Newsfeed
Nachrichtenbote
The 28th Chaos Communication Congress (28C3) is currently underway in Berlin and on Tuesday, researcher Karsten Nohl gave a presentation called: Defending mobile phones. If you have an hour, it's worth watching.
Initial press reports focused on Nohl's revelation that hackers can potentially sniff numerous phone IDs and network authentications from an advantageous point, and because network authentications aren't frequently refreshed (depending on the network operator), an attacker could make expensive premium rate calls and bill them to other persons. GSM network specifications allow for every network action to be re-authenticated, but that requires serious investment in authentication servers. So operators may only do it every third call. Or tenth. Or perhaps only when the phone connects to the network.
The H Security has a good summary overview of all the topics covered during the presentation.
But one of the most interesting things, from our point of view, was Nohl's brief reference to recent reports (Dec. 13th) about various German police authorities having used nearly half a million "Silent SMS" to track suspects in 2010.
So we did a web search and found nothing about it in the English language press. However, Wikipedia's SMS entry has (had) this:
Silent messages, often called silent SMS, stealth SMS, or stealthy ping, will not show up on the display, neither
is there an acoustical signal when they are received. However, at the mobile provider some data is created
(for example, the subscriber identification IMSI). This kind of message is sent especially by the police to locate
a person or to create a complete movement profile of a person. In Germany in the year 2010, nearly half a
million "silent SMSs" were sent by the federal police, the customs, and the secret service "Office for Protection
of the Constitution."
We followed the referenced link to this Heise Online article. The title translates as: Customs, Federal Police and Protection of the Constitution in 2010 sent more than 440,000 "silent SMS".
Hmm, Germany's Customs Enforcement. Those were the folks that used the R2D2 backdoor a.k.a. "0zapftis".
Using Google Translate and Google News, we were able to locate more German language articles using "stille SMS".
The Federal Ministry of the Interior provided details on December 6th. (PDF)
In the screenshot below, you can see the number of messages sent by three authorities since 2006.
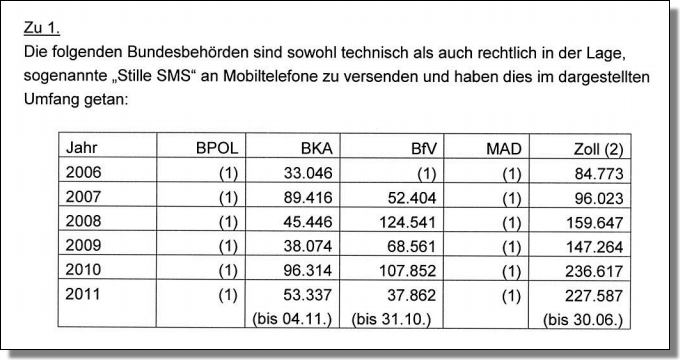
So what exactly does this mean?
Well, basically, various German law enforcement agencies have been "pinging" mobile phones. Such pings only reply whether or not the targeted resource is online or not, just like an IP network ping from a computer would.
But then after making their pings, the agencies have been requesting network logs from mobile network operators. The logs don't reveal information from the mobile phones themselves, but they can be used to locate the cell towers through which the pings traveled. And thus, can be used to track the mobile targeted.
Requesting such network logs was a legal gray area until 2007, when Germany amended its telecommunications surveillance act.
And now we are left to wonder, just how many other countries consider this type of tracking to be a gray area?
On 29/12/11 At 06:47 PM
Weiterlesen...
Initial press reports focused on Nohl's revelation that hackers can potentially sniff numerous phone IDs and network authentications from an advantageous point, and because network authentications aren't frequently refreshed (depending on the network operator), an attacker could make expensive premium rate calls and bill them to other persons. GSM network specifications allow for every network action to be re-authenticated, but that requires serious investment in authentication servers. So operators may only do it every third call. Or tenth. Or perhaps only when the phone connects to the network.
The H Security has a good summary overview of all the topics covered during the presentation.
But one of the most interesting things, from our point of view, was Nohl's brief reference to recent reports (Dec. 13th) about various German police authorities having used nearly half a million "Silent SMS" to track suspects in 2010.
So we did a web search and found nothing about it in the English language press. However, Wikipedia's SMS entry has (had) this:
Silent messages, often called silent SMS, stealth SMS, or stealthy ping, will not show up on the display, neither
is there an acoustical signal when they are received. However, at the mobile provider some data is created
(for example, the subscriber identification IMSI). This kind of message is sent especially by the police to locate
a person or to create a complete movement profile of a person. In Germany in the year 2010, nearly half a
million "silent SMSs" were sent by the federal police, the customs, and the secret service "Office for Protection
of the Constitution."
We followed the referenced link to this Heise Online article. The title translates as: Customs, Federal Police and Protection of the Constitution in 2010 sent more than 440,000 "silent SMS".
Hmm, Germany's Customs Enforcement. Those were the folks that used the R2D2 backdoor a.k.a. "0zapftis".
Using Google Translate and Google News, we were able to locate more German language articles using "stille SMS".
The Federal Ministry of the Interior provided details on December 6th. (PDF)
In the screenshot below, you can see the number of messages sent by three authorities since 2006.

So what exactly does this mean?
Well, basically, various German law enforcement agencies have been "pinging" mobile phones. Such pings only reply whether or not the targeted resource is online or not, just like an IP network ping from a computer would.
But then after making their pings, the agencies have been requesting network logs from mobile network operators. The logs don't reveal information from the mobile phones themselves, but they can be used to locate the cell towers through which the pings traveled. And thus, can be used to track the mobile targeted.
Requesting such network logs was a legal gray area until 2007, when Germany amended its telecommunications surveillance act.
And now we are left to wonder, just how many other countries consider this type of tracking to be a gray area?
On 29/12/11 At 06:47 PM
Weiterlesen...
