Newsfeed
Nachrichtenbote
It's been already a week after the announcement of the CVE-2014-4114 vulnerability, and the tally of the exploiters have only increased.
There are even files where the metadata has remained the same, which clearly shows that they have been copied from the original as in the case of Mirtec and Cueisfry (a trojan linked to Japanese-related APT attacks). Authors behind these malware copied the PowerPoint Document originally used by BlackEnergy and just replaced the payload and the content with legitimate material found online.
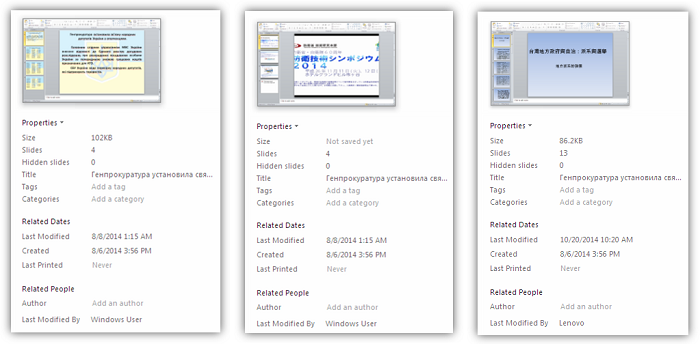
BlackEnergy, Mirtec, Cueisfry document metadata, respectively
Well, if another party's winning formula already worked, there is no need to reinvent the wheel. Until a patch is pushed out, that is. Which brings us to Taleret, a malware family known to be behind certain Taiwanese APT attacks. After CVE-2014-4114 was patched, there was a need to improvise and as such, Taleret this time grabbed a clean PowerPoint and embedded its payload to get it executed via the CVE-2014-6352, a weakness left over from CVE-2014-4114.
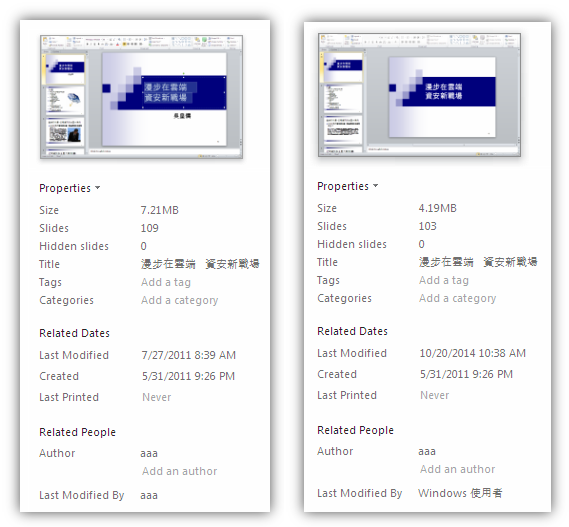
Although Microsoft has released a patch for CVE-2014-4114, CVE-2014-6352 has yet to be patched.
However, a Fix it tool is available here.
It seems that most of the content used by the malicious PowerPoint documents have been harvested from educational institutions or R&D materials that are available in the Internet, thus making it quite challenging to tell them apart.
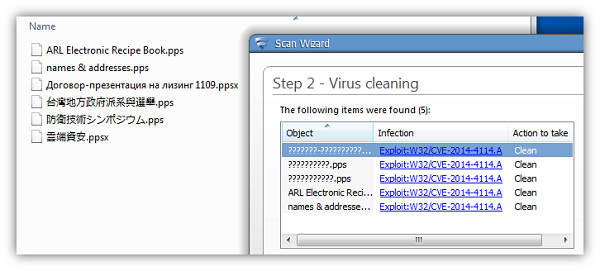
Here are some examples of both the clean documents and their malicious counterparts:

While, there isn't a patch for the other vulnerability yet, if you couldn't tell which one is clean and malicious, please verify the documents received from the source. Or, you can update your antivirus signatures to check if they are detected.
Hashes:
8f31ed3775af80cf458f9c9dd4879c62d3ec21e5 - Mirtec - C&C: 116.212.127.20
66addf1d47b51c04a1d1675b751fbbfa5993a0f0 - Cueisfry - C&C: ms.privacyserve.org
488861f8485703c97a0f665dd7503c70868d4272 - Taleret - C&C: 70.88.151.213
e9020a3cff098269a0c878a58e7abb81c9702691
02b9123088b552b6a566fc319faef385bec46250
98841ea573426883fdc2dad5e50caacfe08c8489
7d0cecfad6afbe9c0707bf82a68fff44541a2235
On 24/10/14 At 01:10 PM
Weiterlesen...
There are even files where the metadata has remained the same, which clearly shows that they have been copied from the original as in the case of Mirtec and Cueisfry (a trojan linked to Japanese-related APT attacks). Authors behind these malware copied the PowerPoint Document originally used by BlackEnergy and just replaced the payload and the content with legitimate material found online.

BlackEnergy, Mirtec, Cueisfry document metadata, respectively
Well, if another party's winning formula already worked, there is no need to reinvent the wheel. Until a patch is pushed out, that is. Which brings us to Taleret, a malware family known to be behind certain Taiwanese APT attacks. After CVE-2014-4114 was patched, there was a need to improvise and as such, Taleret this time grabbed a clean PowerPoint and embedded its payload to get it executed via the CVE-2014-6352, a weakness left over from CVE-2014-4114.

Although Microsoft has released a patch for CVE-2014-4114, CVE-2014-6352 has yet to be patched.
However, a Fix it tool is available here.
It seems that most of the content used by the malicious PowerPoint documents have been harvested from educational institutions or R&D materials that are available in the Internet, thus making it quite challenging to tell them apart.
Here are some examples of both the clean documents and their malicious counterparts:

While, there isn't a patch for the other vulnerability yet, if you couldn't tell which one is clean and malicious, please verify the documents received from the source. Or, you can update your antivirus signatures to check if they are detected.

Hashes:
8f31ed3775af80cf458f9c9dd4879c62d3ec21e5 - Mirtec - C&C: 116.212.127.20
66addf1d47b51c04a1d1675b751fbbfa5993a0f0 - Cueisfry - C&C: ms.privacyserve.org
488861f8485703c97a0f665dd7503c70868d4272 - Taleret - C&C: 70.88.151.213
e9020a3cff098269a0c878a58e7abb81c9702691
02b9123088b552b6a566fc319faef385bec46250
98841ea573426883fdc2dad5e50caacfe08c8489
7d0cecfad6afbe9c0707bf82a68fff44541a2235
On 24/10/14 At 01:10 PM
Weiterlesen...
