Newsfeed
Nachrichtenbote
Do you work for a company possessing information which could be of financial value to people outside the organization? Or, perhaps even a foreign state would find it useful to gain access to the documents you're storing on that shared network drive? Yes? Then congratulations, you may already be the target of a persistent and motivated attacker (who sometimes, but rarely, is also advanced).
According to this CERT-FI presentation, even Finland has seen nearly a decade of these attacks. Nowadays, they're everywhere.
A good targeted attack case example is the one made against RSA in 2011, which our own Timo Hirvonen analyzed. This post tells the whole story of Timo looking for the original source of the infection in RSA's network, which he eventually found:
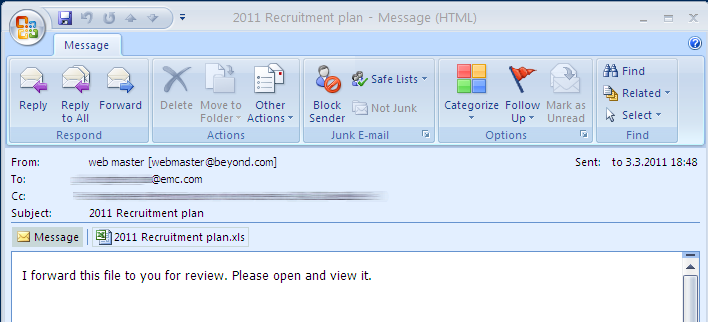
RSA was breached with a document sent as an e-mail attachment to an employee. The document contained an embedded exploit that infected the employee's computer, which gave the attacker the foothold needed to infiltrate. From that computer, they moved on to compromising the rest of the network.
Timo found the document from the files we receive via Virustotal, which is an online service where you can submit files to be scanned with several antivirus engines. The user gets to see the scanning results, thus the likelihood of maliciousness, and the file is sent to antivirus companies for further analysis. Virustotal sees hundreds of thousands of files submitted every day.
We spend a lot of effort analyzing the files submitted through Virustotal, as we want to make sure we detect anything malicious. In addition to the day-to-day malware, we also analyze the exploit documents that suspicious users submit for scanning.
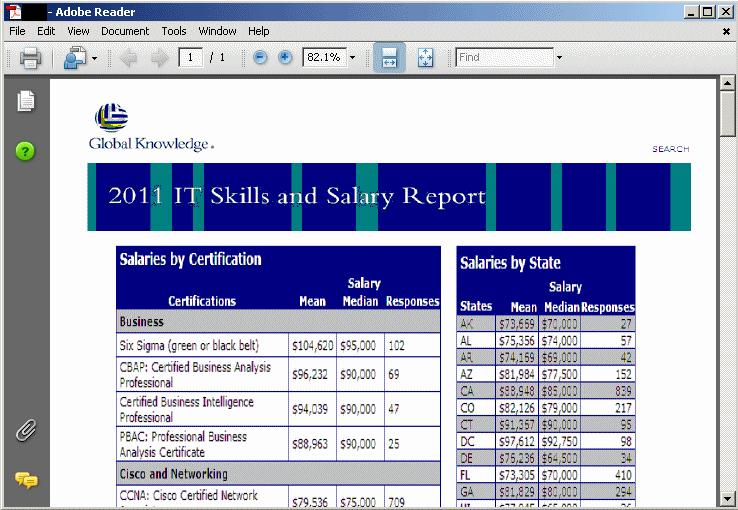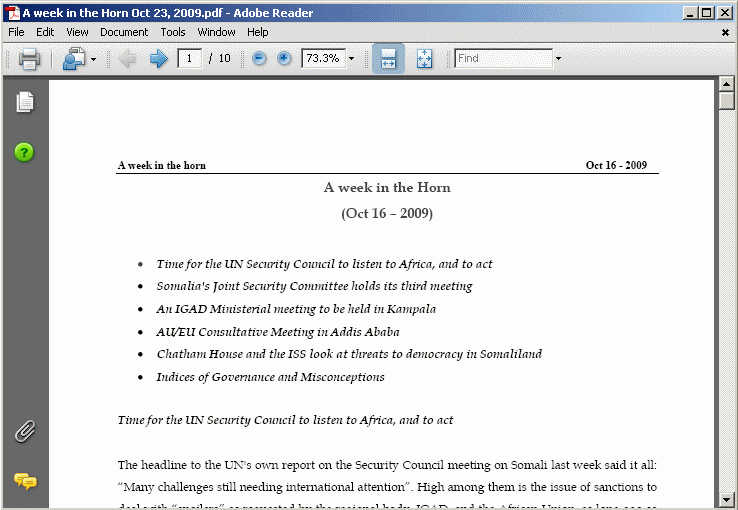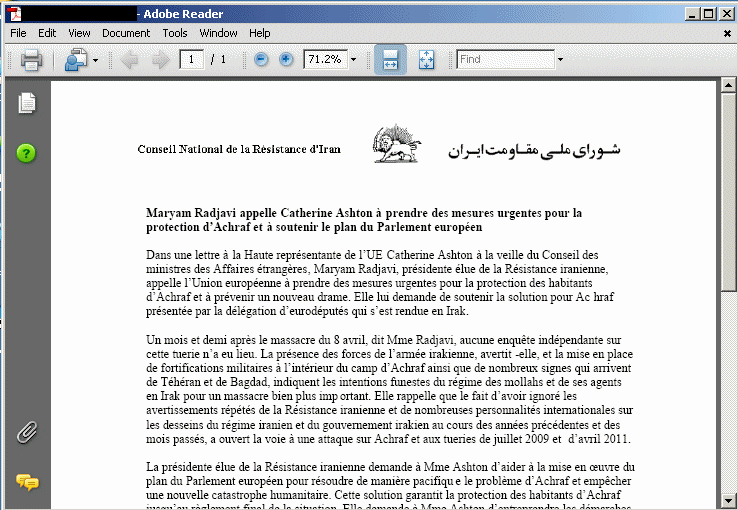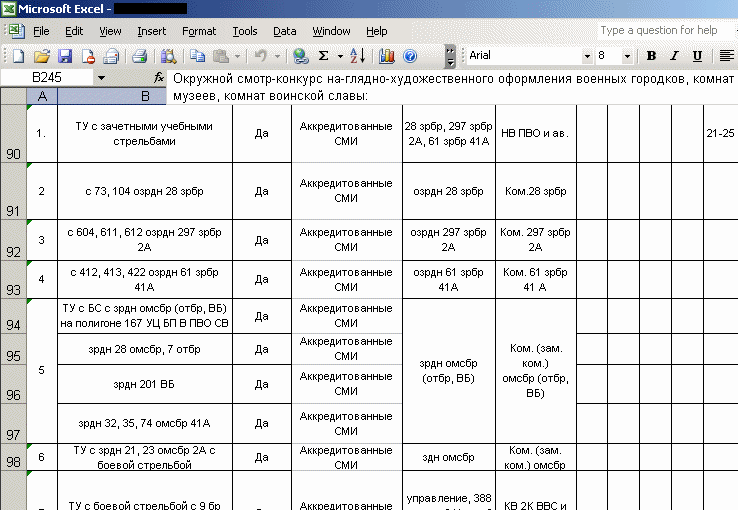
All these documents contained exploit code that would have automatically installed malware onto a user's computer had they opened them with a vulnerable document reader. They give us a small glimpse into the targets as well: who are the people that would expect to receive attachments like this?
In our latest Threat Report, Jarno Niemelä took a set these documents, extracted all the text from them and built word clouds.

The word cloud on the left is from documents we categorized as being political in theme. The one on the right is from documents we felt were corporate-themed. The clouds give you a hint of what kind of sectors are interesting to attackers.
The same tricks won't work forever, though. If you send enough e-mails with exploit attachments your targets will learn and adapt. And so we've seen new tricks in the form of "watering hole" attacks. Here's how they work: the attacker finds a website that he thinks his targets would be likely to visit. If you want to target software companies such as Twitter, Facebook or Apple, perhaps you choose a mobile development website. If you are going after government agencies, you might drop a zero-day exploit for IE8 on the US Department of Labor website. Then you simply wait for your targets to visit the site and get infected.
And then there's the good old trick with USB drives.
We don't have any information to confirm the news that the USB drives given to G20 leaders actually contained malware. If it's true, at least you can't blame the attackers for lack of optimism.
So, defending is simple: don't open e-mail attachments from your colleagues, don't browse the Internet and leave those USB drives alone. In reality, you of course have to remember many other things too. Defending against a motivated attacker is very, very difficult. You have to get everything right, every single day, while the attacker just has to find one mistake you made. The bad guys have it too easy and that's why so many of the organizations out there are under attack.
P.S. For some tips to protect against attacks like this, see the presentation Jarno Niemelä gave at Virus Bulletin this fall.
On 04/11/13 At 11:07 AM
Weiterlesen...
According to this CERT-FI presentation, even Finland has seen nearly a decade of these attacks. Nowadays, they're everywhere.
A good targeted attack case example is the one made against RSA in 2011, which our own Timo Hirvonen analyzed. This post tells the whole story of Timo looking for the original source of the infection in RSA's network, which he eventually found:

RSA was breached with a document sent as an e-mail attachment to an employee. The document contained an embedded exploit that infected the employee's computer, which gave the attacker the foothold needed to infiltrate. From that computer, they moved on to compromising the rest of the network.
Timo found the document from the files we receive via Virustotal, which is an online service where you can submit files to be scanned with several antivirus engines. The user gets to see the scanning results, thus the likelihood of maliciousness, and the file is sent to antivirus companies for further analysis. Virustotal sees hundreds of thousands of files submitted every day.
We spend a lot of effort analyzing the files submitted through Virustotal, as we want to make sure we detect anything malicious. In addition to the day-to-day malware, we also analyze the exploit documents that suspicious users submit for scanning.

All these documents contained exploit code that would have automatically installed malware onto a user's computer had they opened them with a vulnerable document reader. They give us a small glimpse into the targets as well: who are the people that would expect to receive attachments like this?
In our latest Threat Report, Jarno Niemelä took a set these documents, extracted all the text from them and built word clouds.

The word cloud on the left is from documents we categorized as being political in theme. The one on the right is from documents we felt were corporate-themed. The clouds give you a hint of what kind of sectors are interesting to attackers.
The same tricks won't work forever, though. If you send enough e-mails with exploit attachments your targets will learn and adapt. And so we've seen new tricks in the form of "watering hole" attacks. Here's how they work: the attacker finds a website that he thinks his targets would be likely to visit. If you want to target software companies such as Twitter, Facebook or Apple, perhaps you choose a mobile development website. If you are going after government agencies, you might drop a zero-day exploit for IE8 on the US Department of Labor website. Then you simply wait for your targets to visit the site and get infected.
And then there's the good old trick with USB drives.

We don't have any information to confirm the news that the USB drives given to G20 leaders actually contained malware. If it's true, at least you can't blame the attackers for lack of optimism.
So, defending is simple: don't open e-mail attachments from your colleagues, don't browse the Internet and leave those USB drives alone. In reality, you of course have to remember many other things too. Defending against a motivated attacker is very, very difficult. You have to get everything right, every single day, while the attacker just has to find one mistake you made. The bad guys have it too easy and that's why so many of the organizations out there are under attack.
P.S. For some tips to protect against attacks like this, see the presentation Jarno Niemelä gave at Virus Bulletin this fall.
On 04/11/13 At 11:07 AM
Weiterlesen...
