Newsfeed
Nachrichtenbote
We get a lot of samples here at F-Secure Labs, most of them being submitted online. But every now and then, somebody visits one of our labs and brings along their computer for forensics.
Earlier this year, a guy in his early 20's pulled up and parked his Audi R8 just outside our Helsinki HQ. His name is Jens Kyllönen — a professional poker player — both in real world tournaments and in the online poker world. He's a high-roller by any measure, with wins in the range of 2.5 million dollars from the past year.

So why would this poker star detour from his usual routine and drop by for a visit? This is his story…
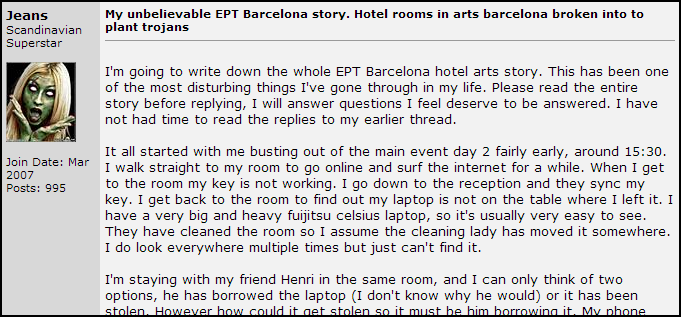
Last September, Jens participated in the European Poker Tour event in Barcelona. He was staying at the event hotel, which is a 5-star location, and spent his day mostly at the tournament tables. He took a break from the tournament and went to his room. And his laptop wasn't there. He checked to see if his friend had borrowed it, no, and then when he returned to his room… his laptop was back. He knew that something was amiss. To add to his suspicion, the OS, Windows, didn't boot properly.
Jens provided a more detailed scenario of what happened that day in this forum:
Thinking he had possibly been compromised, Jens asked us to investigate his laptop. This is quite important, as laptop security is paramount for professional poker players, especially those who play online. We agreed to investigate, and so we made full forensic images and started digging.
After a while, it was obvious that his hunch was correct, the laptop was indeed infected. There was a Remote Access Trojan (RAT) with timestamps coinciding with the time when the laptop had gone missing. Apparently, the attacker installed the trojan from a USB memory stick and configured it to automatically start at every reboot. A RAT, by the way, is a common tool that allows an attacker to control and monitor a laptop remotely, viewing anything that happens on the machine.
Below are succeeding screenshots to give you a better view on how this particular RAT works. In this screenshot, the attacker is able to see his own cards, similar to what any other players would experience.
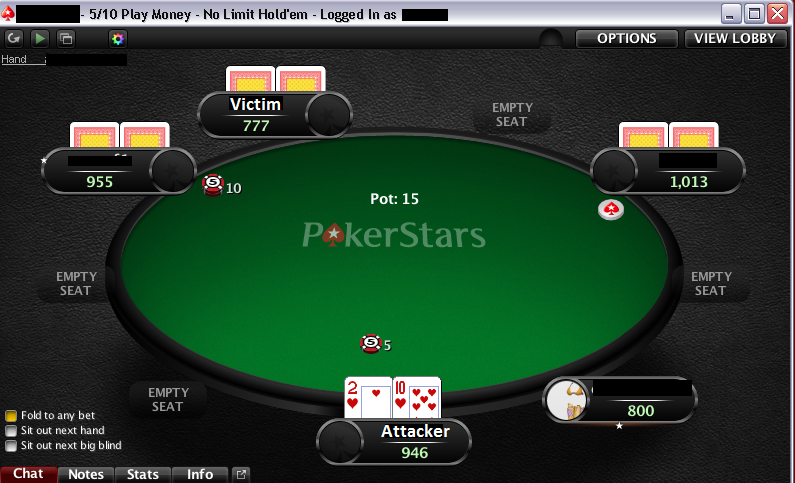
Using the trojan, however, he can also see that the infected machine or the victim is holding a pair of queens. This gives the attacker an edge, so he knows to hold out for a better hand.
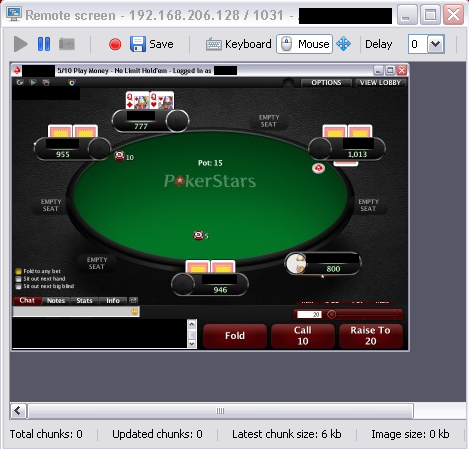
This kind of attack is very generic and works against any online poker site that we know of.
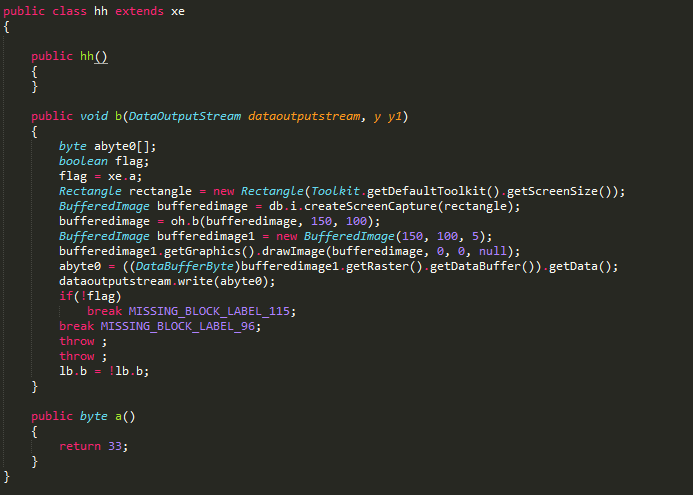
The trojan is written in Java and uses obfuscation, but isn't all that complicated. Since it's in Java, the malware can run in any platform (Mac OS, Windows, Linux). Here is a snippet of the code that takes screenshots of the victim's screen:
After analyzing Jens's laptop, we started looking for other victims. It turned out that yet another professional player, Henri Jaakkola, who stayed in the same room as Jens at the EPT Barcelona event, had the exact same trojan installed in his laptop.
This is not the first time professional poker players have been targeted with tailor-made trojans. We have investigated several cases that have been used to steal hundreds of thousands of euro. What makes these cases noteworthy is that they were not online attacks. The attacker went through the trouble of targeting the victims' systems on site.
(An Evil Maid Attack.)
The phenomenon is now big enough that we think it warrants its own name: Sharking. Sharking attacks are targeted attacks against professional poker players (a.k.a. poker sharks). It's similar to Whaling attacks which are targeted at high profile business managers.
So, what's the moral of the story? If you have a laptop that is used to move large amounts of money, take good care of it. Lock the keyboard when you step away. Put it in a safe when you're not around it, and encrypt the disk to prevent off-line access. Don't surf the web with it (use another laptop/device for that, they're relatively cheap). This advice is true whether you're a poker pro using a laptop for gaming or a business controller in a large company using the computer for wiring a large amount of funds.
—————
Analysis and post by — Daavid and Antti
On 10/12/13 At 12:15 PM
Weiterlesen...
Earlier this year, a guy in his early 20's pulled up and parked his Audi R8 just outside our Helsinki HQ. His name is Jens Kyllönen — a professional poker player — both in real world tournaments and in the online poker world. He's a high-roller by any measure, with wins in the range of 2.5 million dollars from the past year.

So why would this poker star detour from his usual routine and drop by for a visit? This is his story…
Last September, Jens participated in the European Poker Tour event in Barcelona. He was staying at the event hotel, which is a 5-star location, and spent his day mostly at the tournament tables. He took a break from the tournament and went to his room. And his laptop wasn't there. He checked to see if his friend had borrowed it, no, and then when he returned to his room… his laptop was back. He knew that something was amiss. To add to his suspicion, the OS, Windows, didn't boot properly.
Jens provided a more detailed scenario of what happened that day in this forum:

Thinking he had possibly been compromised, Jens asked us to investigate his laptop. This is quite important, as laptop security is paramount for professional poker players, especially those who play online. We agreed to investigate, and so we made full forensic images and started digging.
After a while, it was obvious that his hunch was correct, the laptop was indeed infected. There was a Remote Access Trojan (RAT) with timestamps coinciding with the time when the laptop had gone missing. Apparently, the attacker installed the trojan from a USB memory stick and configured it to automatically start at every reboot. A RAT, by the way, is a common tool that allows an attacker to control and monitor a laptop remotely, viewing anything that happens on the machine.
Below are succeeding screenshots to give you a better view on how this particular RAT works. In this screenshot, the attacker is able to see his own cards, similar to what any other players would experience.

Using the trojan, however, he can also see that the infected machine or the victim is holding a pair of queens. This gives the attacker an edge, so he knows to hold out for a better hand.

This kind of attack is very generic and works against any online poker site that we know of.
The trojan is written in Java and uses obfuscation, but isn't all that complicated. Since it's in Java, the malware can run in any platform (Mac OS, Windows, Linux). Here is a snippet of the code that takes screenshots of the victim's screen:

After analyzing Jens's laptop, we started looking for other victims. It turned out that yet another professional player, Henri Jaakkola, who stayed in the same room as Jens at the EPT Barcelona event, had the exact same trojan installed in his laptop.
This is not the first time professional poker players have been targeted with tailor-made trojans. We have investigated several cases that have been used to steal hundreds of thousands of euro. What makes these cases noteworthy is that they were not online attacks. The attacker went through the trouble of targeting the victims' systems on site.
(An Evil Maid Attack.)
The phenomenon is now big enough that we think it warrants its own name: Sharking. Sharking attacks are targeted attacks against professional poker players (a.k.a. poker sharks). It's similar to Whaling attacks which are targeted at high profile business managers.
So, what's the moral of the story? If you have a laptop that is used to move large amounts of money, take good care of it. Lock the keyboard when you step away. Put it in a safe when you're not around it, and encrypt the disk to prevent off-line access. Don't surf the web with it (use another laptop/device for that, they're relatively cheap). This advice is true whether you're a poker pro using a laptop for gaming or a business controller in a large company using the computer for wiring a large amount of funds.
—————
Analysis and post by — Daavid and Antti
On 10/12/13 At 12:15 PM
Weiterlesen...
