Newsfeed
Nachrichtenbote
We have received reports about a Linux malware known as Backdoor.Gates.
Analysis showed that this malware has the following features:
• Collects information on the compromised system, such as OS version, hard disk size etc.
• Connects to a C&C server for further information. The server address and port are RSA-encrypted.
• Can perform a host of different DDoS attacks:
• TCP-SYN flood
• UDP flood
• DNS flood
• ICMP flood
• HTTP flood
• DNS Amplification
It's notable that this backdoor makes use of this file for its installation:
/etc/init.d/DbSecuritySpt
Interestingly, the string "DbSecuritySpt" is a service name also used by another, a Windows malware. After a closer look, we found out that they are more alike than we initially thought.
Both of them use the same names for the main file and the dropped components. For example, the main component is named as "gates" in the Linux version, and "Gates.exe" in the Windows version. The attack tool is called "bill" in the Linux version and "Bill.exe" in the Windows version. The DNS amplification library is "libamplify.so" or "libamplify.dll", and so on. This was too much of a coincidence, so it turned out pretty quickly that they are actually recompiled ports of the same malware.
The malware is written in C++ and the compiled code, by a quick glance, looks quite different, but closer investigation reveals that they must share the some code base. There are some OS-centric portions of the code, such as thread handling, service installation (on Windows, it is installed as a service "DbSecuritySpt", while on Linux it is a startup script in /etc/init.d/DbSecuritySpt). However, there are other similar parts, such as a simple file handling which uses fopen() and fread() among others. Using those standard C-functions is quite uncommon for a Windows programmer. It is then most likely that both variants are compiled from the same code base, with some heavy platform-specific #ifdef's.
Screenshot of Windows code:
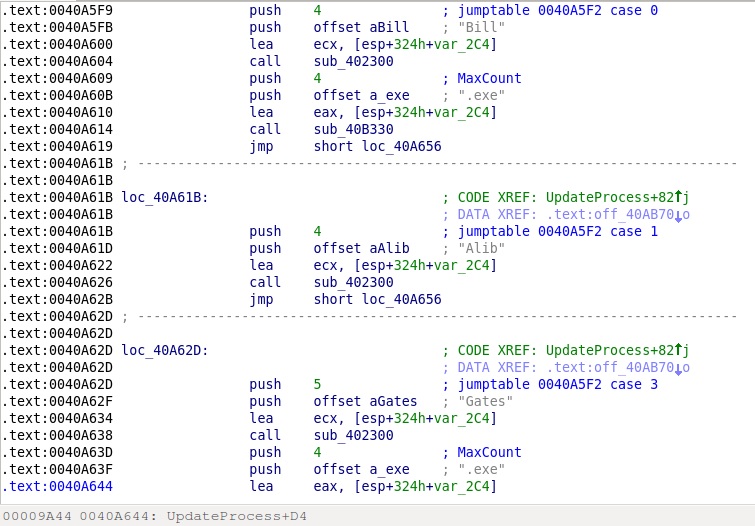
Screenshot of Linux code:
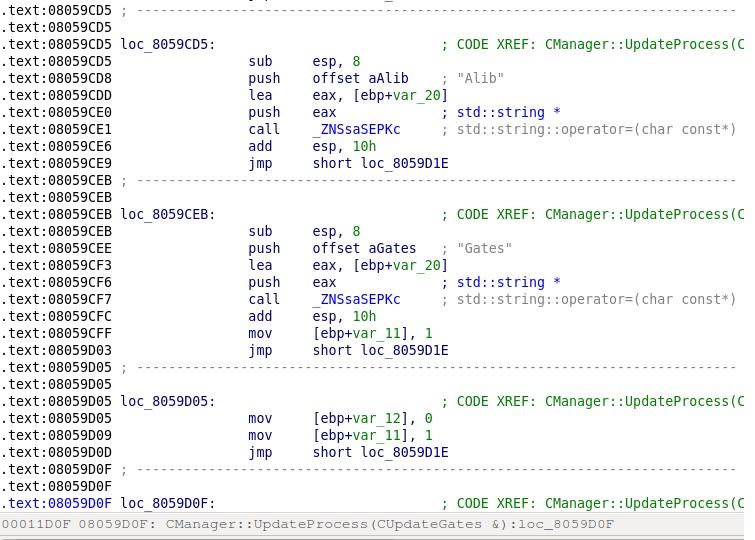
With a multi-platform malware like Backdoor.Gates, it is always interesting to find out how it is installed. We don't fully understand this yet. Based on initial analysis, there seems to be no automatic propagation or exploit functionality in the malware. The reports that we have received indicate that the malware was installed using weak SSH-server passwords, at least on Linux boxes.
More analysis on the Linux part of Backdoor.Gates have also been published by Kaspersky and DrWeb.
-- Post by Jarkko
On 01/08/14 At 08:47 AM
Weiterlesen...
Analysis showed that this malware has the following features:
• Collects information on the compromised system, such as OS version, hard disk size etc.
• Connects to a C&C server for further information. The server address and port are RSA-encrypted.
• Can perform a host of different DDoS attacks:
• TCP-SYN flood
• UDP flood
• DNS flood
• ICMP flood
• HTTP flood
• DNS Amplification
It's notable that this backdoor makes use of this file for its installation:
/etc/init.d/DbSecuritySpt
Interestingly, the string "DbSecuritySpt" is a service name also used by another, a Windows malware. After a closer look, we found out that they are more alike than we initially thought.
Both of them use the same names for the main file and the dropped components. For example, the main component is named as "gates" in the Linux version, and "Gates.exe" in the Windows version. The attack tool is called "bill" in the Linux version and "Bill.exe" in the Windows version. The DNS amplification library is "libamplify.so" or "libamplify.dll", and so on. This was too much of a coincidence, so it turned out pretty quickly that they are actually recompiled ports of the same malware.
The malware is written in C++ and the compiled code, by a quick glance, looks quite different, but closer investigation reveals that they must share the some code base. There are some OS-centric portions of the code, such as thread handling, service installation (on Windows, it is installed as a service "DbSecuritySpt", while on Linux it is a startup script in /etc/init.d/DbSecuritySpt). However, there are other similar parts, such as a simple file handling which uses fopen() and fread() among others. Using those standard C-functions is quite uncommon for a Windows programmer. It is then most likely that both variants are compiled from the same code base, with some heavy platform-specific #ifdef's.
Screenshot of Windows code:

Screenshot of Linux code:

With a multi-platform malware like Backdoor.Gates, it is always interesting to find out how it is installed. We don't fully understand this yet. Based on initial analysis, there seems to be no automatic propagation or exploit functionality in the malware. The reports that we have received indicate that the malware was installed using weak SSH-server passwords, at least on Linux boxes.
More analysis on the Linux part of Backdoor.Gates have also been published by Kaspersky and DrWeb.
-- Post by Jarkko
On 01/08/14 At 08:47 AM
Weiterlesen...
