Newsfeed
Nachrichtenbote
Lately, our eyes have been caught by the rise of Ransomware families. It is very evident that the bad guys are constantly developing this type of malware family as seen in our previous posts about CryptoWall and CTB-Locker and Synolocker. In addition to these families, we have also been observing a rather simpler type of Ransomware, yet pretty active and very much alive since it was first encountered in 2013 - Browlock.
Compared to other Ransomware families, Browlock does not encrypt the victim's files, and does not add nor run any files on the victim's machine. It only scares the user by locking the browser with an alert that claims to be from the police or authorities, stating that the victim has committed a crime by viewing child pornography website or downloading pirated software. It prevents the user from closing the browser, but terminating the browser process using task manager, for example, resolves the problem.
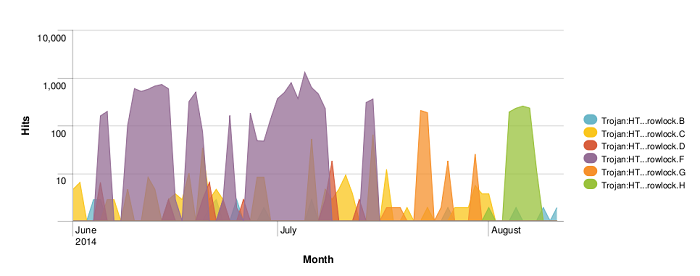
The following are statistics taken from Browlock hits in our telemetry from June onwards.
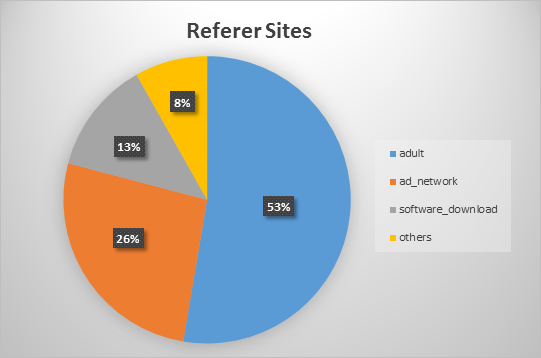
According to our statistics, the target victims were users visiting adult sites. More than half of them were redirected to Browlock pages after going to adult-related websites. Others were redirected through the use of ad networks. We didnt notice any adult website that stood out from our data, however, for the ad networks percentage, almost 60% were from trafficbroker.com alone.
Browlock's landing pages have different IPs and URLs from time to time. You may see more observation of this from malekals website . The URLs may look random, however it has noticeable patterns. Below are some examples:
• http:// alert. policecoin. info/ FI/cls.php
• http:// alert. porschepolice. net/ FI/cls.php
• http:// alert. xraypolice. com/ FI/cls.php
• http:// alert-police. barbrastreisandagent. com/
• http:// alert-police. estateagentsolutions. net/
• http:// attention.starpolice. biz/FI/cls.php
• http:// attention.starpolice. co/FI/cls.php
• http:// police. grantscards. com/
• http:// police. redunderground. com/
• http:// security-scan-nuqbqakx. in/
• http:// security-scan-jdytiujg. in/
• http:// system-check-abevbrye. in/
• http:// system-check-ipxmjdry. in/
• http:// security-akechksv-check. in/
• http:// security-zxqkcohl-chk. in/
• http:// law-enforcement-tqvrlbqb. in/
• http:// law-enforcement-icgkjyrr. in/
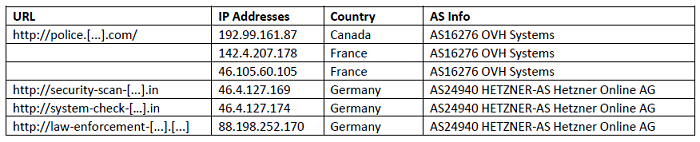
From the month of June, we have observed the following most reported URLs in our upstream, with its corresponding IPs where it is hosted:
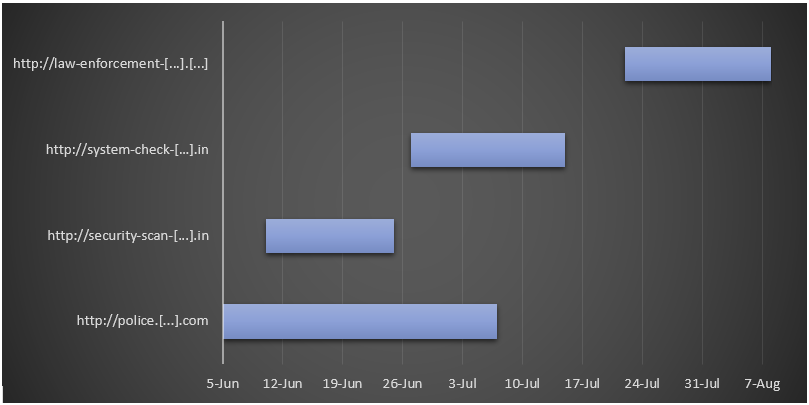
The graph below shows the duration of these URL patterns being actively reported in our upstream. It seems that on average, Browlock was able to keep a single URL pattern of its landing pages for about two weeks to a month long.
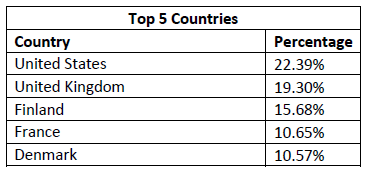
We have also noticed that United States, United Kingdom, and countries in Europe were the most affected.
Weve seen this operation going on for quite a while now, wondering if the bad guys are really getting money from this very simple mechanism. We dont really know for sure how many victims have given in into paying a ransom from its fake alert message. But what we know for sure, is that while we see this ransomware families being active, we will keep our eyes open to keep protecting our customers from this threat.
On 15/08/14 At 02:51 PM
Weiterlesen...
Compared to other Ransomware families, Browlock does not encrypt the victim's files, and does not add nor run any files on the victim's machine. It only scares the user by locking the browser with an alert that claims to be from the police or authorities, stating that the victim has committed a crime by viewing child pornography website or downloading pirated software. It prevents the user from closing the browser, but terminating the browser process using task manager, for example, resolves the problem.
The following are statistics taken from Browlock hits in our telemetry from June onwards.
According to our statistics, the target victims were users visiting adult sites. More than half of them were redirected to Browlock pages after going to adult-related websites. Others were redirected through the use of ad networks. We didnt notice any adult website that stood out from our data, however, for the ad networks percentage, almost 60% were from trafficbroker.com alone.

Browlock's landing pages have different IPs and URLs from time to time. You may see more observation of this from malekals website . The URLs may look random, however it has noticeable patterns. Below are some examples:
• http:// alert. policecoin. info/ FI/cls.php
• http:// alert. porschepolice. net/ FI/cls.php
• http:// alert. xraypolice. com/ FI/cls.php
• http:// alert-police. barbrastreisandagent. com/
• http:// alert-police. estateagentsolutions. net/
• http:// attention.starpolice. biz/FI/cls.php
• http:// attention.starpolice. co/FI/cls.php
• http:// police. grantscards. com/
• http:// police. redunderground. com/
• http:// security-scan-nuqbqakx. in/
• http:// security-scan-jdytiujg. in/
• http:// system-check-abevbrye. in/
• http:// system-check-ipxmjdry. in/
• http:// security-akechksv-check. in/
• http:// security-zxqkcohl-chk. in/
• http:// law-enforcement-tqvrlbqb. in/
• http:// law-enforcement-icgkjyrr. in/
From the month of June, we have observed the following most reported URLs in our upstream, with its corresponding IPs where it is hosted:
The graph below shows the duration of these URL patterns being actively reported in our upstream. It seems that on average, Browlock was able to keep a single URL pattern of its landing pages for about two weeks to a month long.
We have also noticed that United States, United Kingdom, and countries in Europe were the most affected.
Weve seen this operation going on for quite a while now, wondering if the bad guys are really getting money from this very simple mechanism. We dont really know for sure how many victims have given in into paying a ransom from its fake alert message. But what we know for sure, is that while we see this ransomware families being active, we will keep our eyes open to keep protecting our customers from this threat.
On 15/08/14 At 02:51 PM
Weiterlesen...
