Newsfeed
Nachrichtenbote
There was a rather innovative Facebook malware attack last week which pushed both Windows and Mac malware.
While some folks were distracted by the Mac scareware component, it appeared to us as only the secondary factor in the overall attack. The Windows component, a fake "Adobe Flash Player" update, has ZeuS bot characteristics according to an analyst on our Threat Solutions team. We therefore conclude that the attack was focused on building a Windows OS botnet, and that the Mac OS scareware was tacked on as a bonus (as there are no ZeuS binaries to push at Mac users).
Facebook took more than 24 hours to block malicious links redirecting to newtubes.in: a domain using an Indian TLD, hosted on a Lithuanian server, and registered to "Narcisa Scott" of Thailand.
In the end, all links used by the attack were deleted by Facebook.
And we had hoped last week that Facebook killed whatever spam/attack vector was being used.
But that hope was in vain.
The same bad guys are now spamming links to porn sites via Facebook profiles:
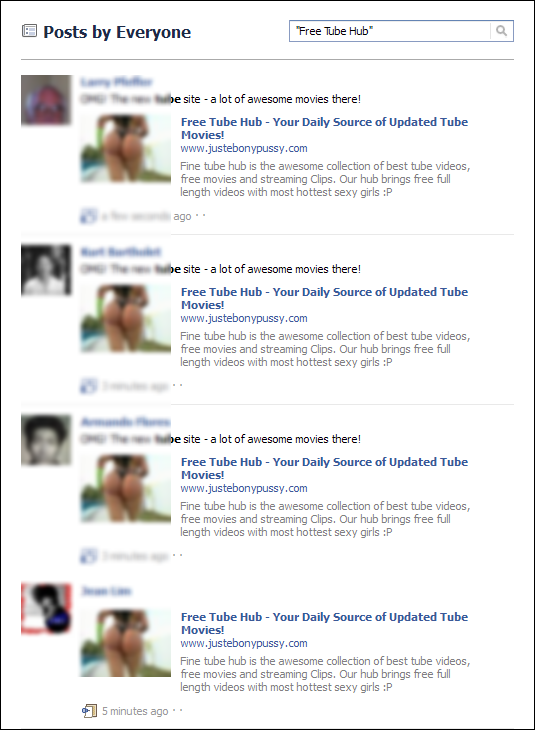
You can see profiles posting the links via an Openbook search for "Free Tube Hub".
The sites, which have names such as blackbootyblog.com, ebonyarea.com, justebonypussy.com and ebonykey.com, all have a common theme…
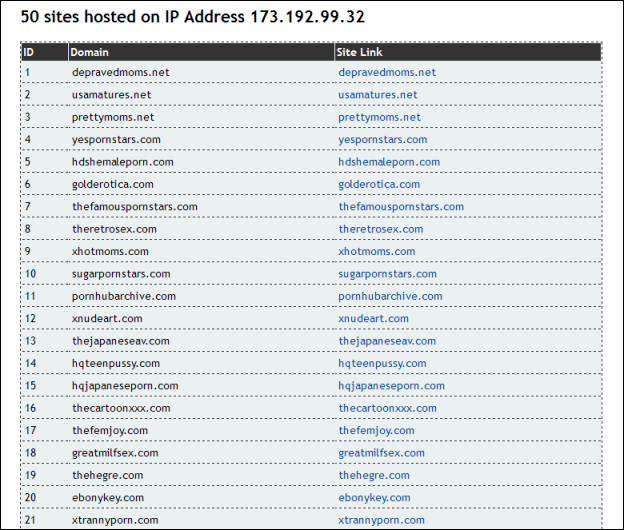
That's because many of them are hosted on the same server:
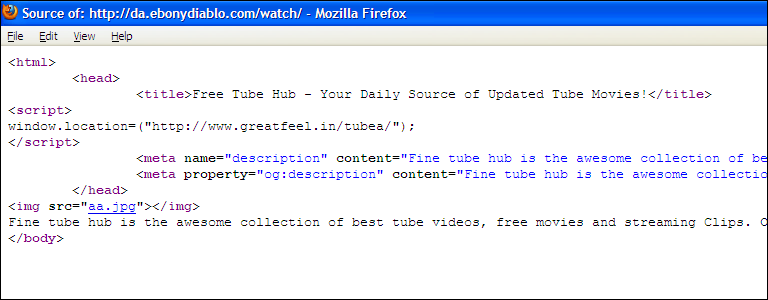
The website server appears to be compromised and a folder called /watch/ has been inserted that contains script which attempts to redirect users to borntobefree.in: a domain using an Indian TLD, is hosted on a Lithuanian server, and is registered to "Andrew Farrell" in Thailand.
Sounds familiar.
So… the porn site server is a smokescreen to hide the real attack site, borntobefree.in.
Neat trick.
As was the case in last week's malware attack, too many visits from the same IP address will result in a redirection to youtube.com. Also, the attack server is Geo-IP aware and focuses on users from the USA and UK.
We currently see no evidence that these links are being spread "virally" via Facebook Platform. Instead, they appear to be posted directly to profiles via bots.
If true, Facebook has a problem. To block these types of attacks, they'll need to suspend the profiles of infected users. But how to inform the user as to which computer is infected?
As we said last week, this is a highly professional attack using well developed techniques.
And it looks to us as if it could be here to stay for a while.
—————
Updated to add on June 9th: Bots continue to spam Facebook with porn based links, and Facebook continues to fail at blocking them (72+ hours and counting).
The links are not redirecting to malware at this time, based on our analysis. Instead, they are currently redirecting to two additional porn sites, one of which we saw last week when these links were pushing fake Flash Players and Mac scareware.
The spammed links use very consistent text, so it's quite surprising that Facebook doesn't have some sort of automation to block accounts from posting the links.
The structure is as follows: there's a porn site, hosted on a common server (see above) and it contains a folder called "/watch/". That folder contains a page with script to pull content from another location:
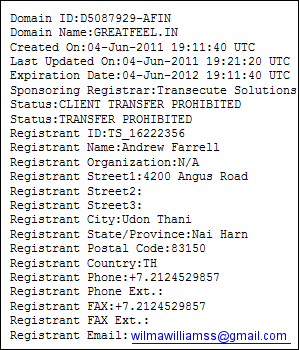
In this case, greatfeel.in, another Lithuanian server with an Indian TLD.
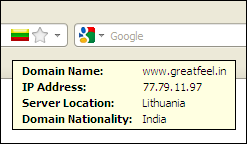
And no big surprise, greatfeel.in is also registered to "Andrew Farrell" in Thailand.
On 07/06/11 At 12:46 PM
Weiterlesen...
While some folks were distracted by the Mac scareware component, it appeared to us as only the secondary factor in the overall attack. The Windows component, a fake "Adobe Flash Player" update, has ZeuS bot characteristics according to an analyst on our Threat Solutions team. We therefore conclude that the attack was focused on building a Windows OS botnet, and that the Mac OS scareware was tacked on as a bonus (as there are no ZeuS binaries to push at Mac users).
Facebook took more than 24 hours to block malicious links redirecting to newtubes.in: a domain using an Indian TLD, hosted on a Lithuanian server, and registered to "Narcisa Scott" of Thailand.
In the end, all links used by the attack were deleted by Facebook.
And we had hoped last week that Facebook killed whatever spam/attack vector was being used.
But that hope was in vain.
The same bad guys are now spamming links to porn sites via Facebook profiles:

You can see profiles posting the links via an Openbook search for "Free Tube Hub".
The sites, which have names such as blackbootyblog.com, ebonyarea.com, justebonypussy.com and ebonykey.com, all have a common theme…
That's because many of them are hosted on the same server:

The website server appears to be compromised and a folder called /watch/ has been inserted that contains script which attempts to redirect users to borntobefree.in: a domain using an Indian TLD, is hosted on a Lithuanian server, and is registered to "Andrew Farrell" in Thailand.
Sounds familiar.
So… the porn site server is a smokescreen to hide the real attack site, borntobefree.in.
Neat trick.
As was the case in last week's malware attack, too many visits from the same IP address will result in a redirection to youtube.com. Also, the attack server is Geo-IP aware and focuses on users from the USA and UK.
We currently see no evidence that these links are being spread "virally" via Facebook Platform. Instead, they appear to be posted directly to profiles via bots.
If true, Facebook has a problem. To block these types of attacks, they'll need to suspend the profiles of infected users. But how to inform the user as to which computer is infected?
As we said last week, this is a highly professional attack using well developed techniques.
And it looks to us as if it could be here to stay for a while.
—————
Updated to add on June 9th: Bots continue to spam Facebook with porn based links, and Facebook continues to fail at blocking them (72+ hours and counting).
The links are not redirecting to malware at this time, based on our analysis. Instead, they are currently redirecting to two additional porn sites, one of which we saw last week when these links were pushing fake Flash Players and Mac scareware.
The spammed links use very consistent text, so it's quite surprising that Facebook doesn't have some sort of automation to block accounts from posting the links.
The structure is as follows: there's a porn site, hosted on a common server (see above) and it contains a folder called "/watch/". That folder contains a page with script to pull content from another location:

In this case, greatfeel.in, another Lithuanian server with an Indian TLD.

And no big surprise, greatfeel.in is also registered to "Andrew Farrell" in Thailand.

On 07/06/11 At 12:46 PM
Weiterlesen...
