Newsfeed
Nachrichtenbote
Earlier today, while doing our daily data mining, we came across a new variant of ZeuS 2.x. It includes a new backdoor command called: win_unlock. Very interesting, turns out this slightly modified ZeuS 2.x includes a ransomware feature.
When this particular variant is executed, it opens Internet Explorer with a specific page (lex.creativesandboxs.com/locker/lock.php) and prevents the user from doing anything else with the infected system. The webpage that was opened presumably showed some type of extortion message, but it's currently unavailable because the site is offline.
The most straightforward way to unlock the system is to simply delete the trojan. This can be a bit tricky since the trojan prevents doing anything with the infected system, luckily the locking itself can be easily disabled first.
Looking at the code that corresponds with a received win_unlock command, it's clear the unlock information is stored to the registry.
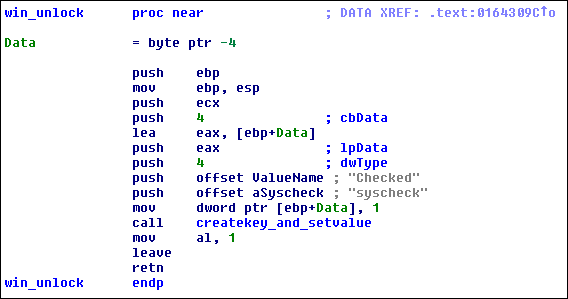
Unlocking can therefore be performed quite easily with a registry editor:
1. boot the system in safe mode
2. add a new key named syscheck under HKEY_CURRENT_USER
3. create a new DWORD value under the syscheck key
4. set the name of the new DWORD value to Checked
5. set the data for the Checked value to 1
6. reboot
SHA1: 03f0c26c6ba77c05152a1e0cc8bc5657f0c83119
Analysis by — Mikko S. and Marko
On 21/05/12 At 11:53 AM
Weiterlesen...
When this particular variant is executed, it opens Internet Explorer with a specific page (lex.creativesandboxs.com/locker/lock.php) and prevents the user from doing anything else with the infected system. The webpage that was opened presumably showed some type of extortion message, but it's currently unavailable because the site is offline.
The most straightforward way to unlock the system is to simply delete the trojan. This can be a bit tricky since the trojan prevents doing anything with the infected system, luckily the locking itself can be easily disabled first.
Looking at the code that corresponds with a received win_unlock command, it's clear the unlock information is stored to the registry.

Unlocking can therefore be performed quite easily with a registry editor:
1. boot the system in safe mode
2. add a new key named syscheck under HKEY_CURRENT_USER
3. create a new DWORD value under the syscheck key
4. set the name of the new DWORD value to Checked
5. set the data for the Checked value to 1
6. reboot
SHA1: 03f0c26c6ba77c05152a1e0cc8bc5657f0c83119
Analysis by — Mikko S. and Marko
On 21/05/12 At 11:53 AM
Weiterlesen...
