Newsfeed
Nachrichtenbote
A sample of the BlackEnergy family was recently uploaded to VirusTotal from Ukraine. The family is allegedly the same malware used in the cyber attack against Georgia in 2008. The malware provides attackers full access to their infected hosts. Check out SecureWorks' detailed analysis from 2010 for more information about the family.
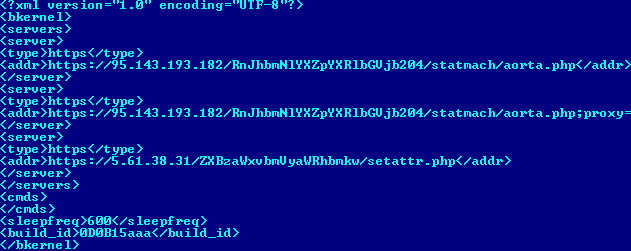
The new sample is not much of a rootkit anymore, in the sense that it no longer hides files, registries, etc. The build is now "0D0B15aaa" according to the embedded XML:
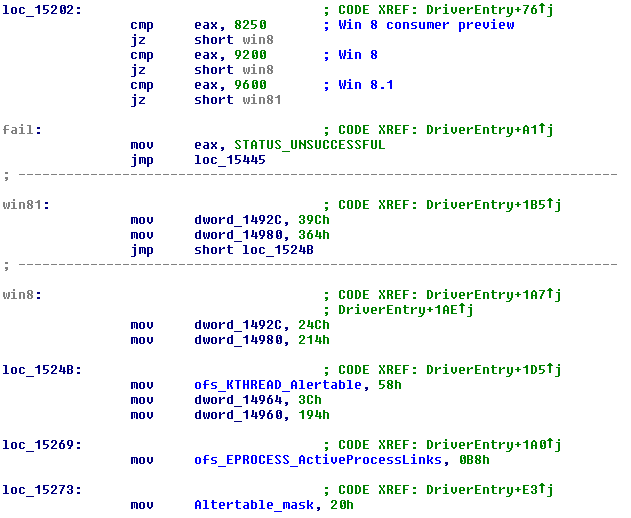
Although not used, the sample still have a routine that hides processes. This time it uses DKOM. Because of this (and to check whether svchost.exe is in an alertable state), the malware keeps a hard coded list of offsets in kernel structures that it uses for the different Windows versions. What is interesting is that the sample was designed with Windows 8 in mind:
Since the sample is not signed, the driver signing enforcement in modern Windows has to be disabled to work.
On 13/06/14 At 05:09 PM
Weiterlesen...
The new sample is not much of a rootkit anymore, in the sense that it no longer hides files, registries, etc. The build is now "0D0B15aaa" according to the embedded XML:

Although not used, the sample still have a routine that hides processes. This time it uses DKOM. Because of this (and to check whether svchost.exe is in an alertable state), the malware keeps a hard coded list of offsets in kernel structures that it uses for the different Windows versions. What is interesting is that the sample was designed with Windows 8 in mind:

Since the sample is not signed, the driver signing enforcement in modern Windows has to be disabled to work.
On 13/06/14 At 05:09 PM
Weiterlesen...
