Newsfeed
Nachrichtenbote
We believe you should never pay a ransom to online criminals. The reason is quite simple. File-encrypting ransomware holds the victim's personal files "at ransom" until a payment is made. For the scheme to work, the victim has to believe that paying up will help. However, the only certain outcome from paying criminals is to encourage them to continue their malicious activities: paying the ransom might not actually get you your files back. Case in point, a recent ransomware family commonly known as SynoLocker.
SynoLocker targets network attached storage devices manufactured by Synology. Once a device has been infected with SynoLocker, the malware will proceed to encrypt files stored on the device. It will also present the victim with a ransom message demanding payment in return for decryption of the files. Here, however, the criminals behind SynoLocker make a false promise. In many of the cases we have observed, the decryption process didn't actually work or the decryption key provided by the criminals was incorrect.
Even after being double-crossed by the criminals, all hope is not lost. If a victim is able to obtain the correct decryption key, the files can still be restored. For this purpose, we are today releasing a small tool, a Python script, written by us. This tool can be used to safely decrypt SynoLocker-encrypted files as long as the correct decryption key can be provided. The tool does not in any way break the encryption of files created by SynoLocker and it does not attempt to bruteforce the decryption key. It will only work, if the decryption key is already known.
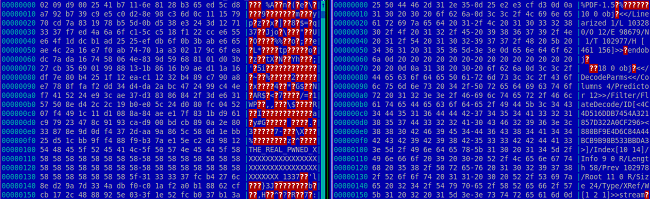
On the left, the beginning of a file encrypted by SynoLocker and, on the right, the beginning of the same file decrypted.
Another use case for our decryption tool is a situation where a user has paid the ransom but can't use the decryption key as they have removed the SynoLocker malware from the infected device. Instead of reinfecting your device with the malware (which is a bad idea), you can use the key together with our script to decrypt your files.
By releasing this tool to the community at large, we hope that we can contribute to undoing the harm caused by these criminals.
We never recommend anyone to pay a ransom.
Our decryption tool, as well as installation and usage instructions, can be found here.
Post by Artturi (@lehtior2)
On 22/08/14 At 12:44 PM
Weiterlesen...
SynoLocker targets network attached storage devices manufactured by Synology. Once a device has been infected with SynoLocker, the malware will proceed to encrypt files stored on the device. It will also present the victim with a ransom message demanding payment in return for decryption of the files. Here, however, the criminals behind SynoLocker make a false promise. In many of the cases we have observed, the decryption process didn't actually work or the decryption key provided by the criminals was incorrect.
Even after being double-crossed by the criminals, all hope is not lost. If a victim is able to obtain the correct decryption key, the files can still be restored. For this purpose, we are today releasing a small tool, a Python script, written by us. This tool can be used to safely decrypt SynoLocker-encrypted files as long as the correct decryption key can be provided. The tool does not in any way break the encryption of files created by SynoLocker and it does not attempt to bruteforce the decryption key. It will only work, if the decryption key is already known.

On the left, the beginning of a file encrypted by SynoLocker and, on the right, the beginning of the same file decrypted.
Another use case for our decryption tool is a situation where a user has paid the ransom but can't use the decryption key as they have removed the SynoLocker malware from the infected device. Instead of reinfecting your device with the malware (which is a bad idea), you can use the key together with our script to decrypt your files.
By releasing this tool to the community at large, we hope that we can contribute to undoing the harm caused by these criminals.
We never recommend anyone to pay a ransom.
Our decryption tool, as well as installation and usage instructions, can be found here.
Post by Artturi (@lehtior2)
On 22/08/14 At 12:44 PM
Weiterlesen...
