Newsfeed
Nachrichtenbote
Last August, we wrote about a series of ransomware that included SynoLocker and [URL='https://www.f-secure.com/weblog/archives/00002729.html']CryptoWall. In our Cryptowall post, we briefly mentioned the more advanced family of ransomware, CTB-Locker, which uses elliptic curve cryptography for file encryption and Tor for communication with the command & control server.
This week, another ransomware emerged using the same cryptography for encryption. It was first spotted by [URL='http://trojan7malware.blogspot.co.uk/2014/12/ophionlocker-new-ransomware-on-scene.html']Trojan7Malware from a malvertising campaign that used RIG exploit kit. They dubbed the malware as OphionLocker.
Upon infection, this malware uses a [URL='https://tor2web.org/']Tor2web URL for giving instructions on how to send the payment and obtain the decrpytor tool.
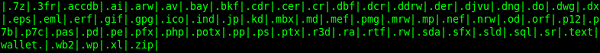
This ransomware encrypts files with the following extensions:
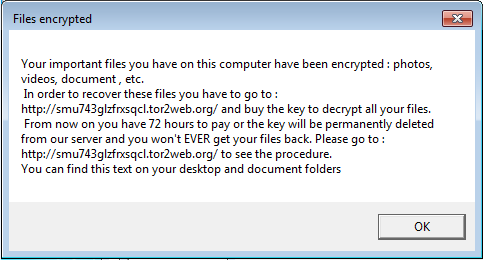
Here is the message that will be shown to the user after encryption:
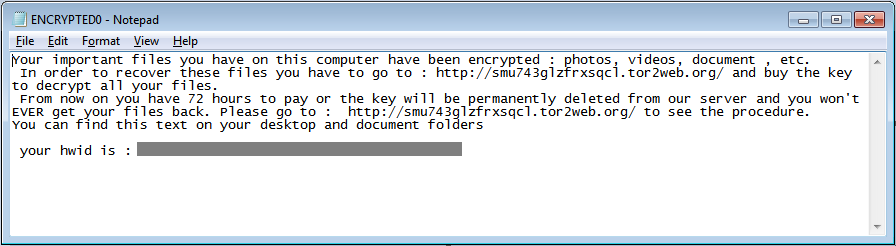
Multiple text files with the format ENCRYPTED[..].txt will be created, which contains the generated Hardware ID for the victim's machine.
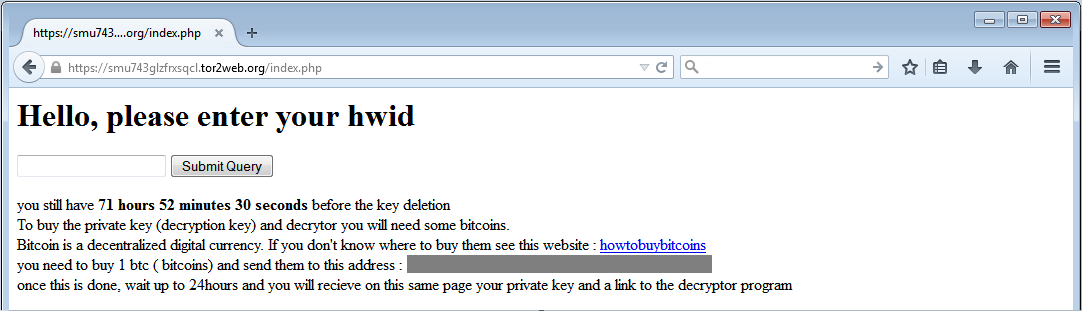
Entering the HWID will display the ransom message that asks for 1 BTC.
If, however, the infection happens on a virtual environment, OphionLocker has a slightly different trick. Though it still gives you a HWID, the message shown does not ask for a ransom payment.
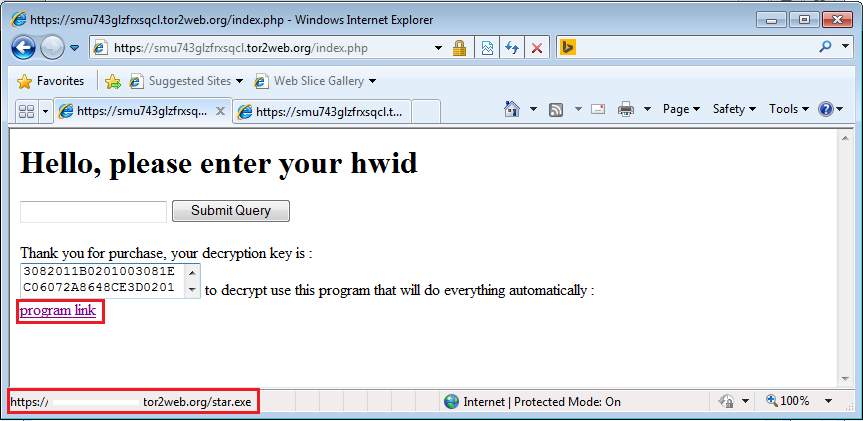
It gives the decryptor for free! Now, we know that sounds too good to be true, yet we still have to try it out. Just in case they're nice to security researchers.
Testing the decryptor will show the following message:
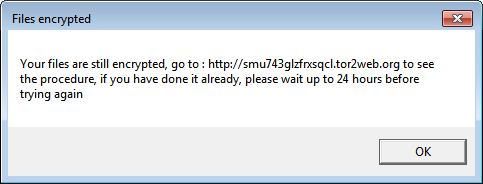
Upon clicking "OK", it will immediately pop another message:
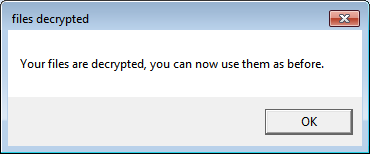
But unfortunately, no files were decrypted.
SHA1: eb78b7079fabecbec01a23c006227246e78126ab (ransomware) - Trojan:W32/Ransomware.D
On 12/12/14 At 04:25 PM
[/URL][/URL][/URL]
Weiterlesen...
This week, another ransomware emerged using the same cryptography for encryption. It was first spotted by [URL='http://trojan7malware.blogspot.co.uk/2014/12/ophionlocker-new-ransomware-on-scene.html']Trojan7Malware from a malvertising campaign that used RIG exploit kit. They dubbed the malware as OphionLocker.
Upon infection, this malware uses a [URL='https://tor2web.org/']Tor2web URL for giving instructions on how to send the payment and obtain the decrpytor tool.
This ransomware encrypts files with the following extensions:
Here is the message that will be shown to the user after encryption:
Multiple text files with the format ENCRYPTED[..].txt will be created, which contains the generated Hardware ID for the victim's machine.
Entering the HWID will display the ransom message that asks for 1 BTC.
If, however, the infection happens on a virtual environment, OphionLocker has a slightly different trick. Though it still gives you a HWID, the message shown does not ask for a ransom payment.
It gives the decryptor for free! Now, we know that sounds too good to be true, yet we still have to try it out. Just in case they're nice to security researchers.
Testing the decryptor will show the following message:
Upon clicking "OK", it will immediately pop another message:
But unfortunately, no files were decrypted.
SHA1: eb78b7079fabecbec01a23c006227246e78126ab (ransomware) - Trojan:W32/Ransomware.D
On 12/12/14 At 04:25 PM
[/URL][/URL][/URL]
Weiterlesen...
