Newsfeed
Nachrichtenbote
We get samples - lots of samples - every day. Like tens of thousands of them.
They are coming from various sources. From our customers. From honeypots and honeynets. Via our online scanners. Submitted directly from our products. From operators and ISPs. Via sample exchange with our competitors and so on.
We also get copies of samples that people submit to online virus scanning services like VirusTotal, Jotti and VirSCAN. We'd like to give big thanks to these services for their valuable co-operation.
When we get samples via such online services, we have absolutely no idea where the sample is coming from and who submitted it. Sometimes such samples can be real mysteries.
Take an example of this PDF file we got a sample of via VirusTotal. The only information we have on this 130kB sample is that it was named f1be1cdea0bcc5a1574a10771cd4e8e8.pdf (after it's MD5 hash) and that it was submitted on the 23rd of May.
When you open this document, this is what you'll see:
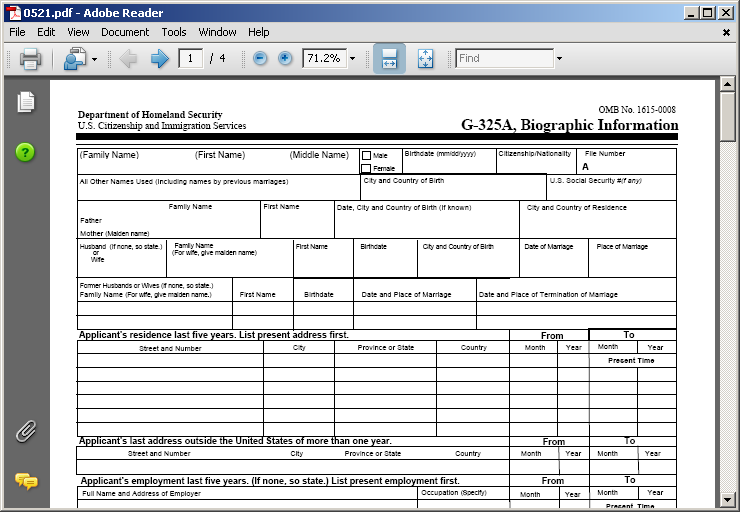
Looks like a Department of Homeland Security form G-325A.
Look again.
What's the filename?
It's not f1be1cdea0bcc5a1574a10771cd4e8e8.pdf. It's 0521.pdf.
This is not the document we opened.
So what happens here?
Apparently this PDF has been used in a targeted attack against an unknown target.
When this PDF is opened in Acrobat Reader, it uses a known exploit to to drop files.
Specifically, it creates two files in the TEMP folder: D50E.tmp.exe and 0521.pdf.
Then it executes the EXE and launches the clean 0521.pdf file to Adobe Reader in order to fool the user that everything is all right.
D50E.tmp.exe is a backdoor that creates lots of new files with innocent-sounding filenames, including:
\windows\system32\avifil16.dll
\windows\system32\avifil64.dll
\windows\system32\drivers\pcictrl.sys
\windows\system32\drivers\Nullbak.dat
\windows\system32\drivers\Beepbak.dat
The SYS component is a rootkit that tries to hide all this activity on the infected machine.
 The backdoor tries to connect to port 80 of a host called nbsstt.3322.org. Anybody operating this machine would have full access to the infected machine.
The backdoor tries to connect to port 80 of a host called nbsstt.3322.org. Anybody operating this machine would have full access to the infected machine.
Well, 3322.org is one of the well-known Chinese DNS-bouncers that we see a lot in targeted attaks. Does nbsstt mean something? Beats me, but Google will find a user with this nickname posting to several Chinese military-related web forums, such as bbs.cjdby.net.
Where does nbsstt.3322.org point to?
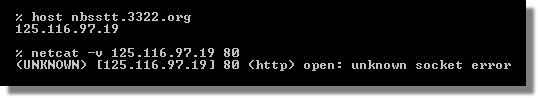
IP address 125.116.97.19 is in Zhejiang, China.
And it's live right now, answering requests at port 80. On 01/06/08 At 12:14 PM
Weiterlesen...
They are coming from various sources. From our customers. From honeypots and honeynets. Via our online scanners. Submitted directly from our products. From operators and ISPs. Via sample exchange with our competitors and so on.
We also get copies of samples that people submit to online virus scanning services like VirusTotal, Jotti and VirSCAN. We'd like to give big thanks to these services for their valuable co-operation.
When we get samples via such online services, we have absolutely no idea where the sample is coming from and who submitted it. Sometimes such samples can be real mysteries.
Take an example of this PDF file we got a sample of via VirusTotal. The only information we have on this 130kB sample is that it was named f1be1cdea0bcc5a1574a10771cd4e8e8.pdf (after it's MD5 hash) and that it was submitted on the 23rd of May.
When you open this document, this is what you'll see:

Looks like a Department of Homeland Security form G-325A.
Look again.
What's the filename?
It's not f1be1cdea0bcc5a1574a10771cd4e8e8.pdf. It's 0521.pdf.
This is not the document we opened.
So what happens here?
Apparently this PDF has been used in a targeted attack against an unknown target.
When this PDF is opened in Acrobat Reader, it uses a known exploit to to drop files.
Specifically, it creates two files in the TEMP folder: D50E.tmp.exe and 0521.pdf.
Then it executes the EXE and launches the clean 0521.pdf file to Adobe Reader in order to fool the user that everything is all right.
D50E.tmp.exe is a backdoor that creates lots of new files with innocent-sounding filenames, including:
\windows\system32\avifil16.dll
\windows\system32\avifil64.dll
\windows\system32\drivers\pcictrl.sys
\windows\system32\drivers\Nullbak.dat
\windows\system32\drivers\Beepbak.dat
The SYS component is a rootkit that tries to hide all this activity on the infected machine.

Well, 3322.org is one of the well-known Chinese DNS-bouncers that we see a lot in targeted attaks. Does nbsstt mean something? Beats me, but Google will find a user with this nickname posting to several Chinese military-related web forums, such as bbs.cjdby.net.
Where does nbsstt.3322.org point to?

IP address 125.116.97.19 is in Zhejiang, China.
And it's live right now, answering requests at port 80. On 01/06/08 At 12:14 PM
Weiterlesen...
