Newsfeed
Nachrichtenbote
A recent ATM breach in Malaysia has caused havoc for several local banks. According to reports, approximately 3 million Malaysian Ringgit (almost 1 million USD) was stolen from 18 ATMs. There is no detailed information on how the attack was performed by the criminals, but according to one local news report, police claimed the criminals installed malware with the file name "ulssm.exe" which was found on the compromised ATMs. Based on the file name, we know that the malware in question was first discovered by Symantec and it is known as "PadPin". The basic technical information of this malware can be found here. We have no confirmation that PadPin is the same malware used in the Malaysian ATM hacks. But even so, we have discovered something interesting by doing our own analysis of PadPin's code.
We searched through our backend sample collection system and quickly located a few samples related to the aforementioned file name. Our automated sample analysis system did not determine the samples to be malicious because the sample will not work on a typical Windows computer; it requires a DLL library which appears to be available on machines such as ATMs or self-service terminals running Windows Embedded operating system. The DLL library is known as Extension for Financial Services (XFS):
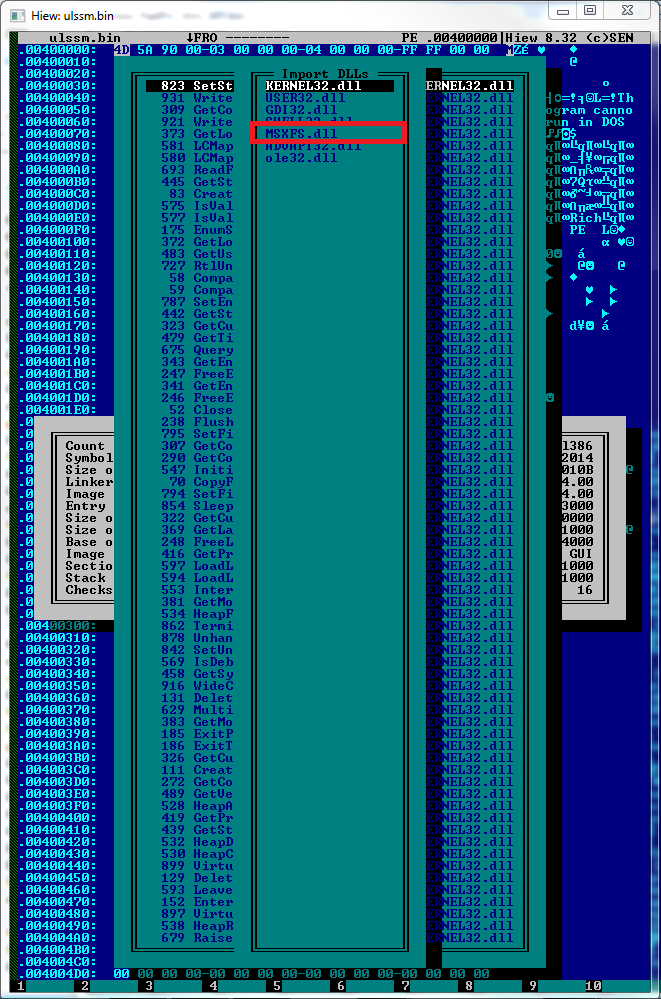
Image: Malware import Extension for Financial Services library
When we took a look at the code, we saw some unfamiliar API functions which are apparently imported via MSXFS.dll as shown in the image above. Unfortunately Microsoft does not provide official documentation for these APIs which makes understanding of the malware code more difficult. Questions continued until we came across a part of the malware code in which the malware attempts to establish a communication channel with the ATM pin pad device via one of the APIs. Basically, its purpose is to listen and wait for the key entered into the pin pad by the criminals in order to carry out different tasks as described in Symantec's write-up. In other words, the commands supported by the malware are limited to the keys available on the pin pad device. For instance, when the criminal enters "0" on pin pad, it will start dispensing money from the ATM machine. Analyzing the code, we started wondering how the malware author knows which pin pad service name to provide to the API so that the program is able to interact with the pin pad device. It's a valid question because the pin pad service name used in the code is quite unique and it is very unlikely one can figure out the service name without documentation.
Therefore, we did some web searches for the API documentation using the API name and the pin pad service name. And the result? We easily found the documentation from a dedicated ebooks website hosted on Baidu which appears to be the NCR programmer's reference manual.
After skimming through the documentation, we concluded that writing a program interacting with the ATM machine becomes handy even for someone without any prior knowledge on how to write software communicating with these ATM devices. The documentation is helpful enough to give programmers some sample code as well. Coincidentally, we also found that the alleged malware targeting Malaysian banks' ATM machines attempt to remove the "AptraDebug.lnk" shortcut file from the Windows startup folder as well as the launch point registry key "AptraDebug" on the infected machine. Its purpose is presumably to disable the default ATM software running on the machine and replaced it with the malware when the machine is rebooted. This file and registry key seem to be referring NCR APTRA XFS software, so it is safe to assume that the malware aims to target only the machine running this self-service platform software.
In conclusion, it's possible this documentation was leaked and uploaded by somebody other than PadPin's authors. And we should not rule out that the malware could be written by some experienced programmers who are or were bank employees.
It is practically impossible to stop somebody from viewing or downloading the documentation once it is available on the Internet, but there are some countermeasures that banks can use to prevent such breaches from happening again. One of the most straightforward mitigation methods is to prevent the ATM machine from running files directly from USB or CD-ROM.
Post by — Wayne
On 07/10/14 At 02:28 PM
Weiterlesen...
We searched through our backend sample collection system and quickly located a few samples related to the aforementioned file name. Our automated sample analysis system did not determine the samples to be malicious because the sample will not work on a typical Windows computer; it requires a DLL library which appears to be available on machines such as ATMs or self-service terminals running Windows Embedded operating system. The DLL library is known as Extension for Financial Services (XFS):

Image: Malware import Extension for Financial Services library
When we took a look at the code, we saw some unfamiliar API functions which are apparently imported via MSXFS.dll as shown in the image above. Unfortunately Microsoft does not provide official documentation for these APIs which makes understanding of the malware code more difficult. Questions continued until we came across a part of the malware code in which the malware attempts to establish a communication channel with the ATM pin pad device via one of the APIs. Basically, its purpose is to listen and wait for the key entered into the pin pad by the criminals in order to carry out different tasks as described in Symantec's write-up. In other words, the commands supported by the malware are limited to the keys available on the pin pad device. For instance, when the criminal enters "0" on pin pad, it will start dispensing money from the ATM machine. Analyzing the code, we started wondering how the malware author knows which pin pad service name to provide to the API so that the program is able to interact with the pin pad device. It's a valid question because the pin pad service name used in the code is quite unique and it is very unlikely one can figure out the service name without documentation.
Therefore, we did some web searches for the API documentation using the API name and the pin pad service name. And the result? We easily found the documentation from a dedicated ebooks website hosted on Baidu which appears to be the NCR programmer's reference manual.

After skimming through the documentation, we concluded that writing a program interacting with the ATM machine becomes handy even for someone without any prior knowledge on how to write software communicating with these ATM devices. The documentation is helpful enough to give programmers some sample code as well. Coincidentally, we also found that the alleged malware targeting Malaysian banks' ATM machines attempt to remove the "AptraDebug.lnk" shortcut file from the Windows startup folder as well as the launch point registry key "AptraDebug" on the infected machine. Its purpose is presumably to disable the default ATM software running on the machine and replaced it with the malware when the machine is rebooted. This file and registry key seem to be referring NCR APTRA XFS software, so it is safe to assume that the malware aims to target only the machine running this self-service platform software.
In conclusion, it's possible this documentation was leaked and uploaded by somebody other than PadPin's authors. And we should not rule out that the malware could be written by some experienced programmers who are or were bank employees.
It is practically impossible to stop somebody from viewing or downloading the documentation once it is available on the Internet, but there are some countermeasures that banks can use to prevent such breaches from happening again. One of the most straightforward mitigation methods is to prevent the ATM machine from running files directly from USB or CD-ROM.
Post by — Wayne
On 07/10/14 At 02:28 PM
Weiterlesen...
