Newsfeed
Nachrichtenbote
Regin is the latest in the line of sophisticated espionage toolkits used to target a range of organizations around the world. As already reported, it's one of the more complex pieces of malware around, and just like many of the other toolkits it also has a long history behind it. We first encountered Regin nearly six years ago in early 2009, when we found it hiding on a Windows server in a customer environment in Northern Europe.
The server had shown symptoms of trouble, as it had been occasionally crashing with the infamous Blue Screen of Death. A driver with an innocuous name of "pciclass.sys" seemed to be causing the crashes. Upon closer analysis it was obvious that the driver was in fact a rootkit, more precisely one of the early variants of Regin.
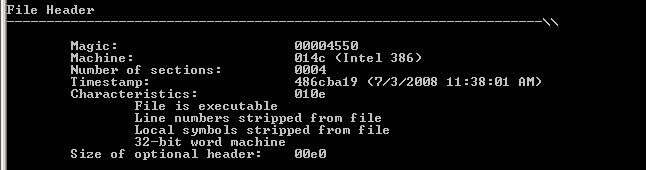
As can be seen from the screenshot above, the driver was apparently compiled already on 7th of March 2008, but other samples with earlier timestamps indicate that the campaign is even older than this.
The driver turned out to be just one component of a multi-stage threat. The embedded configuration in the driver showed it could use either a registry key or the NTFS filesystem Extended Attributes to load the next stage of the malware.
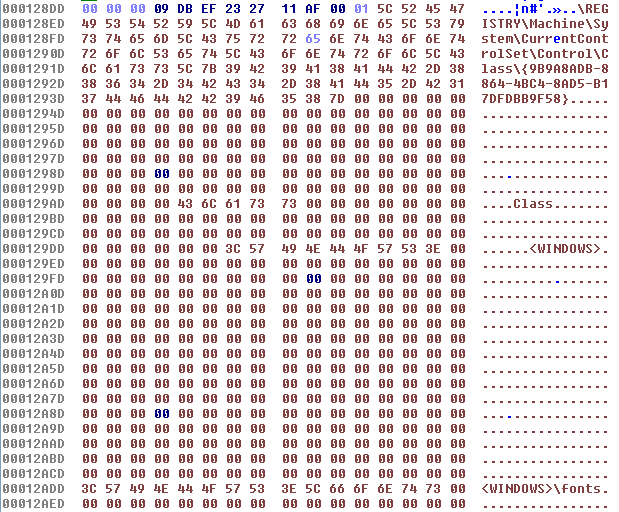
We've seen at least the following registry keys being used for the next stage payload:
• \REGISTRY\Machine\System\CurrentControlSet\Control\Class\{9B9A8ADB-8864-4BC4-8AD5-B17DFDBB9F58}:Class
• \REGISTRY\Machine\System\CurrentControlSet\Control\Class\{4F20E605-9452-4787-B793-D0204917CA58}:Class
• \REGISTRY\Machine\System\CurrentControlSet\Control\RestoreList:VideoBase
The following folders containing an NTFS Extended Attribute with the name "_" have also been seen to store the next stage payload, which can actually be split between two different attributes:
• %WINDIR%
• %WINDIR%\security
• %WINDIR%\repair
• %WINDIR%\msapps
• %WINDIR%\msagent
• %WINDIR%\Cursors
• %WINDIR%\fonts
• %WINDIR%\Temp
• %WINDIR%\msagent\chars
• %WINDIR%\Help
• %WINDIR%\inf
• %WINDIR%\Spool\Printers
• %WINDIR%\CertSrv
During 2013 and 2014, as we have been analyzing the later versions of Regin, the complexity and the level of sophistication in the attacks has become very evident. We would place Regin in the same category of highly sophisticated espionage campaigns together with the likes of Stuxnet, Flame, and Turla/Snake.
As always, attribution is difficult with cases like this. Our belief is that this malware, for a change, isn't coming from Russia or China.
On 23/11/14 At 10:54 PM
Weiterlesen...
The server had shown symptoms of trouble, as it had been occasionally crashing with the infamous Blue Screen of Death. A driver with an innocuous name of "pciclass.sys" seemed to be causing the crashes. Upon closer analysis it was obvious that the driver was in fact a rootkit, more precisely one of the early variants of Regin.

As can be seen from the screenshot above, the driver was apparently compiled already on 7th of March 2008, but other samples with earlier timestamps indicate that the campaign is even older than this.
The driver turned out to be just one component of a multi-stage threat. The embedded configuration in the driver showed it could use either a registry key or the NTFS filesystem Extended Attributes to load the next stage of the malware.

We've seen at least the following registry keys being used for the next stage payload:
• \REGISTRY\Machine\System\CurrentControlSet\Control\Class\{9B9A8ADB-8864-4BC4-8AD5-B17DFDBB9F58}:Class
• \REGISTRY\Machine\System\CurrentControlSet\Control\Class\{4F20E605-9452-4787-B793-D0204917CA58}:Class
• \REGISTRY\Machine\System\CurrentControlSet\Control\RestoreList:VideoBase
The following folders containing an NTFS Extended Attribute with the name "_" have also been seen to store the next stage payload, which can actually be split between two different attributes:
• %WINDIR%
• %WINDIR%\security
• %WINDIR%\repair
• %WINDIR%\msapps
• %WINDIR%\msagent
• %WINDIR%\Cursors
• %WINDIR%\fonts
• %WINDIR%\Temp
• %WINDIR%\msagent\chars
• %WINDIR%\Help
• %WINDIR%\inf
• %WINDIR%\Spool\Printers
• %WINDIR%\CertSrv
During 2013 and 2014, as we have been analyzing the later versions of Regin, the complexity and the level of sophistication in the attacks has become very evident. We would place Regin in the same category of highly sophisticated espionage campaigns together with the likes of Stuxnet, Flame, and Turla/Snake.
As always, attribution is difficult with cases like this. Our belief is that this malware, for a change, isn't coming from Russia or China.
On 23/11/14 At 10:54 PM
Weiterlesen...
