Newsfeed
Nachrichtenbote
One of this summer's most followed ransomware families is CryptoWall. Over time CryptoWall has seen minor updates and changes but its core functionality has stayed pretty much the same. Once a machine has been infected, CryptoWall will attempt to encrypt the contents of the victims hard drive and then demand a ransom payment in exchange for the decryption key required to get the contents back.
The only major break from this was a few months ago when we observed a few CryptoWall samples that were using a custom Tor-component to communicate with their command & control servers. This Tor component was downloaded as an encrypted binary file from compromised websites. It was then decrypted and used to set up a connection to the Tor network through which the C&C server could be reached. Interestingly, we only observed a few of these "Torified" versions of CryptoWall. The majority of the samples we have seen have stuck to the original C&C communication method.
That may now have changed. Just yesterday, the first samples of ransomware calling itself "CryptoWall 2.0" were spotted in the wild.
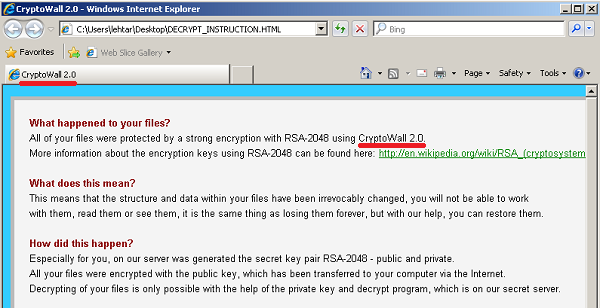
The CryptoWall 2.0 ransom page
CryptoWall 2.0 appears to use a new packer/obfuscator with an increased amount of anti-debugging and anti-static analysis tricks. Upon reaching the final malicious payload, however, CryptoWall 2.0 is almost identical to the Torified CryptoWall 1.0 samples seen earlier this summer.

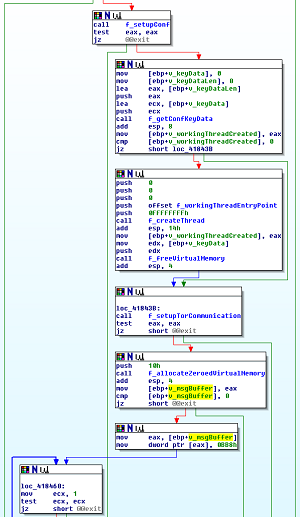
On the left, Torified CryptoWall 1.0 and on the right the same function in CryptoWall 2.0
Perhaps it was the efforts of security researchers to shut down CryptoWall C&C servers that was hurting the gangs business. Or maybe they just felt it was time for change. In any case the author(s) clearly felt a new C&C communication method was needed. And like professional software developers, the CryptoWall author(s) seem to believe in first testing new versions thoroughly alongside previous versions before completely switching over to the new one. We believe the Torified versions of CryptoWall 1.0 were exactly that, testing. Therefore we expect to see a lot more of CryptoWall 2.0 in the near future.
List of compromised Tor-component download locations:
hxxp://www.m[redacted]urg.ch/wordpress/f0k1ats
hxxp://www.ar[redacted]a.com/blog-trabajos/n65dj17i1836
hxxp://www.ar[redacted]er.cz/o515ujx2f
hxxp://www.fd[redacted]rg.de/wp-content/themes/fdp-asz/vrf8iu27h
hxxp://www.cu[redacted]n.de/z6lub76lz295x
hxxp://www.ho[redacted]t.com/5gr4hl2tvv
hxxp://www.me[redacted]o.com/wp-content/themes/mh/3sbgwh
hxxp://ep[redacted]n.ca/blog/eo7ycomyy
hxxp://www.pr[redacted]al.com.br/site/hr38xc4
hxxp://www.ji[redacted]e.be/s5eroewr
hxxp://www.je[redacted]r.at/jesneu/wp-content/themes/Girl/0l9u4lc6che
hxxp://www.dr[redacted]en.de/wordpress/3uh2e
hxxp://www.ye[redacted]ak.com/kf4bv
hxxp://www.ro[redacted]es.com/l449jbc0
hxxp://www.mc[redacted]ld.com/u2m8bbkln3fqpe
hxxp://www.fe[redacted]an.com/wp-content/themes/s431_Blue/bh7u09cpppg5h
hxxp://www.sp[redacted]es.co.uk/blog/f040z4d5d21z5rd
hxxp://www.ch[redacted]ng.co.uk/blog/wp-content/themes/the-beach-house/6k8elm10.bin
hxxp://www.gr[redacted]en.com/wp-content/themes/jarrah/ghd4vowtha0s.bin
List of .onion C&C domains:
crptarv4hcu24ijv.onion
crptbfoi5i54ubez.onion
crptcj7wd4oaafdl.onion
crptdtykhkmux333.onion
crpterfqptggpp7o.onion
Hashes for CryptoWall 2.0 samples:
e6325fc7f7168936aa9331ac707b4c3cc186b46e
Hashes for Torified CryptoWall 1.0 samples:
00e0960099ec6381aa9bf1f11b536e3e32ffa635
3370f29350115af162b613c45fd5a6a44315a213
6698bb2df60685863a664e282e493ca1e886fec3
672d6b7e31fe8f6250c6831d139012b87440274c
f21c073e57ad8a5b73139fbd4361c8985a83c9c9
Post by Artturi Lehtiö (@lehtior2)
On 02/10/14 At 02:47 PM
Weiterlesen...
The only major break from this was a few months ago when we observed a few CryptoWall samples that were using a custom Tor-component to communicate with their command & control servers. This Tor component was downloaded as an encrypted binary file from compromised websites. It was then decrypted and used to set up a connection to the Tor network through which the C&C server could be reached. Interestingly, we only observed a few of these "Torified" versions of CryptoWall. The majority of the samples we have seen have stuck to the original C&C communication method.
That may now have changed. Just yesterday, the first samples of ransomware calling itself "CryptoWall 2.0" were spotted in the wild.
The CryptoWall 2.0 ransom page
CryptoWall 2.0 appears to use a new packer/obfuscator with an increased amount of anti-debugging and anti-static analysis tricks. Upon reaching the final malicious payload, however, CryptoWall 2.0 is almost identical to the Torified CryptoWall 1.0 samples seen earlier this summer.
On the left, Torified CryptoWall 1.0 and on the right the same function in CryptoWall 2.0
Perhaps it was the efforts of security researchers to shut down CryptoWall C&C servers that was hurting the gangs business. Or maybe they just felt it was time for change. In any case the author(s) clearly felt a new C&C communication method was needed. And like professional software developers, the CryptoWall author(s) seem to believe in first testing new versions thoroughly alongside previous versions before completely switching over to the new one. We believe the Torified versions of CryptoWall 1.0 were exactly that, testing. Therefore we expect to see a lot more of CryptoWall 2.0 in the near future.
List of compromised Tor-component download locations:
hxxp://www.m[redacted]urg.ch/wordpress/f0k1ats
hxxp://www.ar[redacted]a.com/blog-trabajos/n65dj17i1836
hxxp://www.ar[redacted]er.cz/o515ujx2f
hxxp://www.fd[redacted]rg.de/wp-content/themes/fdp-asz/vrf8iu27h
hxxp://www.cu[redacted]n.de/z6lub76lz295x
hxxp://www.ho[redacted]t.com/5gr4hl2tvv
hxxp://www.me[redacted]o.com/wp-content/themes/mh/3sbgwh
hxxp://ep[redacted]n.ca/blog/eo7ycomyy
hxxp://www.pr[redacted]al.com.br/site/hr38xc4
hxxp://www.ji[redacted]e.be/s5eroewr
hxxp://www.je[redacted]r.at/jesneu/wp-content/themes/Girl/0l9u4lc6che
hxxp://www.dr[redacted]en.de/wordpress/3uh2e
hxxp://www.ye[redacted]ak.com/kf4bv
hxxp://www.ro[redacted]es.com/l449jbc0
hxxp://www.mc[redacted]ld.com/u2m8bbkln3fqpe
hxxp://www.fe[redacted]an.com/wp-content/themes/s431_Blue/bh7u09cpppg5h
hxxp://www.sp[redacted]es.co.uk/blog/f040z4d5d21z5rd
hxxp://www.ch[redacted]ng.co.uk/blog/wp-content/themes/the-beach-house/6k8elm10.bin
hxxp://www.gr[redacted]en.com/wp-content/themes/jarrah/ghd4vowtha0s.bin
List of .onion C&C domains:
crptarv4hcu24ijv.onion
crptbfoi5i54ubez.onion
crptcj7wd4oaafdl.onion
crptdtykhkmux333.onion
crpterfqptggpp7o.onion
Hashes for CryptoWall 2.0 samples:
e6325fc7f7168936aa9331ac707b4c3cc186b46e
Hashes for Torified CryptoWall 1.0 samples:
00e0960099ec6381aa9bf1f11b536e3e32ffa635
3370f29350115af162b613c45fd5a6a44315a213
6698bb2df60685863a664e282e493ca1e886fec3
672d6b7e31fe8f6250c6831d139012b87440274c
f21c073e57ad8a5b73139fbd4361c8985a83c9c9
Post by Artturi Lehtiö (@lehtior2)
On 02/10/14 At 02:47 PM
Weiterlesen...
