Newsfeed
Nachrichtenbote
There are many ongoing discussions about "Flame" right now — an espionage tool, information was disclosed about it on Monday.
There are plenty of questions from customers, and also from members of the press.
Mikko spoke with Clark Boyd of PRI's The World yesterday about the breaking news.
Symantec's Liam O Murchu spoke with Kai Ryssdal of Marketplace in a very measured and "economical" conversation about Flame's functionality.
Some good questions have been asked. And plenty of hyperbole has been generated.
Here are some questions of our own.
• Am I protected from Flame?
That's the wrong question. You should be asking yourself this: am I at risk?
• Alright then, am I at risk from Flame?
Let's see, are you a systems administrator for a Middle Eastern government?
No? Then no… you aren't at risk.
The number of computers estimated to be infected with Flame is one thousand and there are more than one billion Windows computers in the world. You do the math. You're just as likely to win the lottery.
Additionally: Flame is not a worm. Its architecture includes wormable functionality but those functions are disabled by default. So Flame isn't spreading like a worm and therefore you won't be infected unless you've been specifically targeted.
And then there's the fact that Flame is now known to be in the wild. And so… it's been "turned off". Even Flame's targets are no longer at risk. The real power of an espionage tool is that it's a secret. Flame is no longer a secret and so it will therefore be abandoned. Operational security has been compromised.
• Okay, but still — in theory — am I protected?
We have detections for Flame and our current software blocks and prevents Flame from functioning based on our tests. If you have the most current version of your antivirus software and it's functioning properly with up to date databases, you should be good.
• So I'm safe?
Safe? Okay look… Flame is estimated to be at least two years old. That's old in terms of software code. And Flame is now a known quantity. You don't need to worry about it. Flame has been extinguished.
But…that isn't why you should find Flame interesting. The important thing about Flame is that it represents what else might be out there… the threats that are still unknown.
• So I'm not safe?
Go back and ask yourself the am I at risk question!
Commercial based antivirus and security products are designed for and focus on protecting you from prevalent classes of in the wild threats coming from criminals, thugs and digital mobsters (and it's a constant battle). It is not designed to protect you from the digital equivalent of Seal Team Six. So if you're the guy that finds himself in the crosshairs… you're not safe.
• How about the future? Will Flame's tech give cyber-criminals new tools to work with? Should I worry about that?
Two of our lab analysts literately laughed out loud when asked that question. Flame is big. It's complex (just as lots of legitimate software is complex). But it's not advanced crimeware. It's different. Data stealing crimeware is interested in the quickest, most efficient way to steal what it needs. And it evolves quickly. You might call that: advanced evolution.
Flame on the other hand is a "limited edition" spy tool with a limited scope that was used very carefully. It didn't need to evolve. Clearly there was advanced planning involved, but that doesn't necessarily make it what we would call advanced technology.
• What was Flame designed for?
Information gathering. And not just data from the computer, but also conversations and chats, contacts — intelligence.
• Who made Flame?
Well, it isn't designed for profit. It is too big and "complex" to have been designed by "hackers". So that leaves us with a nation state.
• Wait. What? Nation states spy?
Yeah. We know… shocking but true. #sarcasm
Nation states spy — when have they not? It shouldn't be surprising to anybody that they use digital espionage tools there days.
• What nation made Flame?
It's evident that significant resources went into crafting Flame. Given that, we think a better question is what defense contractor developed Flame.
• Defense contractor?
Yes. The way in which Flame is structured suggests to us that it was written by a contractor — an organization that is being paid.
• Defense contractors develop stuff like Flame?
Have a look for yourself. Here's something that Mikko recently tweeted about.
Here's the job posting for a Cyber Software Engineer:
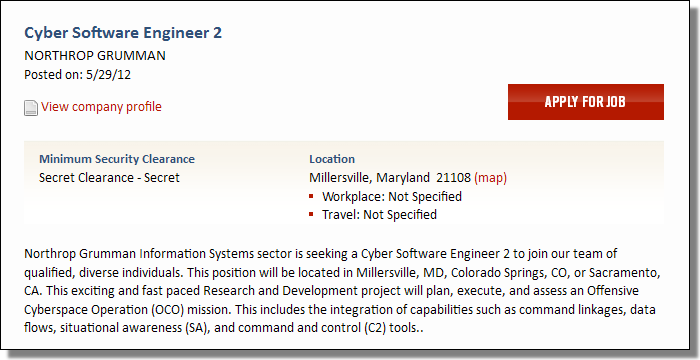
"This exciting and fast paced Research and Development project will plan, execuate, and assess an Offensive Cyberspace Operation (OCO) mission."
The Preferred Qualifications:
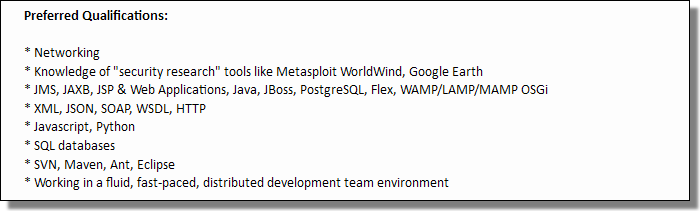
Hmm, SQL databases. Flame uses SQL databases… but no mention of the programming language Lua. Still, looks to us like defense contractors have a particular way of working with this kind of stuff.
And it's not just Northrop Grumman. Lots of defense contractors have positions for this type of project. You know, other companies such as Lockheed Martin and Raytheon.
• Wait, Northrop Grumman, Lockheed Martin and Raytheon? Haven't I read something "hacker" related to those (and other) companies recently?
Oh yes! That's right. The RSA Hack. Yes, defense contractors where among the many companies targeted as a consequence of the hack on RSA.
• What do you suppose the (allegedly Chinese) hackers took from them?
• Could China have Flame too?
• Am I "safe"?
Umm, upon reflection, maybe there's no one good answer for that.
It's complicated. (Get used to it.)
—————
P.S. Does anybody else find it disturbing that Northrop Grumman's preferred qualifications include knowledge of "security research" tools such as Metasploit, World Wind, and Google Earth?
On 30/05/12 At 04:43 PM
Weiterlesen...
There are plenty of questions from customers, and also from members of the press.
Mikko spoke with Clark Boyd of PRI's The World yesterday about the breaking news.
Symantec's Liam O Murchu spoke with Kai Ryssdal of Marketplace in a very measured and "economical" conversation about Flame's functionality.
Some good questions have been asked. And plenty of hyperbole has been generated.
Here are some questions of our own.
• Am I protected from Flame?
That's the wrong question. You should be asking yourself this: am I at risk?
• Alright then, am I at risk from Flame?
Let's see, are you a systems administrator for a Middle Eastern government?
No? Then no… you aren't at risk.
The number of computers estimated to be infected with Flame is one thousand and there are more than one billion Windows computers in the world. You do the math. You're just as likely to win the lottery.
Additionally: Flame is not a worm. Its architecture includes wormable functionality but those functions are disabled by default. So Flame isn't spreading like a worm and therefore you won't be infected unless you've been specifically targeted.
And then there's the fact that Flame is now known to be in the wild. And so… it's been "turned off". Even Flame's targets are no longer at risk. The real power of an espionage tool is that it's a secret. Flame is no longer a secret and so it will therefore be abandoned. Operational security has been compromised.
• Okay, but still — in theory — am I protected?
We have detections for Flame and our current software blocks and prevents Flame from functioning based on our tests. If you have the most current version of your antivirus software and it's functioning properly with up to date databases, you should be good.
• So I'm safe?
Safe? Okay look… Flame is estimated to be at least two years old. That's old in terms of software code. And Flame is now a known quantity. You don't need to worry about it. Flame has been extinguished.
But…that isn't why you should find Flame interesting. The important thing about Flame is that it represents what else might be out there… the threats that are still unknown.
• So I'm not safe?
Go back and ask yourself the am I at risk question!
Commercial based antivirus and security products are designed for and focus on protecting you from prevalent classes of in the wild threats coming from criminals, thugs and digital mobsters (and it's a constant battle). It is not designed to protect you from the digital equivalent of Seal Team Six. So if you're the guy that finds himself in the crosshairs… you're not safe.
• How about the future? Will Flame's tech give cyber-criminals new tools to work with? Should I worry about that?
Two of our lab analysts literately laughed out loud when asked that question. Flame is big. It's complex (just as lots of legitimate software is complex). But it's not advanced crimeware. It's different. Data stealing crimeware is interested in the quickest, most efficient way to steal what it needs. And it evolves quickly. You might call that: advanced evolution.
Flame on the other hand is a "limited edition" spy tool with a limited scope that was used very carefully. It didn't need to evolve. Clearly there was advanced planning involved, but that doesn't necessarily make it what we would call advanced technology.
• What was Flame designed for?
Information gathering. And not just data from the computer, but also conversations and chats, contacts — intelligence.
• Who made Flame?
Well, it isn't designed for profit. It is too big and "complex" to have been designed by "hackers". So that leaves us with a nation state.
• Wait. What? Nation states spy?
Yeah. We know… shocking but true. #sarcasm
Nation states spy — when have they not? It shouldn't be surprising to anybody that they use digital espionage tools there days.
• What nation made Flame?
It's evident that significant resources went into crafting Flame. Given that, we think a better question is what defense contractor developed Flame.
• Defense contractor?
Yes. The way in which Flame is structured suggests to us that it was written by a contractor — an organization that is being paid.
• Defense contractors develop stuff like Flame?
Have a look for yourself. Here's something that Mikko recently tweeted about.
Northrop Grumman is seeking a "Cyber Software Engineer" to execute "An Offensive Cyberspace Operation Mission". Hmm... clearancejobs.com/jobs/1536410/c
— Mikko Hypponen (@mikko) May 18, 2012
— Mikko Hypponen (@mikko) May 18, 2012
Here's the job posting for a Cyber Software Engineer:

"This exciting and fast paced Research and Development project will plan, execuate, and assess an Offensive Cyberspace Operation (OCO) mission."
The Preferred Qualifications:

Hmm, SQL databases. Flame uses SQL databases… but no mention of the programming language Lua. Still, looks to us like defense contractors have a particular way of working with this kind of stuff.
And it's not just Northrop Grumman. Lots of defense contractors have positions for this type of project. You know, other companies such as Lockheed Martin and Raytheon.
• Wait, Northrop Grumman, Lockheed Martin and Raytheon? Haven't I read something "hacker" related to those (and other) companies recently?
Oh yes! That's right. The RSA Hack. Yes, defense contractors where among the many companies targeted as a consequence of the hack on RSA.
• What do you suppose the (allegedly Chinese) hackers took from them?
• Could China have Flame too?
• Am I "safe"?
Umm, upon reflection, maybe there's no one good answer for that.
It's complicated. (Get used to it.)
—————
P.S. Does anybody else find it disturbing that Northrop Grumman's preferred qualifications include knowledge of "security research" tools such as Metasploit, World Wind, and Google Earth?
On 30/05/12 At 04:43 PM
Weiterlesen...
