Newsfeed
Nachrichtenbote
Sometime during the beginning of the year, we have encountered a surge in Fareit spams. Fareit is a downloader used to deliver Zeus and Cryptowall.
Lately, we have been noticing yet another downloader being spammed. It seems that the spammer for this downloader has spent more effort to trick the user into believing that its a legitimate email.
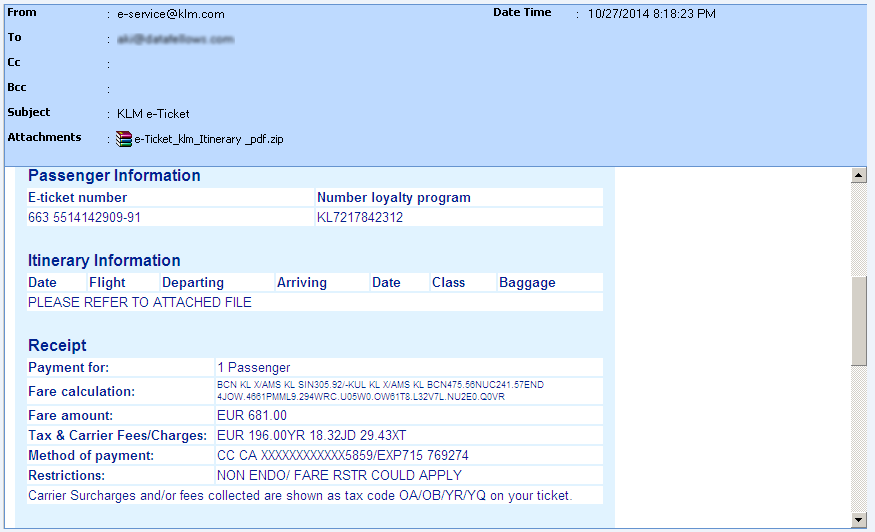
A recent spam was a fake KLM e-ticket which was tailored to pretend to come from the Sales & Service Center of Air France KLM.
However, this spammer did not only tend to English language speakers. Recently, we also saw quite a number of its spam sent in Polish.
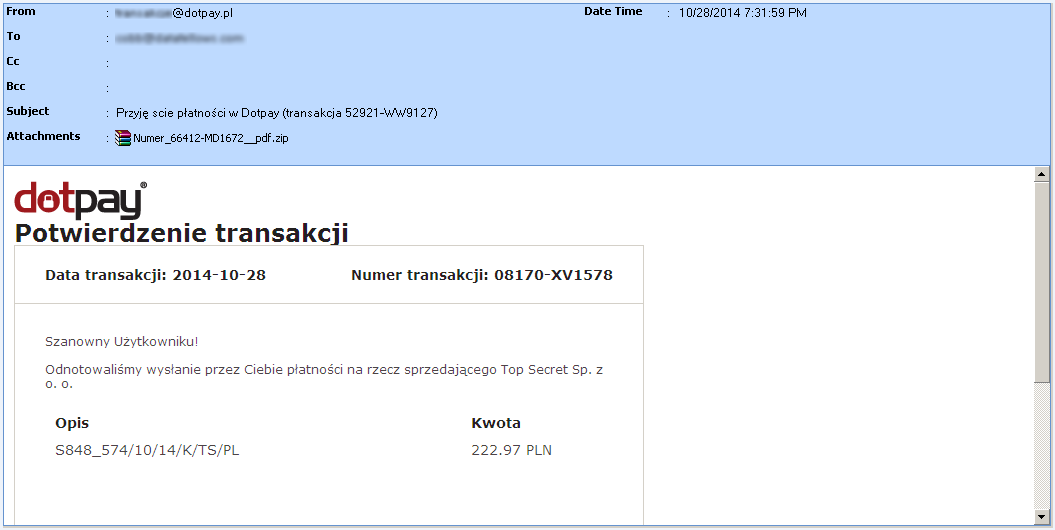
This email, for example, supposedly comes from dotpay.pl, a service for online transaction payment that is based in Poland.
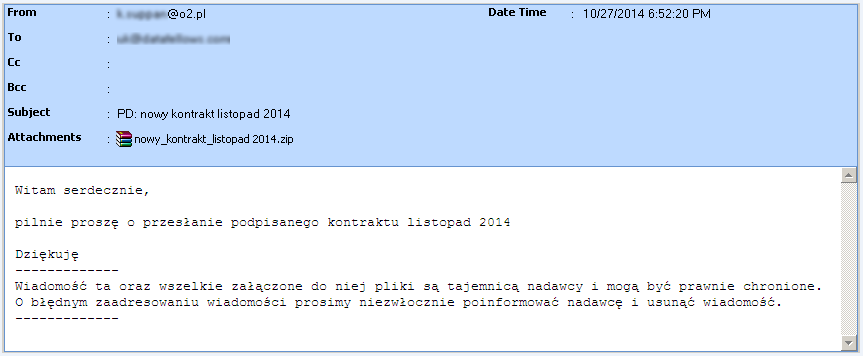
While this one uses an ISP thats popular in Poland.
And just when we thought the spammers language skills ends there, it gave us a sample of its Finnish-themed spam.
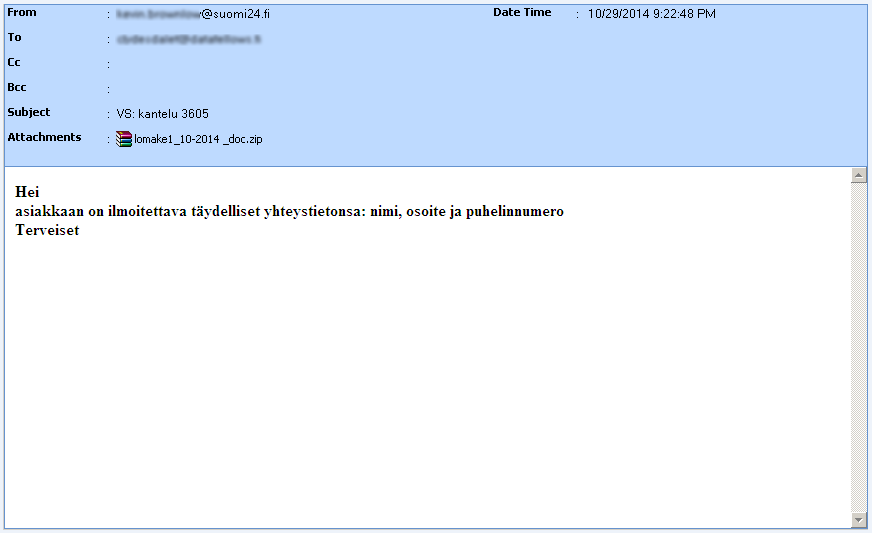
The grammar seems to be quite convincing enough considering that even the subject and attachments are using the correct Finnish terms. Not only that, the email address used, suomi24.fi, is one of Finlands most popular websites.
Obviously, spammers are also doing their research in customizing their messages to produce more effective scams. Not only do they use the language of the target country or people, but they have also achieved to make use of popular email or service providers.
The payload of these spams is a Trojan Downloader known as Wauchos.
Here are its recent filenames:
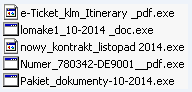
For the two sample attachments, it confirms internet connection by trying to connect to http://www.google.com/webhp.
It makes the following network connections:
http://188. 225.32.207/ssdc32716372/login.php
http://188. 225.32.208/ssdc32716372/file.php
http://188. 225.32.209/ssdc32716372/file.php
http://188. 225.32.209/ssdc32716372/file.php
http://188. 225.32.209/ssdc32716372/file.php
http://92. 53.97.194/ssdc32716372/file.php
http://46. 28.55.113/ssdc32716372/file.php
And it downloads these additional trojans from the following:
http://auto*.it/*/jeve.exe
http://dd*.ru/old.exe
The Wauchos variants weve seen in these emails downloaded either Zbot or Cridex, which are both information stealers.
We detect these families as Trojan-Downloader:W32/Wauchos, Trojan-Spy:W32/Zbot, and Trojan:W32/Cridex.
On 31/10/14 At 04:01 PM
Weiterlesen...
Lately, we have been noticing yet another downloader being spammed. It seems that the spammer for this downloader has spent more effort to trick the user into believing that its a legitimate email.
A recent spam was a fake KLM e-ticket which was tailored to pretend to come from the Sales & Service Center of Air France KLM.
However, this spammer did not only tend to English language speakers. Recently, we also saw quite a number of its spam sent in Polish.
This email, for example, supposedly comes from dotpay.pl, a service for online transaction payment that is based in Poland.
While this one uses an ISP thats popular in Poland.
And just when we thought the spammers language skills ends there, it gave us a sample of its Finnish-themed spam.
The grammar seems to be quite convincing enough considering that even the subject and attachments are using the correct Finnish terms. Not only that, the email address used, suomi24.fi, is one of Finlands most popular websites.
Obviously, spammers are also doing their research in customizing their messages to produce more effective scams. Not only do they use the language of the target country or people, but they have also achieved to make use of popular email or service providers.
The payload of these spams is a Trojan Downloader known as Wauchos.
Here are its recent filenames:
For the two sample attachments, it confirms internet connection by trying to connect to http://www.google.com/webhp.
It makes the following network connections:
http://188. 225.32.207/ssdc32716372/login.php
http://188. 225.32.208/ssdc32716372/file.php
http://188. 225.32.209/ssdc32716372/file.php
http://188. 225.32.209/ssdc32716372/file.php
http://188. 225.32.209/ssdc32716372/file.php
http://92. 53.97.194/ssdc32716372/file.php
http://46. 28.55.113/ssdc32716372/file.php
And it downloads these additional trojans from the following:
http://auto*.it/*/jeve.exe
http://dd*.ru/old.exe
The Wauchos variants weve seen in these emails downloaded either Zbot or Cridex, which are both information stealers.
We detect these families as Trojan-Downloader:W32/Wauchos, Trojan-Spy:W32/Zbot, and Trojan:W32/Cridex.
On 31/10/14 At 04:01 PM
Weiterlesen...
