Newsfeed
Nachrichtenbote
Today we've published a new, quick way to check if your computer is infected by GameOver ZeuS (GOZ). Last week the GOZ botnet was disrupted by international law enforcement together with industry partners, including ourselves.
It is of critical importance to realize GOZ was disrupted — not dismantled. It's not technically impossible for the botnet administrators to reclaim control in the near future. More than one million computers are infected by GOZ, time is of the essence.
To assist with remediation, starting today, you can simply visit — www.f-secure.com/gameoverzeus — to see if your browser has signs of a GameOver ZeuS infection. The nice part is you don't have to install any software and it takes only a few seconds!
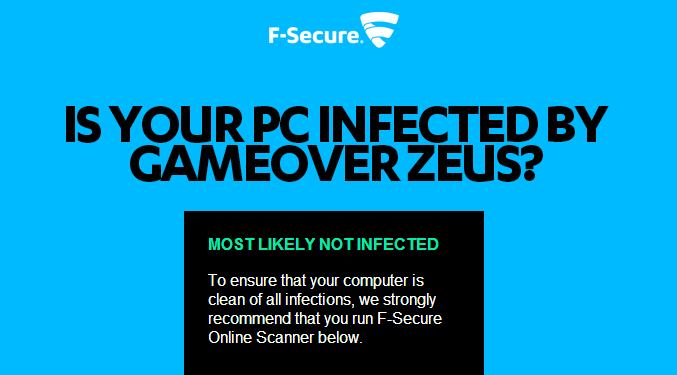
Our more technical readers might be wondering how the check works. It's something we haven't done before, and we thought we'd describe it in more detail here. In the end, we get to play a little trick on the malware itself, which is always fun.
GOZ, or in fact almost any other banking trojan for Windows, infects the browser in order to steal usernames, passwords, and other credentials. Let's say you are going into Amazon.com:
GameOver ZeuS will notice that you are about to sign in to a site it's interested in and steals your credentials straight from inside the browser. How does it do this? By including a configuration file which lists all the addresses it's interested in. Here's a partial list of what GameOver Zeus is tracking:
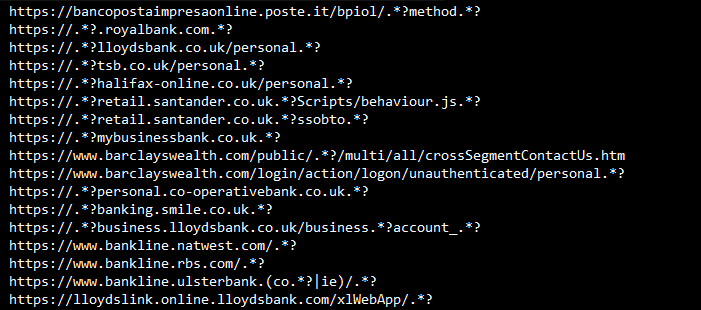
As you notice, the list contains many addresses of banks and other financial institutions. GameOver ZeuS even supports regular expressions to make creating new rules flexible. Some addresses which use regular expressions turn out to be very aggressive:

What do I mean by "aggressive"? Well, for example, visiting a site with the address https://www.f-secure.com/amazon.com/index.html would make GameOver think that you are actually visiting Amazon, because the regular expression still matches. Turns out, we can use this to "trick" GameOver bots and make an easy check to see if an infection is present in your browser!
So what does GameOver actually do when a user is going to Amazon.com? Since the malware lives inside the browser, not only can it see what you type into the login page, but it can also modify the webpage before you see it. When a user with an infected browser goes to Amazon, ZeuS will "inject" more content onto the page. Here's a partial snippet of the code which gets injected:
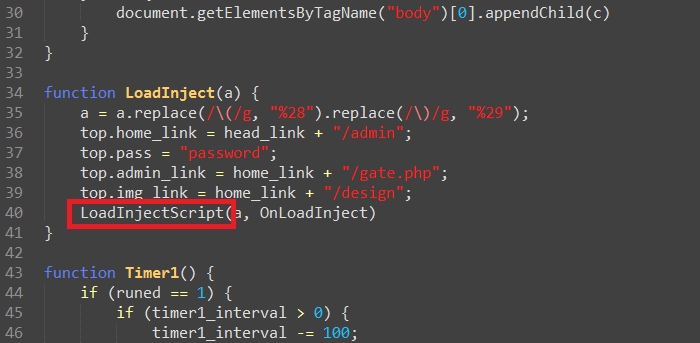
Often this extra code adds new fields to the login page and then sends the content to a server the attacker controls. We'll make use of the highlighted string ("LoadInjectScript") later.
How do we put all of this together to make a quick scan for the malware?
Our detection page at www.f-secure.com/gameoverzeus loads a webpage from an address which has the string "amazon" in it, even though it's just a page from our own site:
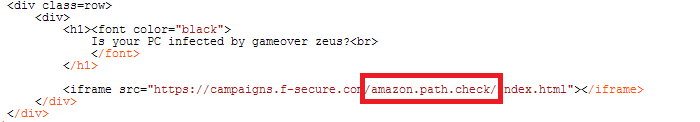
If you are infected, visiting our page makes GameOver ZeuS think you are going to Amazon, even if you're not! This in turn causes GOZ to add its own code to the webpage. When our "fake" Amazon page is loaded, it does a "self-check" and simply searches the page for the modification that GameOver makes. We search for the string "LoadInjectScript" we showed above (note that we have to split it up, so we don't just end up finding our own string!):
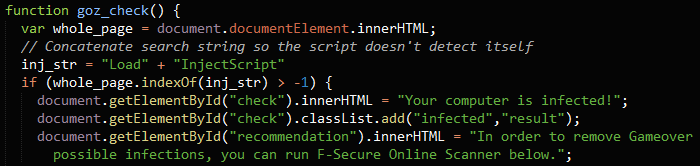
If the string is found on the page, we know GameOver ZeuS has infected your browser!
As always, there are some limitations. If you are using a browser which GameOver doesn't support (Lynx anyone?, or a native 64-bit browser), it may be that your computer is infected, but the browser has no traces of the malware. In such cases, we still recommend running our free Online Scanner to be sure. Also, if you do actually have an infection, you'll need to remove it with the scanner.
Also see US-CERT Alert (TA14-150A).
Links to share: http://www.f-secure.com/gameoverzeus — or — http://bit.ly/GOZCheck
On 09/06/14 At 06:59 AM
Weiterlesen...
It is of critical importance to realize GOZ was disrupted — not dismantled. It's not technically impossible for the botnet administrators to reclaim control in the near future. More than one million computers are infected by GOZ, time is of the essence.
To assist with remediation, starting today, you can simply visit — www.f-secure.com/gameoverzeus — to see if your browser has signs of a GameOver ZeuS infection. The nice part is you don't have to install any software and it takes only a few seconds!

Our more technical readers might be wondering how the check works. It's something we haven't done before, and we thought we'd describe it in more detail here. In the end, we get to play a little trick on the malware itself, which is always fun.
GOZ, or in fact almost any other banking trojan for Windows, infects the browser in order to steal usernames, passwords, and other credentials. Let's say you are going into Amazon.com:

GameOver ZeuS will notice that you are about to sign in to a site it's interested in and steals your credentials straight from inside the browser. How does it do this? By including a configuration file which lists all the addresses it's interested in. Here's a partial list of what GameOver Zeus is tracking:

As you notice, the list contains many addresses of banks and other financial institutions. GameOver ZeuS even supports regular expressions to make creating new rules flexible. Some addresses which use regular expressions turn out to be very aggressive:

What do I mean by "aggressive"? Well, for example, visiting a site with the address https://www.f-secure.com/amazon.com/index.html would make GameOver think that you are actually visiting Amazon, because the regular expression still matches. Turns out, we can use this to "trick" GameOver bots and make an easy check to see if an infection is present in your browser!
So what does GameOver actually do when a user is going to Amazon.com? Since the malware lives inside the browser, not only can it see what you type into the login page, but it can also modify the webpage before you see it. When a user with an infected browser goes to Amazon, ZeuS will "inject" more content onto the page. Here's a partial snippet of the code which gets injected:

Often this extra code adds new fields to the login page and then sends the content to a server the attacker controls. We'll make use of the highlighted string ("LoadInjectScript") later.
How do we put all of this together to make a quick scan for the malware?
Our detection page at www.f-secure.com/gameoverzeus loads a webpage from an address which has the string "amazon" in it, even though it's just a page from our own site:

If you are infected, visiting our page makes GameOver ZeuS think you are going to Amazon, even if you're not! This in turn causes GOZ to add its own code to the webpage. When our "fake" Amazon page is loaded, it does a "self-check" and simply searches the page for the modification that GameOver makes. We search for the string "LoadInjectScript" we showed above (note that we have to split it up, so we don't just end up finding our own string!):

If the string is found on the page, we know GameOver ZeuS has infected your browser!
As always, there are some limitations. If you are using a browser which GameOver doesn't support (Lynx anyone?, or a native 64-bit browser), it may be that your computer is infected, but the browser has no traces of the malware. In such cases, we still recommend running our free Online Scanner to be sure. Also, if you do actually have an infection, you'll need to remove it with the scanner.
Also see US-CERT Alert (TA14-150A).
Links to share: http://www.f-secure.com/gameoverzeus — or — http://bit.ly/GOZCheck
On 09/06/14 At 06:59 AM
Weiterlesen...
