Newsfeed
Nachrichtenbote
We've been seeing cases of malware that first debuted on other operating systems being ported over to Android. Here's another trojan that fits the bill.
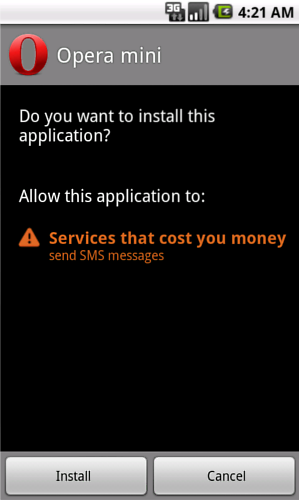
Opfake was first found on Symbian and Windows Mobile. In its latest incarnation on Android, the trojan (still) appears to be an Opera Mini app...whose only permission request is to send SMS messages:
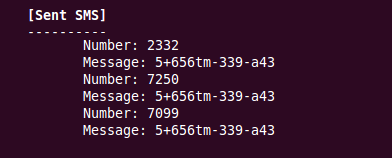
Turns out the app (we detect it as Trojan:Android/OpFake.D) sends the messages on launch:
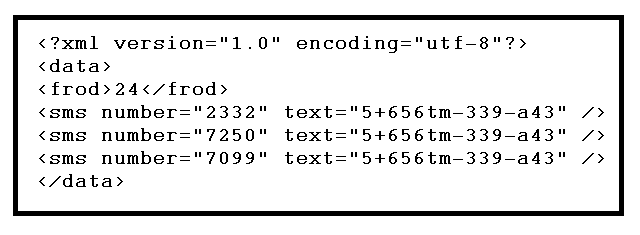
In previous cases, we usually saw these SMS messages hard-coded into the classes; this time, the message contents and telephone numbers are stored in a 'config.xml' file and are encoded. Here's the garbled code:

The string becomes readable when decoded using base64 decoding, showing the SMS messages sent by the app on execution:
This Android version (SHA1: 4b4af6d0dfb797f66edd9a8c532dc59e66777072) simply continues the opFake 'tradition' of encoding its configuration files, so by itself, that's not new. It does however fit into a current trend of Android malware increasingly using encoding, encryption and other techniques (which have been standard for years on other platform) to hide its code or actions from analysis.
ThreatSolutions post by - Irene
On 31/01/12 At 07:28 AM
Weiterlesen...
Opfake was first found on Symbian and Windows Mobile. In its latest incarnation on Android, the trojan (still) appears to be an Opera Mini app...whose only permission request is to send SMS messages:

Turns out the app (we detect it as Trojan:Android/OpFake.D) sends the messages on launch:

In previous cases, we usually saw these SMS messages hard-coded into the classes; this time, the message contents and telephone numbers are stored in a 'config.xml' file and are encoded. Here's the garbled code:

The string becomes readable when decoded using base64 decoding, showing the SMS messages sent by the app on execution:

This Android version (SHA1: 4b4af6d0dfb797f66edd9a8c532dc59e66777072) simply continues the opFake 'tradition' of encoding its configuration files, so by itself, that's not new. It does however fit into a current trend of Android malware increasingly using encoding, encryption and other techniques (which have been standard for years on other platform) to hide its code or actions from analysis.
ThreatSolutions post by - Irene
On 31/01/12 At 07:28 AM
Weiterlesen...
