Newsfeed
Nachrichtenbote
Our back end automation began logging "Gameover" related IP addresses back in May. Gameover is the Peer-to-Peer variant of the ZeuS banking trojan. Last week, we took 3,300+ of the IPs and performed a GeoIP lookup on them.
And the results were quite intriguing!
Download: GameoverIPs.kml
Italy accounted for nearly 10% of the total number of IP addresses:
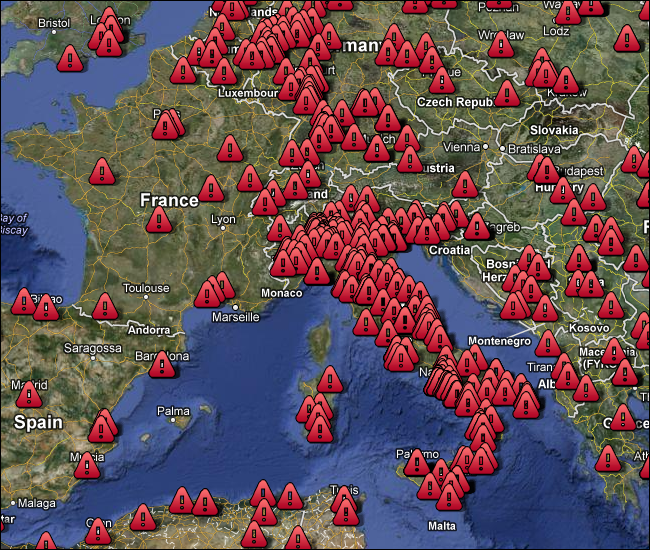
Italy, there, underneath all the caution icons…
Being curious about high number of per capita infections, we then searched the Web for additional research and discovered Brett Stone-Gross's excellent report at Dell SecureWorks.
His underreported (according to Brian Krebs) analysis more than confirms our own findings. Italy has a significant number of Gameover infections.
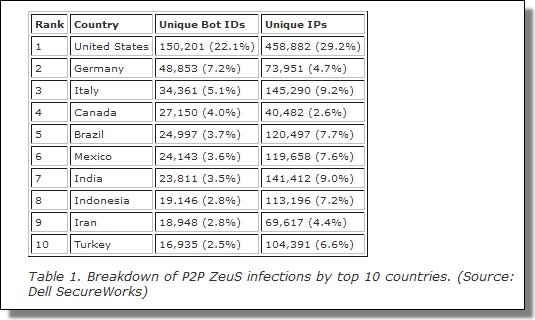
Stone-Gross's report, The Lifecycle of Peer-to-Peer (Gameover) ZeuS, includes details on 678,000 unique Gameover bots, of which, 5.1% are Italian.
From the Gameover configuration file that our analysts recently obtained, we can see that there is an active Italian campaign underway at this time. The at sign (@) indicates bank sessions that Gameover should focus on, screen-capture on click.
• @https://bancopostaimpresaonline.poste.it/bpiol/lastFortyMovementsBalance.do?method=loadLastFortyMovementList
• @https://www3.csebo.it/*
• @https://qweb.quercia.com/*
• @https://www.sparkasse.it/*
• @https://dbonline.deutsche-bank.it/*
• @https://*.cedacri.it/*
• @https://www.bancagenerali.it/*
• @https://www.csebo.it/*
• @https://*.deutsche-bank.it/*
Also of notable interest are the Arabic banks listed within the configuration file.
For the CCNA's among you: Gameover communicates with its peers via UDP on randomly assigned (at installation) ports between 10,000 and 30,000. Such communication happens routinely every several seconds or so and are small, between 40 to 350 bytes. Larger communications happen via TCP. Monitoring for an extended length of time will probably reveal repeated IP addresses.
Our earlier speculation that Gameover's sophistication is evidence of the original ZeuS author's involvement is supported by Krebs on Security posts such as this one which suggests Slavik's continued activity after his supposed "retirement".
Ciao.
Analysis by — Marko and Mikko S.
On 07/09/12 At 12:32 PM
Weiterlesen...
And the results were quite intriguing!
View Larger Map
Download: GameoverIPs.kml
Italy accounted for nearly 10% of the total number of IP addresses:

Italy, there, underneath all the caution icons…
Being curious about high number of per capita infections, we then searched the Web for additional research and discovered Brett Stone-Gross's excellent report at Dell SecureWorks.
His underreported (according to Brian Krebs) analysis more than confirms our own findings. Italy has a significant number of Gameover infections.

Stone-Gross's report, The Lifecycle of Peer-to-Peer (Gameover) ZeuS, includes details on 678,000 unique Gameover bots, of which, 5.1% are Italian.
From the Gameover configuration file that our analysts recently obtained, we can see that there is an active Italian campaign underway at this time. The at sign (@) indicates bank sessions that Gameover should focus on, screen-capture on click.
• @https://bancopostaimpresaonline.poste.it/bpiol/lastFortyMovementsBalance.do?method=loadLastFortyMovementList
• @https://www3.csebo.it/*
• @https://qweb.quercia.com/*
• @https://www.sparkasse.it/*
• @https://dbonline.deutsche-bank.it/*
• @https://*.cedacri.it/*
• @https://www.bancagenerali.it/*
• @https://www.csebo.it/*
• @https://*.deutsche-bank.it/*
Also of notable interest are the Arabic banks listed within the configuration file.
For the CCNA's among you: Gameover communicates with its peers via UDP on randomly assigned (at installation) ports between 10,000 and 30,000. Such communication happens routinely every several seconds or so and are small, between 40 to 350 bytes. Larger communications happen via TCP. Monitoring for an extended length of time will probably reveal repeated IP addresses.
Our earlier speculation that Gameover's sophistication is evidence of the original ZeuS author's involvement is supported by Krebs on Security posts such as this one which suggests Slavik's continued activity after his supposed "retirement".
Ciao.
Analysis by — Marko and Mikko S.
On 07/09/12 At 12:32 PM
Weiterlesen...
