Newsfeed
Nachrichtenbote
Today we are pleased to see an important milestone reached in a coordinated campaign against a sophisticated and well-resourced cyber espionage group. We have recently been participating in a Coordinated Malware Eradication initiative led by Novetta, in cooperation with other security vendors particularly iSight, Cisco, Volexity, Tenable, ThreatConnect, ThreatTrack Security, Microsoft and Symantec, in the aims of disrupting the operations of this particular group. Today, we are jointly releasing an improved level of coverage against the threats utilized by the group.
This espionage group, which we believe to have a strong Chinese nexus, has been targeting several industry sectors from finance, education and government to policy groups and think tanks. They have been operational at least since 2010.
The attackers use several different tools to conduct their operations. One of the tools used by these criminals is Moudoor.
Moudoor is a derivative of the famous Gh0st RAT (remote access tool) that spawned many derivatives over time. In fact, its source code has been circulating across the internet at least since 2008.
Moudoor was named after the functions that were exported by the malware components.
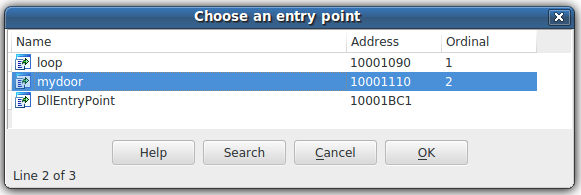
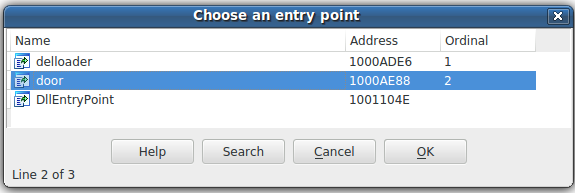
Later versions of this malware have dropped such explicit strings, however, the name of the threat remains.
One of the things that allows us to distinguish between Moudoor from other many derivatives of Gh0st is the particular magic value that it uses to communicate with its C&C. This value has been consistently set to "HTTPS", and that is one of the key distinguishers that we have used to track this particular strain over time.
At its core, Moudoor is a powerful remote access tool. The chain of events that lead to Moudoor infections usually begins with the exploitation of 0-day vulnerabilities through watering hole attacks. For example, the attackers used CVE-2012-4792 before to eventually have Moudoor land on the victim machines.
Moudoor has an impressive list of capabilities, some of which are inherited from being a derivative of the Gh0st RAT. Gh0st features extensive file system manipulation functionalities, advanced spying, monitoring features and more.
Of course, Moudoor's authors have continued to customize their "fork" over time by adding new features and removing those which were not needed. For example, earlier variants of Moudoor kept Gh0st's ability to open a remote shell, but this capability has disappeared in the newer versions. On the other hand, the attackers have worked to tailor which information is extracted from the victim machines to their specific needs and interests.
Analysis of the code of Moudoor also gave us hints that the authors of this threat are of Chinese origin. During its execution, the malware builds a string containing the current time information; such string uses Chinese characters to represent the time in human-readable format.
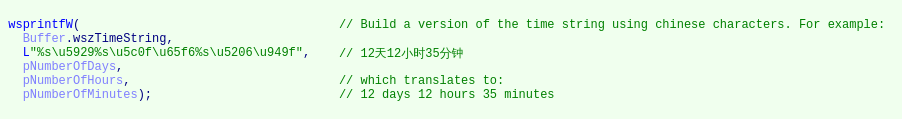
You can read a more detailed summary of the whole operation here. Microsoft has also published information about this operation, which is available from this link.
We are detecting this family as Backdoor:W32/Moudoor. Our customers have received automatic updates to detect the tools known to be used by the attackers. You can also use our Online Scanner to check for signs of compromise. Our Online Scanner is a stand-alone tool that does not require installation, thus will allow you to quickly check for infections simply by downloading and running it.
Moudoor hashes:
0fb004ed2a9c07d38b4f734b8d1621b08be731c1
83f3babe080ef0dd603ea9470a4151354f0963d5
b315fe094bb444b6b64416f3c7ea41b28d1990a4
On 14/10/14 At 04:06 PM
Weiterlesen...
This espionage group, which we believe to have a strong Chinese nexus, has been targeting several industry sectors from finance, education and government to policy groups and think tanks. They have been operational at least since 2010.
The attackers use several different tools to conduct their operations. One of the tools used by these criminals is Moudoor.
Moudoor is a derivative of the famous Gh0st RAT (remote access tool) that spawned many derivatives over time. In fact, its source code has been circulating across the internet at least since 2008.
Moudoor was named after the functions that were exported by the malware components.


Later versions of this malware have dropped such explicit strings, however, the name of the threat remains.
One of the things that allows us to distinguish between Moudoor from other many derivatives of Gh0st is the particular magic value that it uses to communicate with its C&C. This value has been consistently set to "HTTPS", and that is one of the key distinguishers that we have used to track this particular strain over time.
At its core, Moudoor is a powerful remote access tool. The chain of events that lead to Moudoor infections usually begins with the exploitation of 0-day vulnerabilities through watering hole attacks. For example, the attackers used CVE-2012-4792 before to eventually have Moudoor land on the victim machines.
Moudoor has an impressive list of capabilities, some of which are inherited from being a derivative of the Gh0st RAT. Gh0st features extensive file system manipulation functionalities, advanced spying, monitoring features and more.
Of course, Moudoor's authors have continued to customize their "fork" over time by adding new features and removing those which were not needed. For example, earlier variants of Moudoor kept Gh0st's ability to open a remote shell, but this capability has disappeared in the newer versions. On the other hand, the attackers have worked to tailor which information is extracted from the victim machines to their specific needs and interests.
Analysis of the code of Moudoor also gave us hints that the authors of this threat are of Chinese origin. During its execution, the malware builds a string containing the current time information; such string uses Chinese characters to represent the time in human-readable format.

You can read a more detailed summary of the whole operation here. Microsoft has also published information about this operation, which is available from this link.
We are detecting this family as Backdoor:W32/Moudoor. Our customers have received automatic updates to detect the tools known to be used by the attackers. You can also use our Online Scanner to check for signs of compromise. Our Online Scanner is a stand-alone tool that does not require installation, thus will allow you to quickly check for infections simply by downloading and running it.
Moudoor hashes:
0fb004ed2a9c07d38b4f734b8d1621b08be731c1
83f3babe080ef0dd603ea9470a4151354f0963d5
b315fe094bb444b6b64416f3c7ea41b28d1990a4
On 14/10/14 At 04:06 PM
Weiterlesen...
