Newsfeed
Nachrichtenbote
On December 29, 2013, Der Spiegel, a German weekly news magazine, published an article about an internal NSA catalog that lists technology available to the NSA's Tailored Access Operations (TAO). Among that technology is "IRATEMONK".
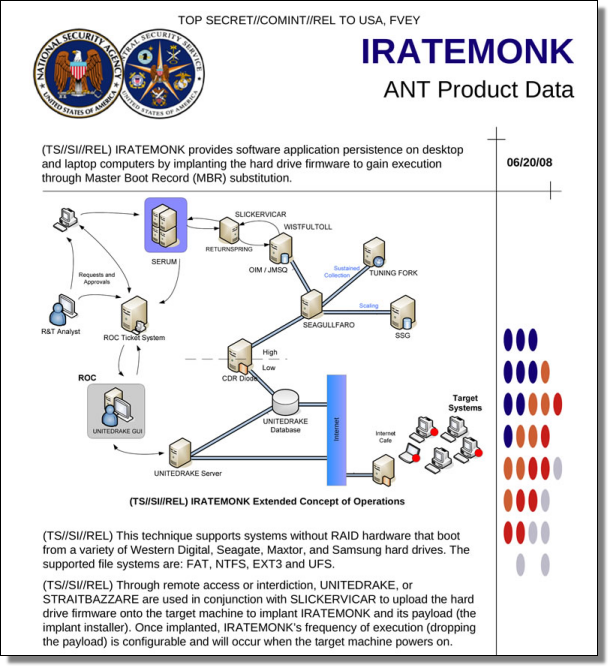
"IRATEMONK provides software application persistence on desktop and laptop computers by implanting the hard drive firmware to gain execution through Master Boot Record (MBR) substitution."
Source: Wikimedia
"This technique supports systems without RAID hardware that boot from a variety of Western Digital, Seagate, Maxtor, and Samsung hard drives."
On January 31, 2014, Bruce Schneier deemed IRATEMONK his "NSA Exploit of the Day" which prompted this from Nicholas Weaver.
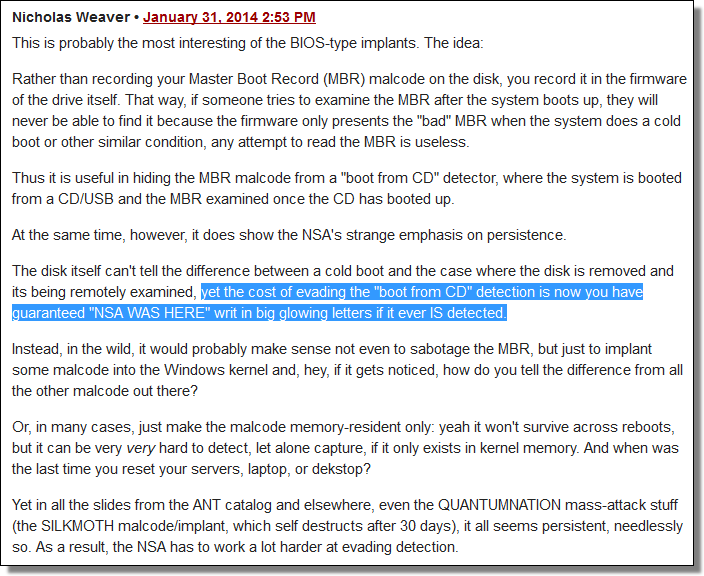
"This is probably the most interesting of the BIOS-type implants."
"yet the cost of evading the 'boot from CD' detection is now you have guaranteed 'NSA WAS HERE' writ in big glowing letters if it ever IS detected."
Well, funny story — components related to IRATEMONK have now been detected — by the folks at Kaspersky Labs. Kaspersky's research paper refers to a threat actor called the "Equation group" whose country of origin is not named, but the group has exactly the capabilities detailed by the NSA's ANT catalog.
Ars Technica has an excellent summary here: How "omnipotent" hackers tied to NSA hid for 14 yearsand were found at last.
On 17/02/15 At 01:20 PM
Weiterlesen...
"IRATEMONK provides software application persistence on desktop and laptop computers by implanting the hard drive firmware to gain execution through Master Boot Record (MBR) substitution."

Source: Wikimedia
"This technique supports systems without RAID hardware that boot from a variety of Western Digital, Seagate, Maxtor, and Samsung hard drives."
On January 31, 2014, Bruce Schneier deemed IRATEMONK his "NSA Exploit of the Day" which prompted this from Nicholas Weaver.

"This is probably the most interesting of the BIOS-type implants."
"yet the cost of evading the 'boot from CD' detection is now you have guaranteed 'NSA WAS HERE' writ in big glowing letters if it ever IS detected."
Well, funny story — components related to IRATEMONK have now been detected — by the folks at Kaspersky Labs. Kaspersky's research paper refers to a threat actor called the "Equation group" whose country of origin is not named, but the group has exactly the capabilities detailed by the NSA's ANT catalog.
Ars Technica has an excellent summary here: How "omnipotent" hackers tied to NSA hid for 14 yearsand were found at last.
On 17/02/15 At 01:20 PM
Weiterlesen...
