Newsfeed
Nachrichtenbote
Security Advisories related to Microsoft Office were released last week. Regular weblog readers may have already read about them via other tech-news sources.
There's Microsoft Security Advisory 953635 which only affects Microsoft Office Word 2002 Service Pack 3. If you have that particular version of Word installed, you may want to download Word Viewer 2003 as a workaround, upgrade, or else avoid all external document files.
And then there's Microsoft Security Advisory 955179. A vulnerability in the ActiveX Control for Microsoft Access Snapshot Viewer which could allow remote code execution. This particular vulnerability made a number of headlines last week due to the Internet Explorer implications. It's currently unpatched and there have been some limited cases of an exploit in the wild.
One of the cases seen involved a patent themed site with thousands of pages injected with JavaScript. It looks like the site was hacked with a popular kit called Neosploit and the ActiveX exploit was added to the mix. That's only one site but many, many pages.
We weren't very familiar with the Snapshot tool so we experimented some earlier this week.
It ships with many versions of Microsoft Access previous to Office 2007. However, it isn't necessarily installed if you have Office 2003 with Access. The default option is to install the Snapshot Viewer on first use.
So what happens when Internet Explorer encounters an SNP file and you have a "Default" rather than "Full" installation of Office?
Well, first a legitimate file causes this prompt:
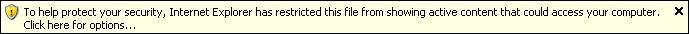
Then, if you elect to continue and push past a couple more prompts, IE will call on the Office installer.
In our experience, many people will then see the following prompt:
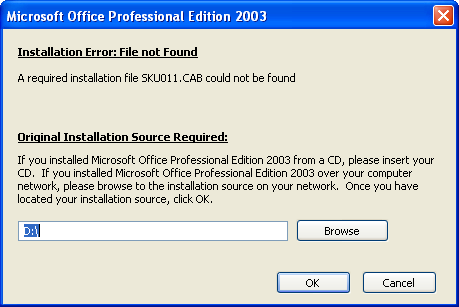
…and then you've got to go digging for your installation CD. Or perhaps you have to call the guys from IT to map out the network folder with the installation files.
That seems like a lot of trouble just to get the Snapshot Viewer OCX installed. So it's far from a perfect exploit.
But there are those that have the full installation of Access 2003, et cetera installed.
Think you might be vulnerable? Here is a test for you. Open this link — SNP.HTML — using Internet Explorer.
If you can easily read the "secret message" then you might want to set the killbits as recommend in MSA 955179.
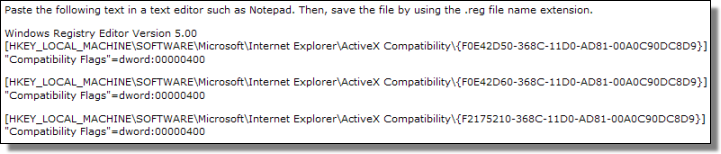 On 18/07/08 At 04:49 PM
On 18/07/08 At 04:49 PM
Weiterlesen...
There's Microsoft Security Advisory 953635 which only affects Microsoft Office Word 2002 Service Pack 3. If you have that particular version of Word installed, you may want to download Word Viewer 2003 as a workaround, upgrade, or else avoid all external document files.
And then there's Microsoft Security Advisory 955179. A vulnerability in the ActiveX Control for Microsoft Access Snapshot Viewer which could allow remote code execution. This particular vulnerability made a number of headlines last week due to the Internet Explorer implications. It's currently unpatched and there have been some limited cases of an exploit in the wild.
One of the cases seen involved a patent themed site with thousands of pages injected with JavaScript. It looks like the site was hacked with a popular kit called Neosploit and the ActiveX exploit was added to the mix. That's only one site but many, many pages.
We weren't very familiar with the Snapshot tool so we experimented some earlier this week.
It ships with many versions of Microsoft Access previous to Office 2007. However, it isn't necessarily installed if you have Office 2003 with Access. The default option is to install the Snapshot Viewer on first use.
So what happens when Internet Explorer encounters an SNP file and you have a "Default" rather than "Full" installation of Office?
Well, first a legitimate file causes this prompt:

Then, if you elect to continue and push past a couple more prompts, IE will call on the Office installer.
In our experience, many people will then see the following prompt:

…and then you've got to go digging for your installation CD. Or perhaps you have to call the guys from IT to map out the network folder with the installation files.
That seems like a lot of trouble just to get the Snapshot Viewer OCX installed. So it's far from a perfect exploit.
But there are those that have the full installation of Access 2003, et cetera installed.
Think you might be vulnerable? Here is a test for you. Open this link — SNP.HTML — using Internet Explorer.
If you can easily read the "secret message" then you might want to set the killbits as recommend in MSA 955179.
 On 18/07/08 At 04:49 PM
On 18/07/08 At 04:49 PMWeiterlesen...
