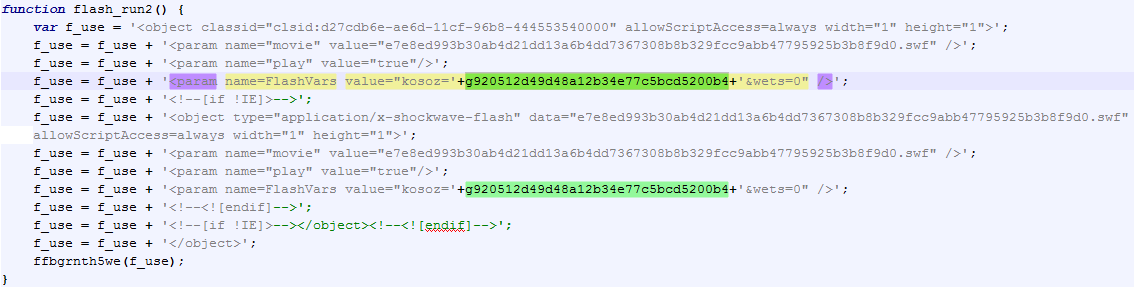
It also includes checks for Antivirus and VMware files that was not in the early versions:
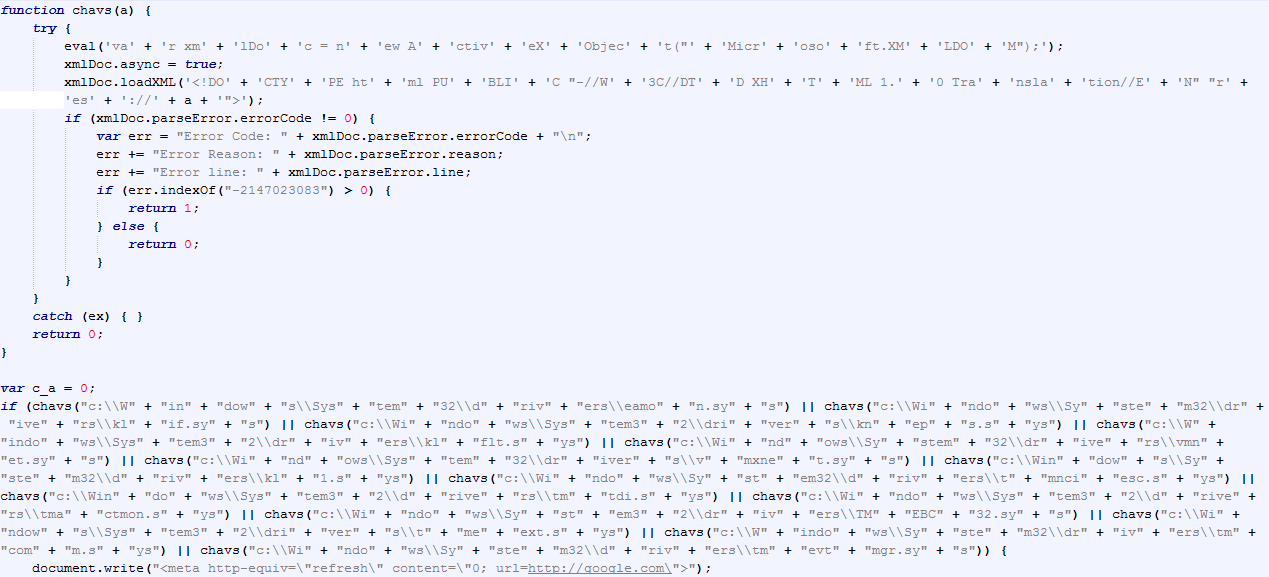
We detect these landing pages as Exploit:JS/ArchieEK.A and Exploit:JS/ArchieEK.B.
The URL patterns of Archie were also simple and used descriptive filenames in its traffic such as below:
• http://144. 76.36.67/flashhigh.swf
• http://144. 76.36.67/flashlow.swf
• http://144. 76.36.67/ie8910.html
• http://144. 76.36.67/silverapp1.xap
But recently, we've observed a different pattern that uses a SHA256 string for the filenames:
• http://31. 184.194.99/0d495794f41827de0f8679412e1823c8
• http://31. 184.194.99/cd8e0a126d3c528fce042dfb7f0f725055a04712d171ad0f94f94d5173cd90d2.html
• http://31. 184.194.99/9edcdf010cd9204e740b7661e46c303180e2d674417193cc6cbadc861fdf508a.swf
• http://31. 184.194.99/e7e8ed993b30ab4d21dd13a6b4dd7367308b8b329fcc9abb47795925b3b8f9d0.swf
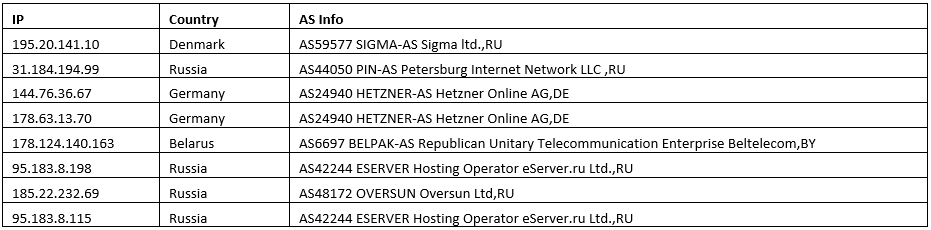
Below are reported IP addresses from our upstream where this kit is hosted:
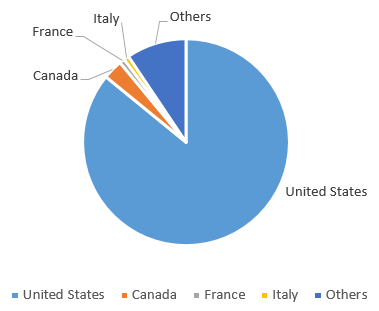
From our telemetry, the most affected countries are the United States and Canada.
The common payload of Archie EK is a Trojan Clicker. Below are example hashes this kit delivered based on our upstream, and we detect them as follows:
• 8b29dc79dfd0bcfb22e8954c65066be508bb1529 - Gen:Variant.Graftor.152508
• 1850a174582c8b1c31dfcbe1ff53ebb67d8bde0d - Gen:Trojan.Heur.PT.fy4@bOYsAwl
• 2150d6762db6ec98e92bb009b3bdacb9a640df04 - Generic.Malware.SFdld!!.8499435C
• 5a89a48fa8ef92d1a4b31ee20f3f630e73c1c6c2 - Generic.Malware.SFdld!!.294B1B47
Astrum EK is another new player in the exploit kit market this year. It was first reported by Kafeine in September, and was found to be one of the kits the Reveton gang has started to use.
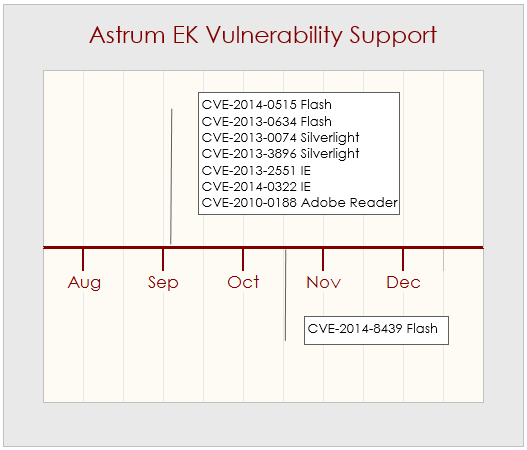
Initially, it has support for the following vulnerabilities: CVE-2014-0515/CVE-2013-0634 (Flash), CVE-2013-0074/CVE-2013-3896 (Silverlight), CVE-2013-2551/CVE-2014-0322 (Internet Explorer), and CVE-2010-0188 (Adobe Reader). In October, Kafeine spotted that Astrum EK is exploiting CVE-2014-8439, a Flash vulnerability that we discovered together with Kafeine.
Being one of the new players in the exploit kit market this year, it has also been evident in our telemetry and continues its activity up to now.
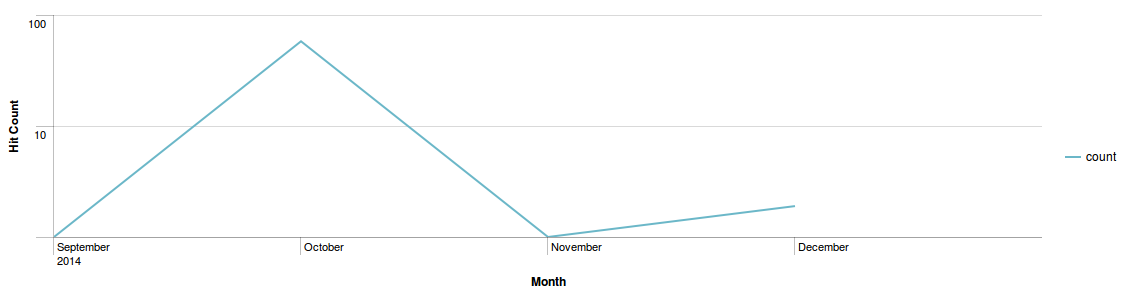
Unlike Archie exploit kit, Astrum uses a lot of obfuscation in its landing page. Below are code snippets of two landing pages that are basically the same, but the second one having added garbage comments and spaces in between codes to add more obfuscation to avoid detection:

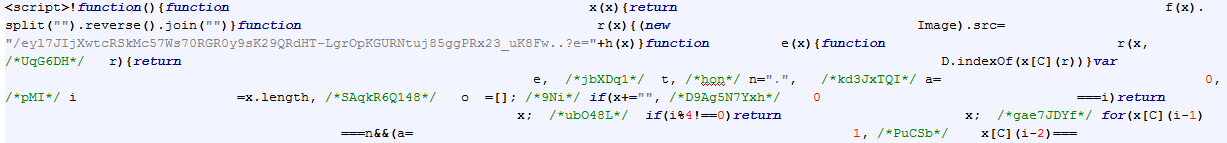
As has also been described by Kafeine, deobfuscated code shows checking of analyst tools and Kaspersky's plugin:
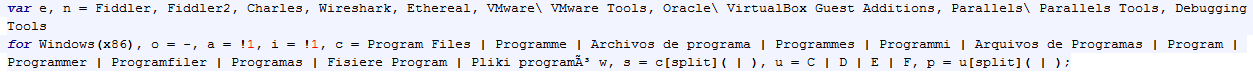
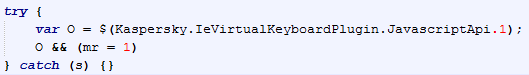
We detect the landing pages as Exploit:JS/AstrumEK.A and Exploit:JS/AstrumEK.B.
Astrum has an identifiable URL pattern such as below:
• http://ad7. […].com.ar/QRtVMKEnSCR8eD9fnxd2SHxwOl7GRXQaKC5kXc4ULxt6IWlcy0omTTI9bg-cDmhPKQ..
• http://adv2. […].com.ar/Zhc_UrNYeTNRKVVsiDscWV57AGvSbhcJAy5baY0-EA4NLFQ73WETCxUxBG2OcVlYDg..
• http://pic2. […].net.au/nGtsDdma82ajBwA2t_jOC6FUCjW--MsC-FVZYeOuywn3BgYy4fPIV-9NVTjks9MO8w..
• http://pic2. […].net.au/nHEeB7017BijH3duhVKAdqJJJDvcVtIh90UvaNdf03ylHSY7gwrQJu9XJzKAHMxw8w..
• http://cdn-net4. […].net.au/Y9fEaE97uN9d7v0FdRyCs1yy_wopS9zhDO_3CSVI3uAI7KhQI0fV4RDx_1R3Upi0Cg..
• http://cdn-net8[…].net.au/4xuNWu0qxwyNdLxn0xysbIsg6jPeTq9jjnO5MNsZoWPTcbNqgBL_PJA9tmbVA-dnig..
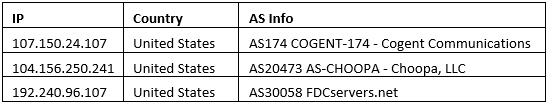
Below are reported IP addresses where Astrum EK is hosted:
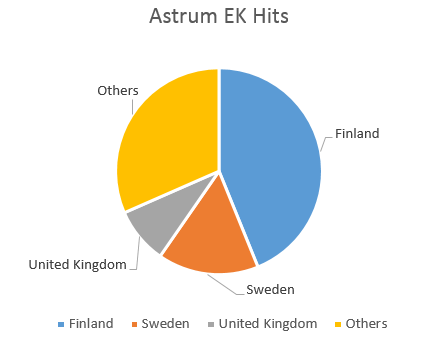
Based on our telemetry, we have hits of Astrum EK from the countries below:
Archie and Astrum are only two of the new ones. There are also other new kits such as Rig, Null Hole, and Niteris (CottonCastle), and other exploit kits continue to rise and evolve such as Angler, Nuclear, Neutrino, FlashEK, Fiesta, SweetOrange, and others.
One notable characteristic with these exploit kits is that checking of Antivirus files, VMware files and other analyst tools are now becoming common. Other exploit kits, such as Nuclear and Angler, have also integrated these checks to avoid being analyzed by malware researchers. You can read more about that from Kafeine's blog.
On 11/12/14 At 12:34 PM
Weiterlesen...
Archie EK was first described in August as a basic exploit kit, as it uses exploit modules copied from the Metasploit Framework.
We detect the exploits used by Archie EK, and so upon review of our telemetry, we can see the kit made its first appearance during the first week of July. It has remained active since then.
From July, we've seen hits of CVE-2014-0515 (Flash) exploit with Archie EK traffic, and then in the following month, we noticed detections of CVE-2014-0497 (Flash), CVE-2013-0074 (Silverlight), and CVE-2013-2551 (Internet Explorer) exploits. By November, Kafeine spotted new Flash vulnerability CVE-2014-0569 and IE vulnerability CVE-2014-6332 integrated in this exploit kit, which has also been evident from our upstream.
We detect exploits used by Archie EK as:
• Exploit:HTML/CVE-2013-2551.B
• Exploit:JS/ArchieEK.A
• Exploit:JS/ArchieEK.B
• Exploit:MSIL/CVE-2013-0074.E
• Exploit:SWF/CVE-2014-0515.C
• Exploit:SWF/CVE-2014-0569.A
• Exploit:SWF/Salama.D
Just like other exploit kits, this kit has evolved over the months, not only in the vulnerability support but also its landing page. The early samples of Archie we encountered used straightforward filenames and variable names such as "pluginDet.js" and "payload".
Below is a code snippet of the earlier landing page:
However, during November, we started to see new samples with slight modifications attempting to add some obfuscation. It is now using random looking strings instead of simple descriptive variable names. Below is a code snippet of a recent landing page sample.
It also includes checks for Antivirus and VMware files that was not in the early versions:
We detect these landing pages as Exploit:JS/ArchieEK.A and Exploit:JS/ArchieEK.B.
The URL patterns of Archie were also simple and used descriptive filenames in its traffic such as below:
• http://144. 76.36.67/flashhigh.swf
• http://144. 76.36.67/flashlow.swf
• http://144. 76.36.67/ie8910.html
• http://144. 76.36.67/silverapp1.xap
But recently, we've observed a different pattern that uses a SHA256 string for the filenames:
• http://31. 184.194.99/0d495794f41827de0f8679412e1823c8
• http://31. 184.194.99/cd8e0a126d3c528fce042dfb7f0f725055a04712d171ad0f94f94d5173cd90d2.html
• http://31. 184.194.99/9edcdf010cd9204e740b7661e46c303180e2d674417193cc6cbadc861fdf508a.swf
• http://31. 184.194.99/e7e8ed993b30ab4d21dd13a6b4dd7367308b8b329fcc9abb47795925b3b8f9d0.swf
Below are reported IP addresses from our upstream where this kit is hosted:
From our telemetry, the most affected countries are the United States and Canada.
The common payload of Archie EK is a Trojan Clicker. Below are example hashes this kit delivered based on our upstream, and we detect them as follows:
• 8b29dc79dfd0bcfb22e8954c65066be508bb1529 - Gen:Variant.Graftor.152508
• 1850a174582c8b1c31dfcbe1ff53ebb67d8bde0d - Gen:Trojan.Heur.PT.fy4@bOYsAwl
• 2150d6762db6ec98e92bb009b3bdacb9a640df04 - Generic.Malware.SFdld!!.8499435C
• 5a89a48fa8ef92d1a4b31ee20f3f630e73c1c6c2 - Generic.Malware.SFdld!!.294B1B47
Astrum EK is another new player in the exploit kit market this year. It was first reported by Kafeine in September, and was found to be one of the kits the Reveton gang has started to use.
Initially, it has support for the following vulnerabilities: CVE-2014-0515/CVE-2013-0634 (Flash), CVE-2013-0074/CVE-2013-3896 (Silverlight), CVE-2013-2551/CVE-2014-0322 (Internet Explorer), and CVE-2010-0188 (Adobe Reader). In October, Kafeine spotted that Astrum EK is exploiting CVE-2014-8439, a Flash vulnerability that we discovered together with Kafeine.
Being one of the new players in the exploit kit market this year, it has also been evident in our telemetry and continues its activity up to now.
Unlike Archie exploit kit, Astrum uses a lot of obfuscation in its landing page. Below are code snippets of two landing pages that are basically the same, but the second one having added garbage comments and spaces in between codes to add more obfuscation to avoid detection:
As has also been described by Kafeine, deobfuscated code shows checking of analyst tools and Kaspersky's plugin:
We detect the landing pages as Exploit:JS/AstrumEK.A and Exploit:JS/AstrumEK.B.
Astrum has an identifiable URL pattern such as below:
• http://ad7. […].com.ar/QRtVMKEnSCR8eD9fnxd2SHxwOl7GRXQaKC5kXc4ULxt6IWlcy0omTTI9bg-cDmhPKQ..
• http://adv2. […].com.ar/Zhc_UrNYeTNRKVVsiDscWV57AGvSbhcJAy5baY0-EA4NLFQ73WETCxUxBG2OcVlYDg..
• http://pic2. […].net.au/nGtsDdma82ajBwA2t_jOC6FUCjW--MsC-FVZYeOuywn3BgYy4fPIV-9NVTjks9MO8w..
• http://pic2. […].net.au/nHEeB7017BijH3duhVKAdqJJJDvcVtIh90UvaNdf03ylHSY7gwrQJu9XJzKAHMxw8w..
• http://cdn-net4. […].net.au/Y9fEaE97uN9d7v0FdRyCs1yy_wopS9zhDO_3CSVI3uAI7KhQI0fV4RDx_1R3Upi0Cg..
• http://cdn-net8[…].net.au/4xuNWu0qxwyNdLxn0xysbIsg6jPeTq9jjnO5MNsZoWPTcbNqgBL_PJA9tmbVA-dnig..
Below are reported IP addresses where Astrum EK is hosted:
Based on our telemetry, we have hits of Astrum EK from the countries below:
Archie and Astrum are only two of the new ones. There are also other new kits such as Rig, Null Hole, and Niteris (CottonCastle), and other exploit kits continue to rise and evolve such as Angler, Nuclear, Neutrino, FlashEK, Fiesta, SweetOrange, and others.
One notable characteristic with these exploit kits is that checking of Antivirus files, VMware files and other analyst tools are now becoming common. Other exploit kits, such as Nuclear and Angler, have also integrated these checks to avoid being analyzed by malware researchers. You can read more about that from Kafeine's blog.
On 11/12/14 At 12:34 PM
Weiterlesen...
