Newsfeed
Nachrichtenbote
There have been numerous reports about the mysterious Linux backdoor connected to Turla, an APT family. The malware has some pretty interesting features, the most interesting being its ability to sniff the network interface. More specifically, it can configure its C&C address from the network traffic. This allows the backdoor to sit silently in the network and activate with a specially crafted packet sent by the attackers.
When activated, the backdoor tries to connect to specified C&C. The C&C server can then instruct the backdoor with typical RAT features such as downloading, uploading, file listing, execution, etc.
Initial investigation showed that aside from the network sniffing, this malware behaves like a typical remote access trojan.
However, after checking further, we noticed something special about the environment set for file execution command:
PATH=/bin:/usr/bin:/usr/local/bin:/usr/openwin/bin:/usr/ucb/bin:/usr/ccs/bin
LD_LIBRARY_PATH=/usr/lib:/usr/local/lib:/usr/dt/lib
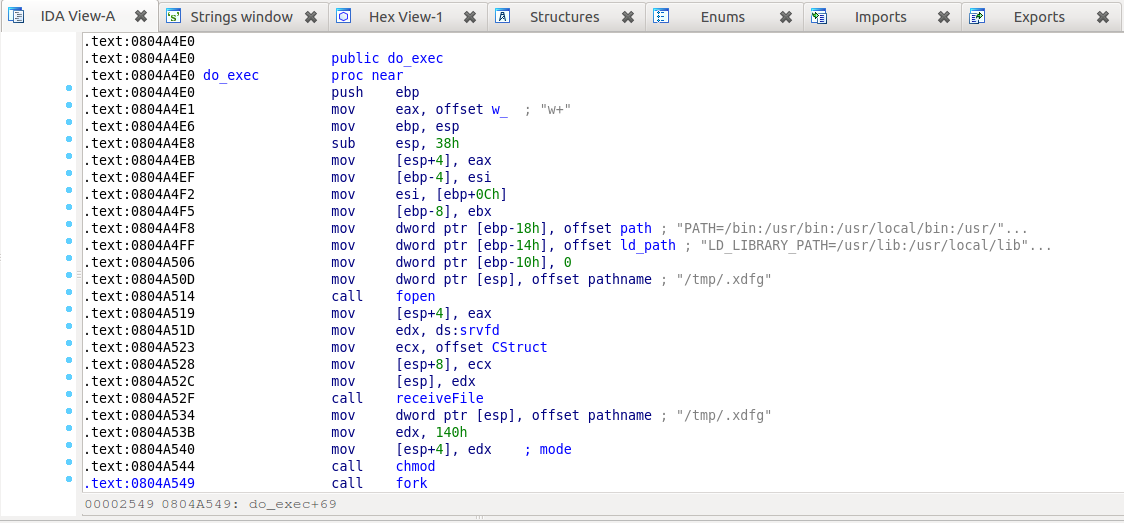
Environment set for a temporary file execution
This isn't at all typical for a Linux environment. As a matter of fact, it fits more for a Solaris environment:
/usr/openwin - Solaris OpenWindows location
/usr/ccs - C Compilation System of Solaris Studio
/usr/ucb - Solaris BSD compatibility directory
/usr/dt - Solaris CDE (Common Desktop Environment) installation location
This raises a question on whether this backdoor was originally targeting Solaris platform. There's nothing in the code and statically-linked libraries that would make this especially difficult to port, so we wouldn't be surprised to find out this malware is also on Solaris boxes in the following days.
Post by — Jarkko
On 11/12/14 At 11:06 AM
Weiterlesen...
When activated, the backdoor tries to connect to specified C&C. The C&C server can then instruct the backdoor with typical RAT features such as downloading, uploading, file listing, execution, etc.
Initial investigation showed that aside from the network sniffing, this malware behaves like a typical remote access trojan.
However, after checking further, we noticed something special about the environment set for file execution command:
PATH=/bin:/usr/bin:/usr/local/bin:/usr/openwin/bin:/usr/ucb/bin:/usr/ccs/bin
LD_LIBRARY_PATH=/usr/lib:/usr/local/lib:/usr/dt/lib

Environment set for a temporary file execution
This isn't at all typical for a Linux environment. As a matter of fact, it fits more for a Solaris environment:
/usr/openwin - Solaris OpenWindows location
/usr/ccs - C Compilation System of Solaris Studio
/usr/ucb - Solaris BSD compatibility directory
/usr/dt - Solaris CDE (Common Desktop Environment) installation location
This raises a question on whether this backdoor was originally targeting Solaris platform. There's nothing in the code and statically-linked libraries that would make this especially difficult to port, so we wouldn't be surprised to find out this malware is also on Solaris boxes in the following days.
Post by — Jarkko
On 11/12/14 At 11:06 AM
Weiterlesen...
