Newsfeed
Nachrichtenbote
Karmina wrote about a malware targeting multiple operating systems on Monday.
The Mac OS X sample that time was a PowerPC binary. Yesterday, we received an Intel x86 version in our backend systems which appears to have been used in a similar type of attack.
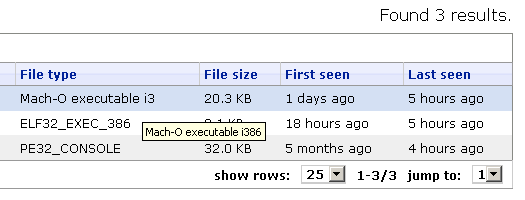
Nothing fancy. This time the sample uses the server 199.180.197.59, which was not accessible during our analysis. It uses the ports 8080, 8081, 443 for OS X, Linux and Windows respectively.
The payloads remain the same, with only their implementations changed. Instead of connecting to the remote server to get additional shellcode to execute (which then opens a reverse shell), the OS X binary immediately opens a reverse shell. Attackers with access to the shell are able to do pretty much anything with the system.
The Linux binary remains the same except that it is using a different server. In Windows, the same payload routine is now in the form of a shellcode:
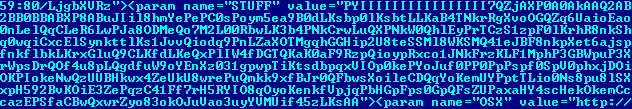
The shellcode is executed using the SET module shellcodeexec.binary. In a nutshell, despite being in a different form and using a different server and port, the behavior of the Windows payload remains the same.
The files are detected as:
Backdoor:OSX/TESrel.A (MD5: 0c6f52069afb3e8f0019f6873fb7a8b0)
Backdoor:Linux/GetShell.A (MD5: 2241851dfb75b3562f4da30363df7383)
Backdoor:W32/TES.A (SET module shellcodeexec.binary / MD5: 7a0fcd15ee1c2d9d196ab6515adf2f87)
The appearance of these samples in our backend indicates that the incident we reported earlier is not the only one out there.
On 13/07/12 At 11:45 AM
Weiterlesen...
The Mac OS X sample that time was a PowerPC binary. Yesterday, we received an Intel x86 version in our backend systems which appears to have been used in a similar type of attack.

Nothing fancy. This time the sample uses the server 199.180.197.59, which was not accessible during our analysis. It uses the ports 8080, 8081, 443 for OS X, Linux and Windows respectively.
The payloads remain the same, with only their implementations changed. Instead of connecting to the remote server to get additional shellcode to execute (which then opens a reverse shell), the OS X binary immediately opens a reverse shell. Attackers with access to the shell are able to do pretty much anything with the system.
The Linux binary remains the same except that it is using a different server. In Windows, the same payload routine is now in the form of a shellcode:

The shellcode is executed using the SET module shellcodeexec.binary. In a nutshell, despite being in a different form and using a different server and port, the behavior of the Windows payload remains the same.
The files are detected as:
Backdoor:OSX/TESrel.A (MD5: 0c6f52069afb3e8f0019f6873fb7a8b0)
Backdoor:Linux/GetShell.A (MD5: 2241851dfb75b3562f4da30363df7383)
Backdoor:W32/TES.A (SET module shellcodeexec.binary / MD5: 7a0fcd15ee1c2d9d196ab6515adf2f87)
The appearance of these samples in our backend indicates that the incident we reported earlier is not the only one out there.
On 13/07/12 At 11:45 AM
Weiterlesen...
