Newsfeed
Nachrichtenbote
A little over two weeks ago, we found a new family of Android ransomware: SLocker.
We have no evidence that SLocker is related to Koler, the most recently discovered Android ransomware. It does however carry through on the threat Koler made. Unlike Koler — which pretended to, but didn't actually encrypt files — SLocker will actually scan the device's SD card for specific file types:
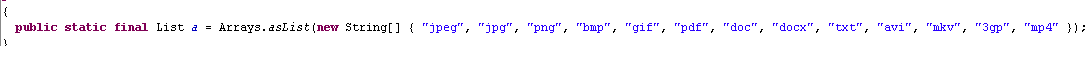
When the SLocker app is launched, it encrypts these files and then displays a ransom message:

The message informs the user they must transfer a payment via an online money transfer service in order to recover the files. The phone number listed in the message on the left is based in Ukraine.
Currently there are two versions of this family. The first version uses the TOR anonymizing network to communicate between infected phones and the malware's C&C-server. We suspect this version might be a testing revision because all debug information is available.
The second SLocker version appeared at the same time as the TOR-enabled version but is simplified. This version shares much the same code (including encryption and the same hardcoded decryption key) but the debugging parts are no longer present. The main difference though is that this version doesn't use TOR. Instead, it takes its commands via SMS messages:
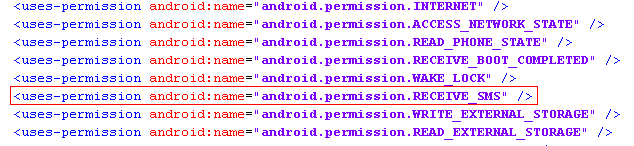
Also notable is that unlike the TOR-enabled version, this one lists a Russian phone number and demands Russian currency in the ransom message:
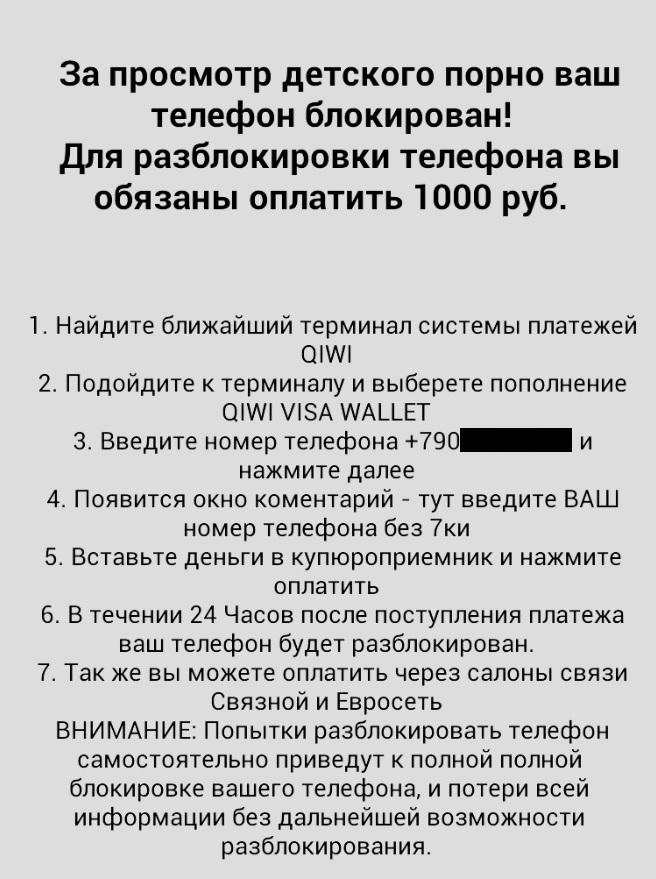
Digging deeper into retracing the C&C server, we found its IP address had been registered as far back to 2005 to a private person. Currently, a Russian-based webhosting service is running there.
Though this version of SLocker is less sophisticated in that it does not use TOR for its C&C communications, it still seems to be under active development, as the latest sample we have of this version now includes capability to take photographs using the device's camera. It seems likely that SLocker's author(s) will continue to develop it in the future.
—————
Post by — Mikko Hyykoski
On 16/06/14 At 07:10 AM
Weiterlesen...
We have no evidence that SLocker is related to Koler, the most recently discovered Android ransomware. It does however carry through on the threat Koler made. Unlike Koler — which pretended to, but didn't actually encrypt files — SLocker will actually scan the device's SD card for specific file types:
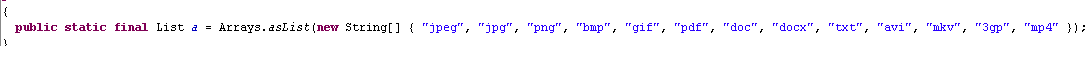
When the SLocker app is launched, it encrypts these files and then displays a ransom message:

The message informs the user they must transfer a payment via an online money transfer service in order to recover the files. The phone number listed in the message on the left is based in Ukraine.
Currently there are two versions of this family. The first version uses the TOR anonymizing network to communicate between infected phones and the malware's C&C-server. We suspect this version might be a testing revision because all debug information is available.
The second SLocker version appeared at the same time as the TOR-enabled version but is simplified. This version shares much the same code (including encryption and the same hardcoded decryption key) but the debugging parts are no longer present. The main difference though is that this version doesn't use TOR. Instead, it takes its commands via SMS messages:
Also notable is that unlike the TOR-enabled version, this one lists a Russian phone number and demands Russian currency in the ransom message:

Digging deeper into retracing the C&C server, we found its IP address had been registered as far back to 2005 to a private person. Currently, a Russian-based webhosting service is running there.
Though this version of SLocker is less sophisticated in that it does not use TOR for its C&C communications, it still seems to be under active development, as the latest sample we have of this version now includes capability to take photographs using the device's camera. It seems likely that SLocker's author(s) will continue to develop it in the future.
—————
Post by — Mikko Hyykoski
On 16/06/14 At 07:10 AM
Weiterlesen...
