Newsfeed
Nachrichtenbote
Now here's something we don't see every day.
It's an interesting twist on an old tactic — a worm that uses a local elevation of privilege vulnerability to access the kernel and execute code.
Most malware with rootkit functionality will tamper with the Windows kernel and attempt to execute code in kernel mode. Typically, a special driver is used to do this.
Worm.Win32.AutoRun.nox has a payload that restores the original function pointers back to the kernel's System Service Table (SST). The usual motivation for malware to do this is to remove any SST hooks installed by security software or other malware that might affect its successful operation.
As noted, normally a special driver or the physical memory device is used to get access to kernel-mode memory to restore the pointers. AutoRun.nox is different — it uses "GDI Local Elevation of Privilege Vulnerability (CVE-2006-5758)" to do the job. For malware, its rather unique to see such a technique being used.
This vulnerability is due to an error in handling a shared memory structure, which allows the structure to be remapped from read-only to writable. April 2007's update patched the vulnerability.
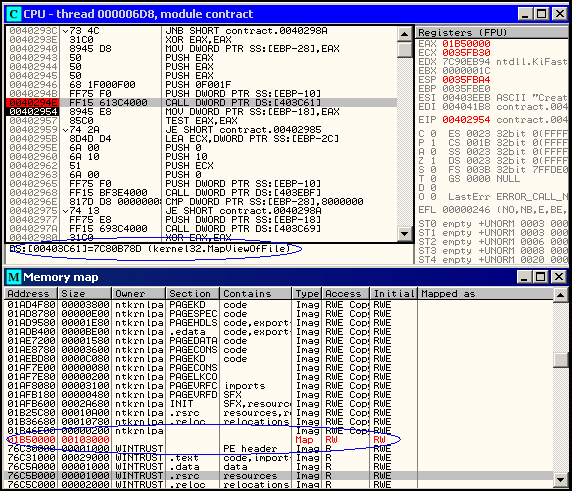
After remapping the memory, the malware will initialize a CPalette object. It will then search for the palette object in the shared kernel memory structure. Since the memory is now writable, it can be altered to include a pointer to a special function that will remove any existing SST hooks. Finally, a call to GetNearestPaletteIndex will indirectly cause the function to be executed. Afterwards, the palette object is restored leaving no trace of the attack.
If attacking this vulnerability fails, the worm goes back to the tried-and-true "special driver" method. The driver is detected by us as Rootkit:W32/Agent.UG.
Either way, if the attack is successful, the machine is compromised as the attacker can access the kernel and execute code, or cause a denial of service.
This attack will only work on unpatched machines running without the latest updates. Microsoft ranks this vulnerability as Important and recommends that users apply the update immediately.
Foresight? From: http://technet.microsoft.com/en-us/library/cc750820.aspx
"With this new release, the Window Manager, GDI, and related graphics device drivers have been moved to the Windows NT Executive running in kernel mode"
Response team post by — Lordian, Ian, Kimmo, Antti ...and Mika On 26/09/08 At 02:52 PM
Weiterlesen...
It's an interesting twist on an old tactic — a worm that uses a local elevation of privilege vulnerability to access the kernel and execute code.
Most malware with rootkit functionality will tamper with the Windows kernel and attempt to execute code in kernel mode. Typically, a special driver is used to do this.
Worm.Win32.AutoRun.nox has a payload that restores the original function pointers back to the kernel's System Service Table (SST). The usual motivation for malware to do this is to remove any SST hooks installed by security software or other malware that might affect its successful operation.
As noted, normally a special driver or the physical memory device is used to get access to kernel-mode memory to restore the pointers. AutoRun.nox is different — it uses "GDI Local Elevation of Privilege Vulnerability (CVE-2006-5758)" to do the job. For malware, its rather unique to see such a technique being used.
This vulnerability is due to an error in handling a shared memory structure, which allows the structure to be remapped from read-only to writable. April 2007's update patched the vulnerability.

After remapping the memory, the malware will initialize a CPalette object. It will then search for the palette object in the shared kernel memory structure. Since the memory is now writable, it can be altered to include a pointer to a special function that will remove any existing SST hooks. Finally, a call to GetNearestPaletteIndex will indirectly cause the function to be executed. Afterwards, the palette object is restored leaving no trace of the attack.
If attacking this vulnerability fails, the worm goes back to the tried-and-true "special driver" method. The driver is detected by us as Rootkit:W32/Agent.UG.
Either way, if the attack is successful, the machine is compromised as the attacker can access the kernel and execute code, or cause a denial of service.
This attack will only work on unpatched machines running without the latest updates. Microsoft ranks this vulnerability as Important and recommends that users apply the update immediately.
Foresight? From: http://technet.microsoft.com/en-us/library/cc750820.aspx
"With this new release, the Window Manager, GDI, and related graphics device drivers have been moved to the Windows NT Executive running in kernel mode"
Response team post by — Lordian, Ian, Kimmo, Antti ...and Mika On 26/09/08 At 02:52 PM
Weiterlesen...
