Newsfeed
Nachrichtenbote
We've been receiving lots of malicious flash file lately. Most of the flash file that we received has obfuscated shellcodes.
I stumble on one sample and gave a closer look on it. The obfuscation is simple, it only uses XOR and ADD instruction.
Basically, this flash file is taking advantage of the recent 0-day vulnerability in Adobe Flash Player. It downloads and execute a file from the following site:
hxtp://www.psp1122.cn/[removed].exe
We detect the downloaded EXE file as Trojan-PSW.Win32.OnlineGames.ayju and the flash file as Exploit.SWF.Downloader.a
Here's an animated image of decrypted shellcode:
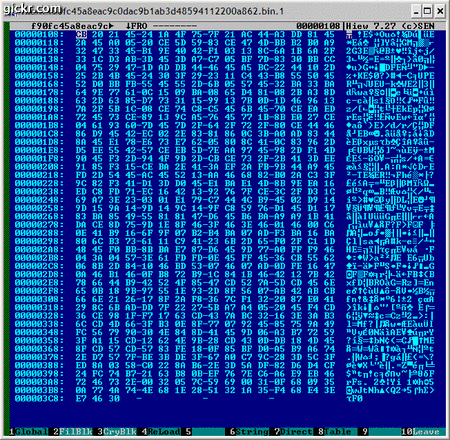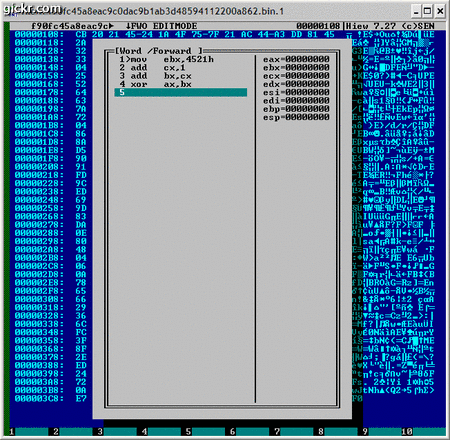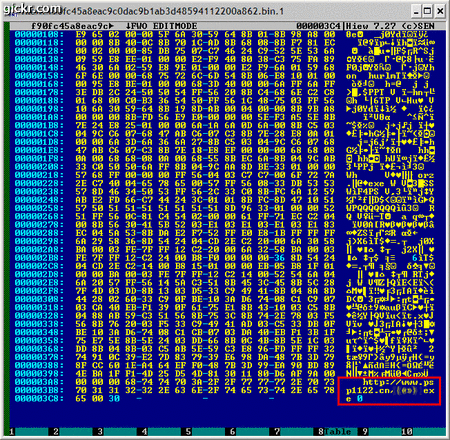
On 29/05/08 At 07:13 PM
Weiterlesen...
I stumble on one sample and gave a closer look on it. The obfuscation is simple, it only uses XOR and ADD instruction.
Basically, this flash file is taking advantage of the recent 0-day vulnerability in Adobe Flash Player. It downloads and execute a file from the following site:
hxtp://www.psp1122.cn/[removed].exe
We detect the downloaded EXE file as Trojan-PSW.Win32.OnlineGames.ayju and the flash file as Exploit.SWF.Downloader.a
Here's an animated image of decrypted shellcode:

On 29/05/08 At 07:13 PM
Weiterlesen...
