Newsfeed
Nachrichtenbote
Journalist John Leyden recently contacted us for our opinion on vulnerability research by Tom Forbes. The focus of Forbes' research was Dell's "System Detect" utility and a flaw that allows for remote code execution. Forbes reported his findings last November and Dell mitigated the issue in January (and also again last week).
But a significant problem remains from our point of view.
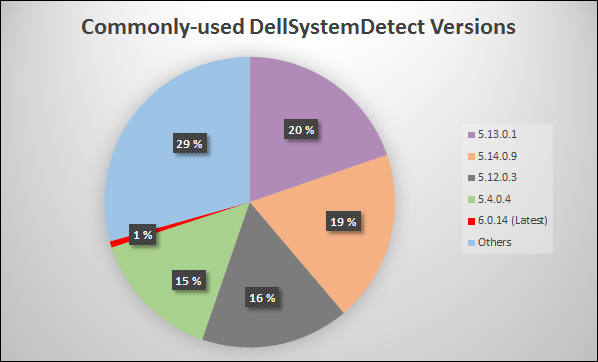
Older versions of the software don't update themselves and there remains a lot of vulnerable computers out there. Over time, our customers have scanned various versions of System Detect many hundreds of thousands of times. It's very prevalent software. From just our customer base statistics within the last two weeks, we can see approximately 100,000 customers queried reputation checks on System Detect. Only about one percent of our customers are now running the latest version (6.0.14, represented by red in the chart below).
Older versions of System Detect create a run key in the registry that starts the service automatically. So vulnerable versions run persistently even though it's only needed when visiting Dell's support site. The latest version — 6.0.14 — doesn't create a run key.
Exploiting older versions of System Detect is very easy. It only requires that the target visits a URL with some variation of "dell" in its domain. Exactly where in the URL varies depending on the version of the software.
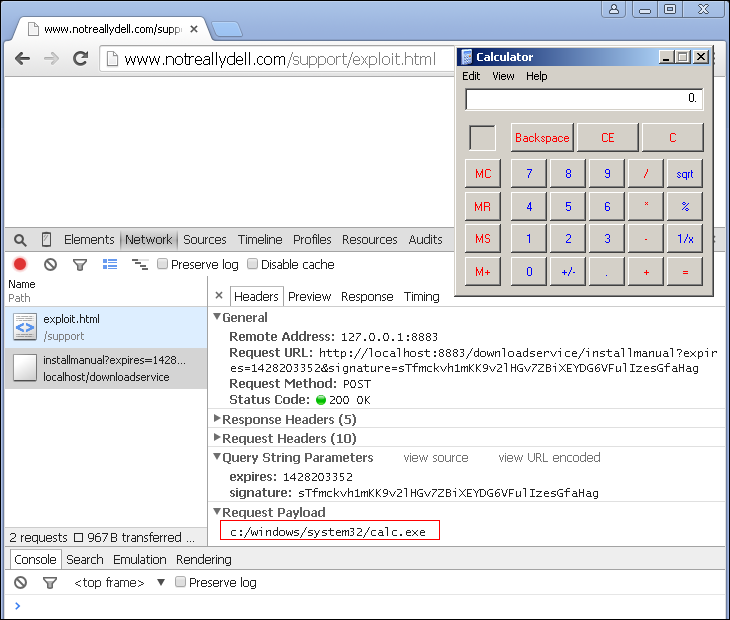
We used Forbe's research and our own black-box testing to run three versions of System Detect, observing network traffic and replaying the same traffic with small modifications. We confirmed the older versions can be used to launch calc.exe from a targeted machine (i.e., Remote Code Execution).
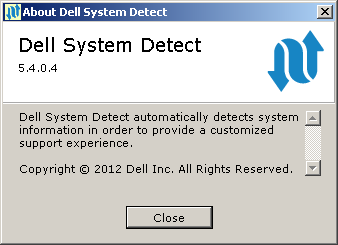
For the 5.4.0.4 version, the domain part of the referer-field's URL needs to contain "dell.com" but it accepts also "www.notreallydell.com", so it's highly vulnerable.
Version 6.0.9 was released after Forbes reported the issue to Dell. It requires that the domain contains ".dell.". This means it also accepts "a.dell.fakesite.ownedbythebadguys.com", so it's also just as vulnerable to a web-based attack.
The current version, 6.0.14, requires that the domain is "*.dell.com" which more or less addresses the problem, especially when combined with the lack of autostart. If you need to have a version installed, it should be this one.
Older versions should definitely be uninstalled as soon as possible.

Here's an HTTPS enabled download link.
We are continuing to investigate further issues and actions that may be necessary to protect our customers.
On 02/04/15 At 12:53 PM
Weiterlesen...
But a significant problem remains from our point of view.
Older versions of the software don't update themselves and there remains a lot of vulnerable computers out there. Over time, our customers have scanned various versions of System Detect many hundreds of thousands of times. It's very prevalent software. From just our customer base statistics within the last two weeks, we can see approximately 100,000 customers queried reputation checks on System Detect. Only about one percent of our customers are now running the latest version (6.0.14, represented by red in the chart below).

Older versions of System Detect create a run key in the registry that starts the service automatically. So vulnerable versions run persistently even though it's only needed when visiting Dell's support site. The latest version — 6.0.14 — doesn't create a run key.
Exploiting older versions of System Detect is very easy. It only requires that the target visits a URL with some variation of "dell" in its domain. Exactly where in the URL varies depending on the version of the software.
We used Forbe's research and our own black-box testing to run three versions of System Detect, observing network traffic and replaying the same traffic with small modifications. We confirmed the older versions can be used to launch calc.exe from a targeted machine (i.e., Remote Code Execution).

For the 5.4.0.4 version, the domain part of the referer-field's URL needs to contain "dell.com" but it accepts also "www.notreallydell.com", so it's highly vulnerable.

Version 6.0.9 was released after Forbes reported the issue to Dell. It requires that the domain contains ".dell.". This means it also accepts "a.dell.fakesite.ownedbythebadguys.com", so it's also just as vulnerable to a web-based attack.
The current version, 6.0.14, requires that the domain is "*.dell.com" which more or less addresses the problem, especially when combined with the lack of autostart. If you need to have a version installed, it should be this one.
Older versions should definitely be uninstalled as soon as possible.

Here's an HTTPS enabled download link.
We are continuing to investigate further issues and actions that may be necessary to protect our customers.
On 02/04/15 At 12:53 PM
Weiterlesen...
