Newsfeed
Nachrichtenbote
Trojan number one:
A report of an Apple Remote Desktop Agent vulnerability recently surfaced. Now there's news of a trojan that can exploit the flaw.
The exploit tool, called "Applescript Trojan horse template" was crafted by forum participants of MacShadows.com. These guys appear to have been hobbyist hackers interested in testing the ARDAgent vulnerability. It doesn't appear to be in the wild at present. We detect it as Backdoor.Mac.Hovdy.a.
What's the ARDAgent flaw? In a nutshell, ARDAgent runs Applescript with root privileges. So once the victim is tricked into installing Hovdy, no user passwords are required for it to do its thing, which is provide backdoor access to the attacker.
You can read more details from Security Fix here and here. SecureMac's advisory is here.
Trojan number two:
There was also another Mac OSX trojan discovered last week.
This one was found by Intego. We detect it as Trojan-PSW:OSX/PokerStealer.A.
Response Analyst Mark G. performed our analysis and provided the following details:
PokerStealer.A heavily relies on social engineering. It comes with the filename PokerGame.app (180Kb), sounds interesting, right?

However, once executed, it will prompt the user for a password.
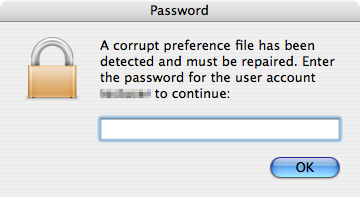
It checks the provided password to see if it matches the username of the machine. If not, it will ask again. It needs the user's password to continue.
What happens behind the scenes is the following: It enables the SSH of the infected machine by running; It acquires the following information — local IP address, subnet mask, private IP address of the router (domain), public IP address by querying via the Internet; It gets the version of OSX, recovers its hash and saves it to a file named secret_file.
After all the necessary information has been gathered it then sends the information to a specific e-mail address with the following information: Subject Howdy; Message details include username, password, and IP addresses.
With the e-mailed information, the attacker can perform routines from a remote location through SSH without the user knowing it and may even take control of the infected machine.
The PokerStealer.A trojan appears to have been written by someone with more than just hobbyist level motivations.
PokerStealer's infection is limited by the password requirement.
So what do you think happens next?
That's right. The author of PokerStealer (motivated by profit) is going to seek out the hobbyist's "Applescript Trojan horse template" and will reduce the infection steps of PokerStealer.A to simply running an application named "Poker Game".
How many Mac users do you think like to play poker? On 24/06/08 At 03:35 PM
Weiterlesen...
A report of an Apple Remote Desktop Agent vulnerability recently surfaced. Now there's news of a trojan that can exploit the flaw.
The exploit tool, called "Applescript Trojan horse template" was crafted by forum participants of MacShadows.com. These guys appear to have been hobbyist hackers interested in testing the ARDAgent vulnerability. It doesn't appear to be in the wild at present. We detect it as Backdoor.Mac.Hovdy.a.
What's the ARDAgent flaw? In a nutshell, ARDAgent runs Applescript with root privileges. So once the victim is tricked into installing Hovdy, no user passwords are required for it to do its thing, which is provide backdoor access to the attacker.
You can read more details from Security Fix here and here. SecureMac's advisory is here.
Trojan number two:
There was also another Mac OSX trojan discovered last week.
This one was found by Intego. We detect it as Trojan-PSW:OSX/PokerStealer.A.
Response Analyst Mark G. performed our analysis and provided the following details:
PokerStealer.A heavily relies on social engineering. It comes with the filename PokerGame.app (180Kb), sounds interesting, right?

However, once executed, it will prompt the user for a password.

It checks the provided password to see if it matches the username of the machine. If not, it will ask again. It needs the user's password to continue.
What happens behind the scenes is the following: It enables the SSH of the infected machine by running; It acquires the following information — local IP address, subnet mask, private IP address of the router (domain), public IP address by querying via the Internet; It gets the version of OSX, recovers its hash and saves it to a file named secret_file.
After all the necessary information has been gathered it then sends the information to a specific e-mail address with the following information: Subject Howdy; Message details include username, password, and IP addresses.
With the e-mailed information, the attacker can perform routines from a remote location through SSH without the user knowing it and may even take control of the infected machine.
The PokerStealer.A trojan appears to have been written by someone with more than just hobbyist level motivations.
PokerStealer's infection is limited by the password requirement.
So what do you think happens next?
That's right. The author of PokerStealer (motivated by profit) is going to seek out the hobbyist's "Applescript Trojan horse template" and will reduce the infection steps of PokerStealer.A to simply running an application named "Poker Game".
How many Mac users do you think like to play poker? On 24/06/08 At 03:35 PM
Weiterlesen...
