Newsfeed
Nachrichtenbote
Tuesday's post refers to Downadup/Conflicker as an MS08-067 worm variant. What do we mean by that?
Downadup and other such similar worms exploit a vulnerability in the Windows Server service.
Server Service Vulnerability — CVE-2008-4250.
The vulnerability is detailed by October 23rd's Microsoft Security Bulletin MS08-067.
There are a few important notes to be made about this particular Security Bulletin…
First — It was an out-of-band update.

Second — It was given an "Exploitability Index Assessment" of "1 – Consistent exploit code likely".
That kind of speaks for itself, doesn't it?
Third — It allows for Remote Code Execution, in numerous versions of Windows (particularly critical for 2000, XP, and Server 2003).
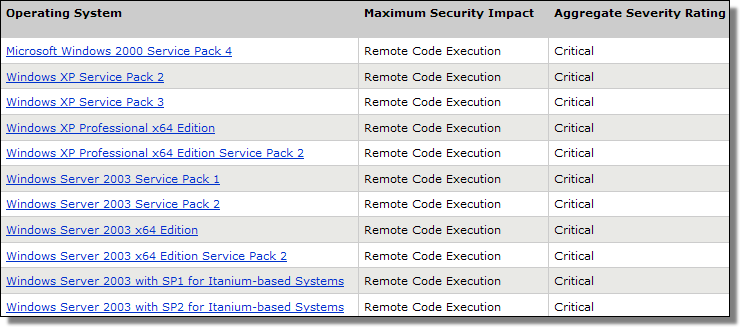
All of these combined factors equals something quite serious that should be patched as soon as possible. If you are having difficulties with Automatic Updates, the bulletin links to manual downloads.
Security Update for Windows XP
Security Update for Windows Server 2003
It's always a good idea to be ready for out-of-band updates. You can subscribe to Microsoft Security Notifications here.
Downadup has "old school" worm functionality (no user interaction required), the likes of which we haven't really seen for a while now. It also knows some current tricks; it's a worm that spreads via the Internet, local area networks, and removable media. While it doesn't seem to be gaining very much traction on the Internet, it's rapidly spreading once it's inside of local area networks that aren't patched.
(If you're a network administrator, a proactive scan for vulnerable machines may be well worth your time.)
Make sure that your antivirus software is up-to-date and disable Autoplay *and* Autorun functionality if possible. Downadup spreads itself via Network Shares and Removable Storage Devices such as USB memory. Downadup also attempts to brute-force account passwords so make sure that your administrator accounts are secure and use strict passwords.
Alright, that covers prevention — what about those of you that have infected computers within your networks?
Remember, Downadup is a network worm. You must clean all of the computers within your network or else you risk reinfections. Servers first, then workstations. Disinfect, then use the manual Microsoft update to patch, then manually update your antivirus, then do a full system scan for all files.
If you use F-Secure Anti-Virus, you can download our manual updates from here.
Downadup uses random extensions for some of its components so you'll need to scan all file types on the system once you have disinfected.
We have a disinfection tool that may assist your efforts. You can download it from here. It's a command line utility and you should carefully review the included readme.txt file.
Our Downadup.AL description provides additional details. On 08/01/09 At 07:49 PM
Weiterlesen...
Downadup and other such similar worms exploit a vulnerability in the Windows Server service.
Server Service Vulnerability — CVE-2008-4250.
The vulnerability is detailed by October 23rd's Microsoft Security Bulletin MS08-067.
There are a few important notes to be made about this particular Security Bulletin…
First — It was an out-of-band update.

Second — It was given an "Exploitability Index Assessment" of "1 – Consistent exploit code likely".
That kind of speaks for itself, doesn't it?
Third — It allows for Remote Code Execution, in numerous versions of Windows (particularly critical for 2000, XP, and Server 2003).

All of these combined factors equals something quite serious that should be patched as soon as possible. If you are having difficulties with Automatic Updates, the bulletin links to manual downloads.
Security Update for Windows XP
Security Update for Windows Server 2003
It's always a good idea to be ready for out-of-band updates. You can subscribe to Microsoft Security Notifications here.
Downadup has "old school" worm functionality (no user interaction required), the likes of which we haven't really seen for a while now. It also knows some current tricks; it's a worm that spreads via the Internet, local area networks, and removable media. While it doesn't seem to be gaining very much traction on the Internet, it's rapidly spreading once it's inside of local area networks that aren't patched.
(If you're a network administrator, a proactive scan for vulnerable machines may be well worth your time.)
Make sure that your antivirus software is up-to-date and disable Autoplay *and* Autorun functionality if possible. Downadup spreads itself via Network Shares and Removable Storage Devices such as USB memory. Downadup also attempts to brute-force account passwords so make sure that your administrator accounts are secure and use strict passwords.
Alright, that covers prevention — what about those of you that have infected computers within your networks?
Remember, Downadup is a network worm. You must clean all of the computers within your network or else you risk reinfections. Servers first, then workstations. Disinfect, then use the manual Microsoft update to patch, then manually update your antivirus, then do a full system scan for all files.
If you use F-Secure Anti-Virus, you can download our manual updates from here.
Downadup uses random extensions for some of its components so you'll need to scan all file types on the system once you have disinfected.
We have a disinfection tool that may assist your efforts. You can download it from here. It's a command line utility and you should carefully review the included readme.txt file.
Our Downadup.AL description provides additional details. On 08/01/09 At 07:49 PM
Weiterlesen...
