Newsfeed
Nachrichtenbote
In September, we blogged about CosmicDuke leveraging timely, political topics to deceive the recipient into opening the malicious document. After a more detailed analysis of the files we made two major discoveries.
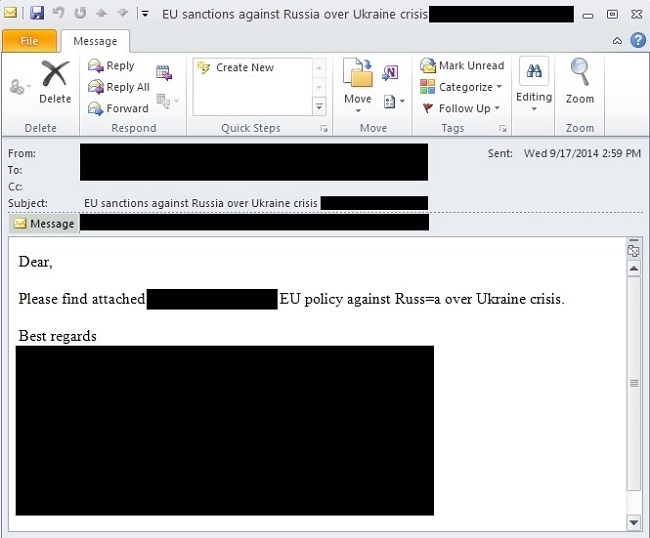
Based on emails that we found from VirusTotal, at least one European Ministry of Foreign Affairs has been targeted. Here is a redacted version of one of the emails:
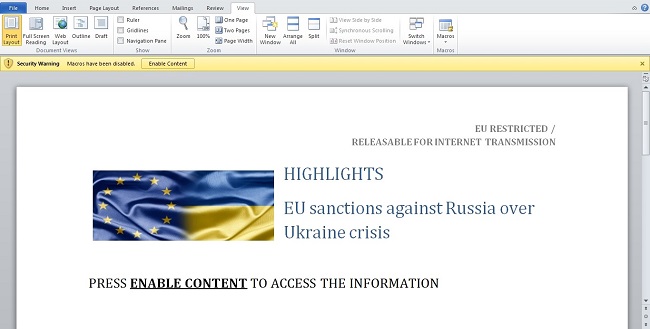
Its heartwarming to see how kind the attackers are: when you open the email attachment, the Word document helps you enable macros by instructing you to click Enable Content.
Once the victim enables macros the system gets infected with CosmicDuke, which brings us to our second discovery: in addition to the usual infostealer features, the CosmicDuke executables also install MiniDuke.
In our analysis released in July we mentioned that CosmicDuke seems to be connected to MiniDuke because both malware families use the same loader which has been exclusively used by the MiniDuke group. The CosmicDuke samples that infect the system with MiniDuke give us further evidence that the same actor is behind both malware families.
Looking at the targets of malware campaigns often helps us understand who might be behind the operations. In this sense, CosmicDuke is quite interesting. The malware has a distinctly dual nature: it targets people involved with illegal substances but also high-profile organizations like government agencies. This same kind of duality can also be seen in a related case, OnionDuke. When we first blogged about OnionDuke in November, we mentioned that OnionDuke is connected to MiniDuke through the use of shared command and control infrastructure. We also mentioned that OnionDuke appears to be used for two distinct purposes: in targeted attacks against high-profile targets such as government agencies and interestingly also in mass infection campaigns against Tor users and downloaders of torrent files. Further research has shown that not only can the victims of OnionDuke be clearly divided into two groups, but the versions of OnionDuke used and the command and control infrastructure used are also similarly divisible.
In the mass infection campaigns of OnionDuke, the attackers have used compromised web servers and free hosting providers for command and control. In these campaigns, the victim computer has been infected with a limited backdoor version of OnionDuke whose main purpose is to contact the C&C server to download and execute additional components. These downloaded components then perform tasks such as collecting system information and user credentials. On the contrary, in the attacks on high-profile targets, the C&C infrastructure used by OnionDuke has been solely owned and operated by the attackers. This infrastructure is also largely shared with known MiniDuke infrastructure. In these cases, the attackers have used a much more full-featured version of OnionDuke that doesnt need to download any additional components to perform its tasks. Importantly, this division of tactics perfectly aligns with the division of victims.
We have shown a connection between MiniDuke, OnionDuke, and CosmicDuke. We have also observed an interesting duality in the uses of OnionDuke and CosmicDuke. The question then is: what does all this mean? Like Kaspersky pointed out in their excellent blog post, one explanation is that CosmicDuke is used as a legal spyware tool by law enforcement agencies and interestingly Kaspersky observed victims involved with illegal substances only in Russia. Our data supports this observation. Moreover, none of the high-profile targets of CosmicDuke that weve seen have been from Russia but what these targets have in common is that their interests arent exactly aligned with Russia. Likewise, similar distinctions hold true for OnionDuke suggesting it may be part of the same collection of spyware tools. Considering the victims of the law enforcement use case seem to be from Russia, and none of the high-profile victims are exactly pro-Russian, we believe that a Russian government agency is behind these operations.
Samples hashes:
EU sanctions against Russia over Ukraine crisis .docm: 82448eb23ea9eb3939b6f24df46789bf7f2d43e3
A Scottish Yes to independence .docm: c86b13378ba2a41684e1f93b4c20e05fc5d3d5a3
32-bit dropper DLL: 241075fc1493172c47d881bcbfbf21cfa4daa42d
64-bit dropper DLL: 51ac683df63ff71a0003ca17e640bbeaaa14d0aa
CosmicDuke-MiniDuke combo: 7ad1bef0ba61dbed98d76d4207676d08c893fc13
OnionDuke limited backdoor: b491c14d8cfb48636f6095b7b16555e9a575d57f
OnionDuke full backdoor: d433f281cf56015941a1c2cb87066ca62ea1db37
Post by Timo (@TimoHirvonen) and Artturi (@lehtior2)
On 07/01/15 At 02:38 PM
Weiterlesen...
Based on emails that we found from VirusTotal, at least one European Ministry of Foreign Affairs has been targeted. Here is a redacted version of one of the emails:

Its heartwarming to see how kind the attackers are: when you open the email attachment, the Word document helps you enable macros by instructing you to click Enable Content.

Once the victim enables macros the system gets infected with CosmicDuke, which brings us to our second discovery: in addition to the usual infostealer features, the CosmicDuke executables also install MiniDuke.
In our analysis released in July we mentioned that CosmicDuke seems to be connected to MiniDuke because both malware families use the same loader which has been exclusively used by the MiniDuke group. The CosmicDuke samples that infect the system with MiniDuke give us further evidence that the same actor is behind both malware families.
Looking at the targets of malware campaigns often helps us understand who might be behind the operations. In this sense, CosmicDuke is quite interesting. The malware has a distinctly dual nature: it targets people involved with illegal substances but also high-profile organizations like government agencies. This same kind of duality can also be seen in a related case, OnionDuke. When we first blogged about OnionDuke in November, we mentioned that OnionDuke is connected to MiniDuke through the use of shared command and control infrastructure. We also mentioned that OnionDuke appears to be used for two distinct purposes: in targeted attacks against high-profile targets such as government agencies and interestingly also in mass infection campaigns against Tor users and downloaders of torrent files. Further research has shown that not only can the victims of OnionDuke be clearly divided into two groups, but the versions of OnionDuke used and the command and control infrastructure used are also similarly divisible.
In the mass infection campaigns of OnionDuke, the attackers have used compromised web servers and free hosting providers for command and control. In these campaigns, the victim computer has been infected with a limited backdoor version of OnionDuke whose main purpose is to contact the C&C server to download and execute additional components. These downloaded components then perform tasks such as collecting system information and user credentials. On the contrary, in the attacks on high-profile targets, the C&C infrastructure used by OnionDuke has been solely owned and operated by the attackers. This infrastructure is also largely shared with known MiniDuke infrastructure. In these cases, the attackers have used a much more full-featured version of OnionDuke that doesnt need to download any additional components to perform its tasks. Importantly, this division of tactics perfectly aligns with the division of victims.
We have shown a connection between MiniDuke, OnionDuke, and CosmicDuke. We have also observed an interesting duality in the uses of OnionDuke and CosmicDuke. The question then is: what does all this mean? Like Kaspersky pointed out in their excellent blog post, one explanation is that CosmicDuke is used as a legal spyware tool by law enforcement agencies and interestingly Kaspersky observed victims involved with illegal substances only in Russia. Our data supports this observation. Moreover, none of the high-profile targets of CosmicDuke that weve seen have been from Russia but what these targets have in common is that their interests arent exactly aligned with Russia. Likewise, similar distinctions hold true for OnionDuke suggesting it may be part of the same collection of spyware tools. Considering the victims of the law enforcement use case seem to be from Russia, and none of the high-profile victims are exactly pro-Russian, we believe that a Russian government agency is behind these operations.
Samples hashes:
EU sanctions against Russia over Ukraine crisis .docm: 82448eb23ea9eb3939b6f24df46789bf7f2d43e3
A Scottish Yes to independence .docm: c86b13378ba2a41684e1f93b4c20e05fc5d3d5a3
32-bit dropper DLL: 241075fc1493172c47d881bcbfbf21cfa4daa42d
64-bit dropper DLL: 51ac683df63ff71a0003ca17e640bbeaaa14d0aa
CosmicDuke-MiniDuke combo: 7ad1bef0ba61dbed98d76d4207676d08c893fc13
OnionDuke limited backdoor: b491c14d8cfb48636f6095b7b16555e9a575d57f
OnionDuke full backdoor: d433f281cf56015941a1c2cb87066ca62ea1db37
Post by Timo (@TimoHirvonen) and Artturi (@lehtior2)
On 07/01/15 At 02:38 PM
Weiterlesen...
