Newsfeed
Nachrichtenbote
Tibia is a massively multiplayer online role-playing game (MMORPG). See part one of this post for more details.
Open Tibia players use "IP Changer" applications to reconfigure their Tibia clients.
We recently analyzed a sample which included one such IP Changer. It's detected as Trojan-Dropper.W32/Agent.EUJ.
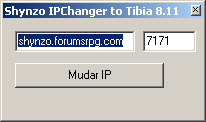
Agent.EUJ has a file size of 728,637 bytes and is packed with FSG 2.0. When the file is executed it runs this IP Changer:
It also installs a Trojan-Spy on the player's computer.
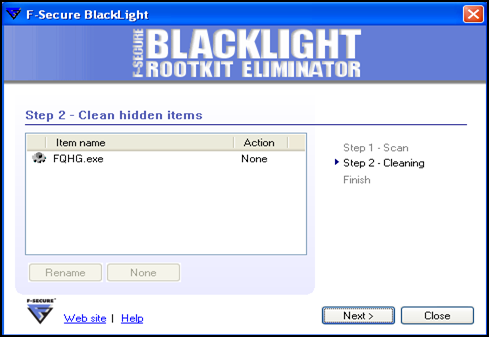
BlackLight reveals FQHG.exe hidden in the process list.
So this is what happens when Agent.EUJ is executed…
It drops and executes:
C:\WIN.EXE – detected as Trojan-Dropper.Win32.Small.awz
C:\SHYNZO IPCHANGER.EXE – which is a non-malicious IP Changer
Small.awz is compiled in Microsoft Visual C++ 6.0 with a file size of 492,166 bytes. It creates the following files:
%temp%\@{random hex numbers}.tmp – a library file detected as Monitor.Win32.Ardamax.o
%temp%\@{random hex numbers}.tmp – a non-executable file which has embedded malicious executable files
Small.awz then loads the library file and executes its exported function "sfx_main". This library file extracts the embedded malicious executable files in the non-executable file "%temp%\@{random hex numbers}.tmp" and drops it to the folder %windir%\Sys32.
%windir%\Sys32\FQGH.006 – detected as Trojan-Spy:W32/Ardamax.N
%windir%\Sys32\FQGH.007 – detected as Monitor.Win32.Ardamax.o
%windir%\Sys32\FQGH.exe – detected as Trojan-Spy.Win32.Ardamax.r
%windir%\Sys32\AKV.exe – detected as Trojan-Spy.Win32.Ardamax.gz
Lastly, it executes Trojan-Spy.Win32.Ardamax.r.
Ardamax.r is used by the files FQGH.006, FQGH.007 and AKV.exe as a component for hiding its process, to monitor processes, and to take snapshots of the system.
It creates the following Registry entry as its Autorun:
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
FQHG Agent = "%windir%\Sys32\FQHG.exe"
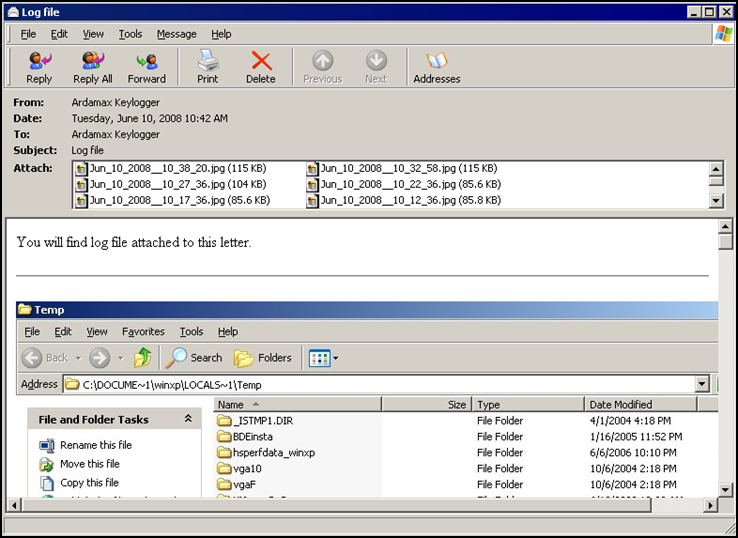
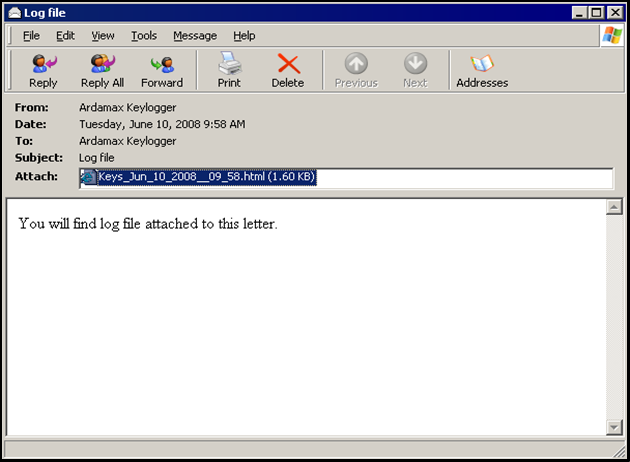
It then sends the snapshots and monitored processes via e-mail to "Ardamax Keylogger" .
E-mail message:
E-mail message:
Monitor logs:
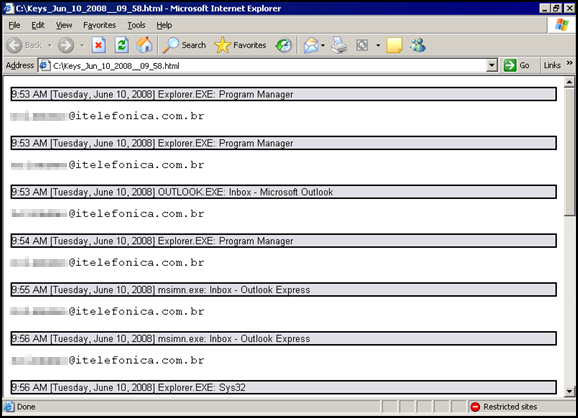
Online game passwords are frequently targeted for a variety of reasons.
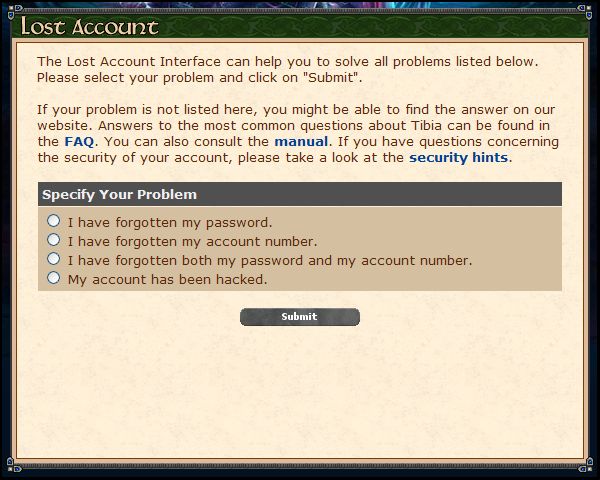
Hacked accounts are a common support issue. Check out option number four from Tibia's Lost Acconts page…
Response Team post by — Lordian & Sean On 03/07/08 At 06:06 PM
Weiterlesen...
Open Tibia players use "IP Changer" applications to reconfigure their Tibia clients.
We recently analyzed a sample which included one such IP Changer. It's detected as Trojan-Dropper.W32/Agent.EUJ.
Agent.EUJ has a file size of 728,637 bytes and is packed with FSG 2.0. When the file is executed it runs this IP Changer:

It also installs a Trojan-Spy on the player's computer.
BlackLight reveals FQHG.exe hidden in the process list.

So this is what happens when Agent.EUJ is executed…
It drops and executes:
C:\WIN.EXE – detected as Trojan-Dropper.Win32.Small.awz
C:\SHYNZO IPCHANGER.EXE – which is a non-malicious IP Changer
%temp%\@{random hex numbers}.tmp – a library file detected as Monitor.Win32.Ardamax.o
%temp%\@{random hex numbers}.tmp – a non-executable file which has embedded malicious executable files
%windir%\Sys32\FQGH.006 – detected as Trojan-Spy:W32/Ardamax.N
%windir%\Sys32\FQGH.007 – detected as Monitor.Win32.Ardamax.o
%windir%\Sys32\FQGH.exe – detected as Trojan-Spy.Win32.Ardamax.r
%windir%\Sys32\AKV.exe – detected as Trojan-Spy.Win32.Ardamax.gz
Ardamax.r is used by the files FQGH.006, FQGH.007 and AKV.exe as a component for hiding its process, to monitor processes, and to take snapshots of the system.
It creates the following Registry entry as its Autorun:
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
FQHG Agent = "%windir%\Sys32\FQHG.exe"
E-mail message:

E-mail message:

Monitor logs:

Online game passwords are frequently targeted for a variety of reasons.
Hacked accounts are a common support issue. Check out option number four from Tibia's Lost Acconts page…

Response Team post by — Lordian & Sean On 03/07/08 At 06:06 PM
Weiterlesen...
