Newsfeed
Nachrichtenbote
On Tuesday, Facebook Security announced its new effort to make malware cleanup easier. And we're very happy to be part of that effort. F-Secure is one of two vendors now partnered with Facebook do to malware clean-up.
With over one billion users, Facebook has a very unique vantage point from which to detect threats. It can see patterns on a scale few others can. And user accounts pumping spam links that have uncommon browser plugins installed… well, those accounts are connecting from computers affected by malware. So what to do about it?
That's where we come in…
When Facebook determines a case of Facebook-focused malware, it introduces this prompt during login:
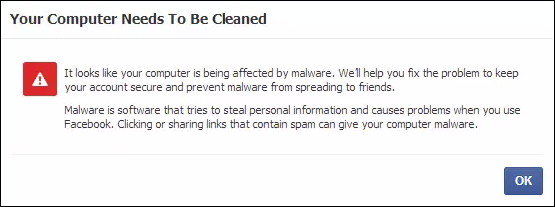
The user then has the option to download our Online Scanner:
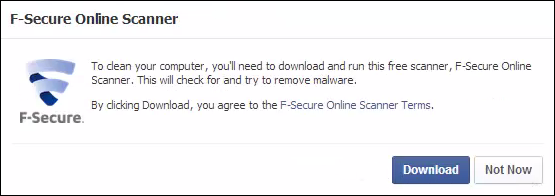
Once downloaded and started, the user can continue to their Facebook feed.
Our scanner runs in the background and produces a Facebook notification when it's finished.
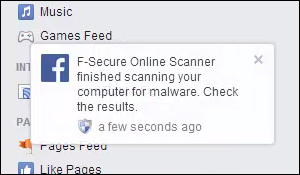
While Facebook-focused malware is the trigger which prompts the scan, our scanner will of course detect more threats if present. If a difficult case is discovered, Facebook will move our UI into the foreground.
"Chanki" — our service manager for this project — makes the following observations:
1 — There are a tremendous amount of suspect installers out there, which while not necessarily malicious, are difficult to classify as clean by default. Separating the wheat from the chaff is a challenge when installers can be configured to install multiple items utilizing a common platform that also has legitimate uses.
2 — We also needed to come up with approaches for handling the classification, detection and removal of malicious browser extensions on Firefox and Chrome, which represent a significant attack vector against Facebook's platform. This is typified by families such as the Turkish-oriented Kilim malware, and older attacks such as FBSuper which we have previously written about on this blog. The attack surface is not just Win32 OS; we have to take into account the platforms represented by the browsers as well.
3 — We also discovered that Bitcoin remains a significant motivation for malware authors. We identified at least two malware families, Napolar and Lecpetex, that utilize Facebook as a vector to spread and install Bitcoin miners.
Great work, Chanki!
You don't need to be prompted by Facebook to try our Online Scanner. Feel free to download and run it yourself. Add it to your USB toolkit, it needs online access for our latest detections, it isn't Web-based. If complex threats are discovered, the scanner includes neat tech such as an ability to reboot into a virtual Linux machine and then back to Windows. Nice.

You'll always find the latest version here: f-secure.com/online-scanner
On 21/05/14 At 12:42 PM
Weiterlesen...
With over one billion users, Facebook has a very unique vantage point from which to detect threats. It can see patterns on a scale few others can. And user accounts pumping spam links that have uncommon browser plugins installed… well, those accounts are connecting from computers affected by malware. So what to do about it?
That's where we come in…
When Facebook determines a case of Facebook-focused malware, it introduces this prompt during login:

The user then has the option to download our Online Scanner:

Once downloaded and started, the user can continue to their Facebook feed.
Our scanner runs in the background and produces a Facebook notification when it's finished.

While Facebook-focused malware is the trigger which prompts the scan, our scanner will of course detect more threats if present. If a difficult case is discovered, Facebook will move our UI into the foreground.
"Chanki" — our service manager for this project — makes the following observations:
1 — There are a tremendous amount of suspect installers out there, which while not necessarily malicious, are difficult to classify as clean by default. Separating the wheat from the chaff is a challenge when installers can be configured to install multiple items utilizing a common platform that also has legitimate uses.
2 — We also needed to come up with approaches for handling the classification, detection and removal of malicious browser extensions on Firefox and Chrome, which represent a significant attack vector against Facebook's platform. This is typified by families such as the Turkish-oriented Kilim malware, and older attacks such as FBSuper which we have previously written about on this blog. The attack surface is not just Win32 OS; we have to take into account the platforms represented by the browsers as well.
3 — We also discovered that Bitcoin remains a significant motivation for malware authors. We identified at least two malware families, Napolar and Lecpetex, that utilize Facebook as a vector to spread and install Bitcoin miners.
Great work, Chanki!
You don't need to be prompted by Facebook to try our Online Scanner. Feel free to download and run it yourself. Add it to your USB toolkit, it needs online access for our latest detections, it isn't Web-based. If complex threats are discovered, the scanner includes neat tech such as an ability to reboot into a virtual Linux machine and then back to Windows. Nice.

You'll always find the latest version here: f-secure.com/online-scanner
On 21/05/14 At 12:42 PM
Weiterlesen...
