Newsfeed
Nachrichtenbote
The rather pathetic story of Andrew Auernheimer, a.k.a. Weev, took another step yesterday when the unrepentant Internet troll was sentenced to 41 months in (U.S.) prison for one count of identity fraud and one count of unauthorized computer access.
We've posted about Weev in the past: Free Weev. Free Weev?
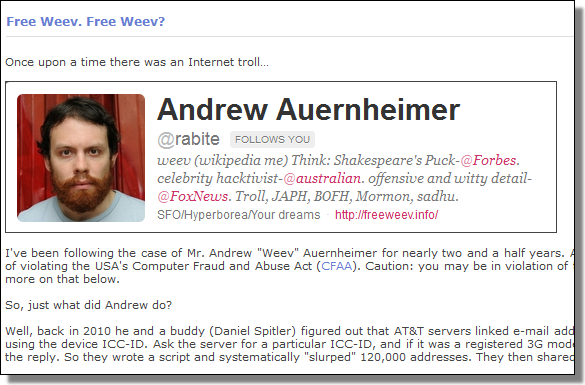
Much of today's press coverage (and Twitter reaction) is singularly focused on the Computer Fraud and Abuse Act (CFAA) — which is the (vaguely written) law related to the count of unauthorized access.
Some folks are voicing concern that Weev's sentencing will have a "chilling effect" on security research.
But not to worry!
Almost all of the coverage we've seen really fails to consider the charge of identity fraud.
So here's a handy how-to guide on avoiding trouble when disclosing a security flaw:
1. Don't be anasshole troll.
2. When you discover a flaw, don't abuse it. Only do enough to demonstrate the problem, no more.
3. Don't collect, record, and then transmit personally identifiable information (PII) belonging to other people.
4. When contacting reporters, have them volunteer their own device IDs to demonstrate the flaw.
Simple.
On 19/03/13 At 12:24 PM
Weiterlesen...
We've posted about Weev in the past: Free Weev. Free Weev?

Much of today's press coverage (and Twitter reaction) is singularly focused on the Computer Fraud and Abuse Act (CFAA) — which is the (vaguely written) law related to the count of unauthorized access.
Some folks are voicing concern that Weev's sentencing will have a "chilling effect" on security research.
But not to worry!
Almost all of the coverage we've seen really fails to consider the charge of identity fraud.
So here's a handy how-to guide on avoiding trouble when disclosing a security flaw:
1. Don't be an
2. When you discover a flaw, don't abuse it. Only do enough to demonstrate the problem, no more.
3. Don't collect, record, and then transmit personally identifiable information (PII) belonging to other people.
4. When contacting reporters, have them volunteer their own device IDs to demonstrate the flaw.
Simple.
On 19/03/13 At 12:24 PM
Weiterlesen...
