Newsfeed
Nachrichtenbote
The backdoor known as "MiniDuke" was identified in Feburary 2013, discovered in a series of attacks against NATO and European government agencies. During MiniDuke analysis in April 2014, we determined that another malware family was using the same loader as MiniDuke stage 3. That malware is part of the Cosmu family of information-stealers which have been around for years.
What makes the connection to MiniDuke interesting is that, based on compilation timestamps, it was Cosmu, not MiniDuke, which originally used the common shared loader. Moreover, we found that the loader was updated at some point, and both malware families took the updated loader into use. Since Cosmu is the first malware known to share code with MiniDuke, we decided to name the samples showing this amalgamation of MiniDuke-derived loader and Cosmu-derived payload as CosmicDuke.

(Image: NASA — Charles M. Duke, lunar module pilot of Apollo 16.)
The filenames and content used in CosmicDuke's attack files to lure victims contain references to the countries of Ukraine, Poland, Turkey, and Russia, either generally in use of language or included detail, or in allusions to events or institutions. The filenames and content chosen seem to be tailored to their targets interests, though we have no further information on the identity or location of these victims yet.
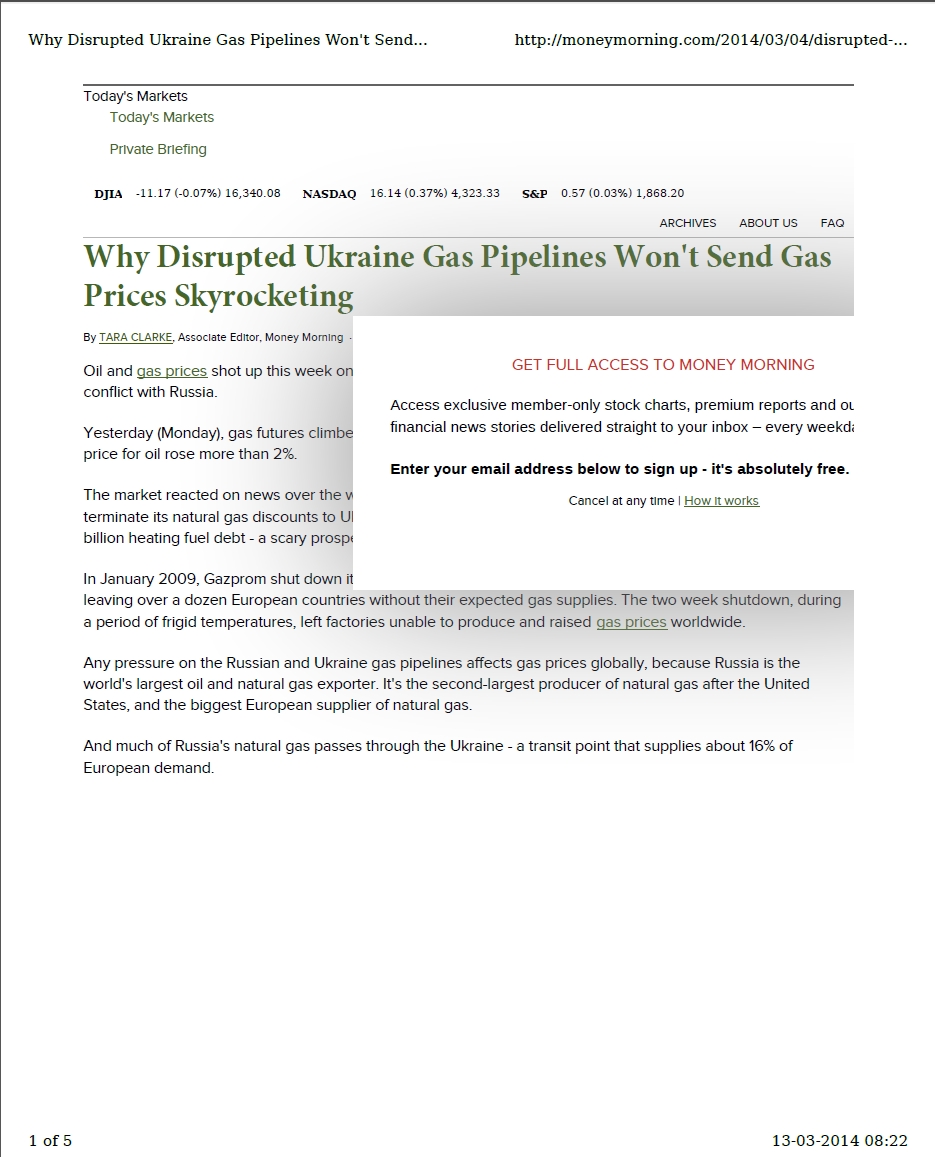
CosmicDuke infections start by tricking targets into opening either a PDF file which contains an exploit or a Windows executable whose filename is manipulated to make it look like a document or image file. Some of the samples display a decoy document to the user. This one was named Ukraine-Gas-Pipelines-Security-Report-March-2014.pdf:
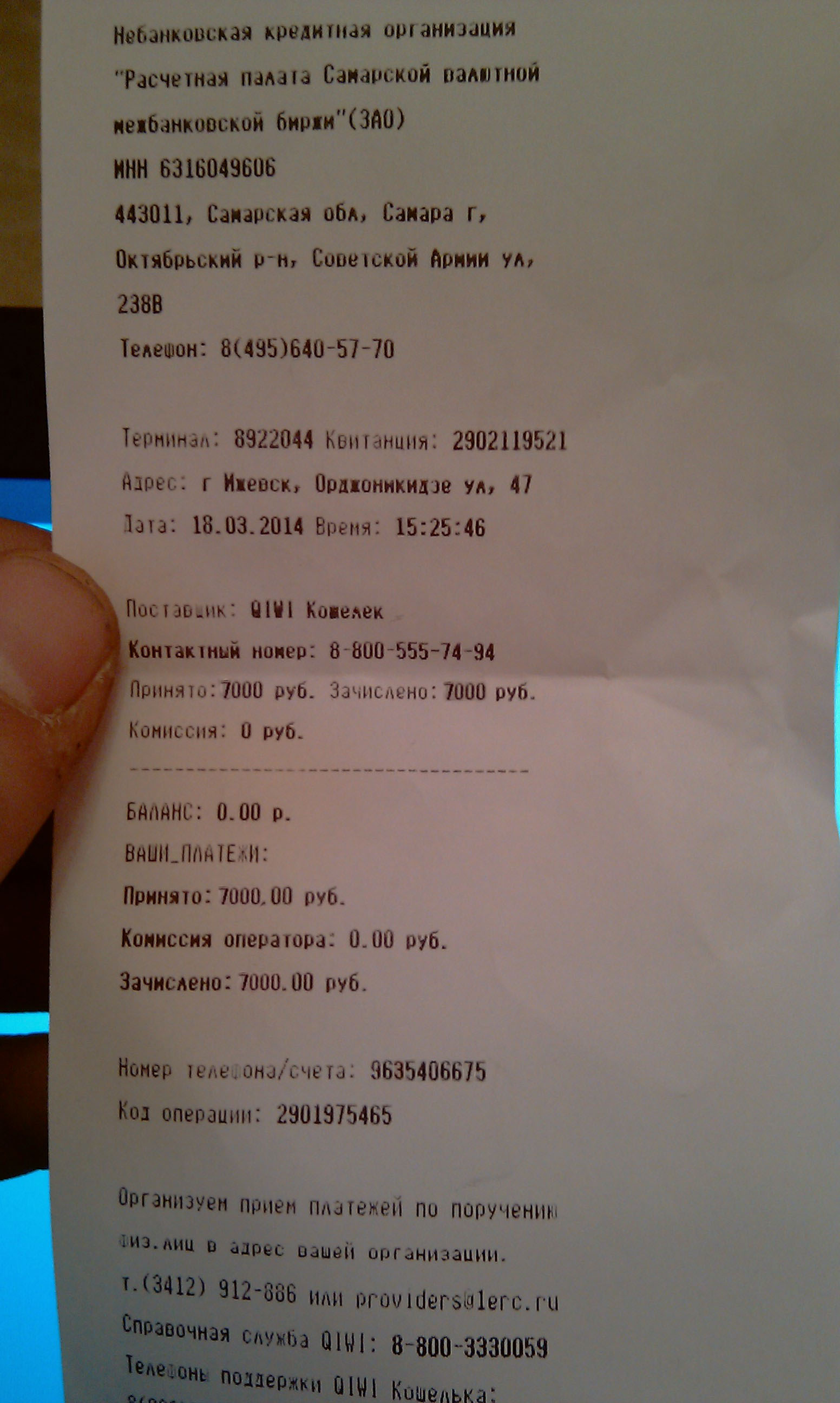
Here's a rather different kind of a decoy, showing a receipt of a payment in Russian. An interesting detail about the image file is that it contains EXIF metadata, including the date when the photo was taken and the model of the mobile phone that was used to take the photo.
Once the target opens the malicious file, CosmiDuke gains persistence on the system and starts collecting information. The data collection components include a keylogger, clipboard stealer, screenshotter, and password stealers for a variety of popular chat, e-mail and web browsing programs. CosmicDuke also collects information about the files on the system, and has the capability to export cryptographic certificates and the associated private keys.
Once the information has been collected, it is sent out to remote servers via FTP. In addition to stealing information from the system, CosmicDuke allows the attacker to download and execute other malware on the system.
F-Secure has detections for all of the different malicious components used by the CosmicDuke samples known to us.
To learn more about the technical details, please see our CosmicDuke malware analysis report.
Post by — Timo
On 02/07/14 At 03:55 PM
Weiterlesen...
What makes the connection to MiniDuke interesting is that, based on compilation timestamps, it was Cosmu, not MiniDuke, which originally used the common shared loader. Moreover, we found that the loader was updated at some point, and both malware families took the updated loader into use. Since Cosmu is the first malware known to share code with MiniDuke, we decided to name the samples showing this amalgamation of MiniDuke-derived loader and Cosmu-derived payload as CosmicDuke.

(Image: NASA — Charles M. Duke, lunar module pilot of Apollo 16.)
The filenames and content used in CosmicDuke's attack files to lure victims contain references to the countries of Ukraine, Poland, Turkey, and Russia, either generally in use of language or included detail, or in allusions to events or institutions. The filenames and content chosen seem to be tailored to their targets interests, though we have no further information on the identity or location of these victims yet.
CosmicDuke infections start by tricking targets into opening either a PDF file which contains an exploit or a Windows executable whose filename is manipulated to make it look like a document or image file. Some of the samples display a decoy document to the user. This one was named Ukraine-Gas-Pipelines-Security-Report-March-2014.pdf:

Here's a rather different kind of a decoy, showing a receipt of a payment in Russian. An interesting detail about the image file is that it contains EXIF metadata, including the date when the photo was taken and the model of the mobile phone that was used to take the photo.

Once the target opens the malicious file, CosmiDuke gains persistence on the system and starts collecting information. The data collection components include a keylogger, clipboard stealer, screenshotter, and password stealers for a variety of popular chat, e-mail and web browsing programs. CosmicDuke also collects information about the files on the system, and has the capability to export cryptographic certificates and the associated private keys.
Once the information has been collected, it is sent out to remote servers via FTP. In addition to stealing information from the system, CosmicDuke allows the attacker to download and execute other malware on the system.
F-Secure has detections for all of the different malicious components used by the CosmicDuke samples known to us.
To learn more about the technical details, please see our CosmicDuke malware analysis report.
Post by — Timo
On 02/07/14 At 03:55 PM
Weiterlesen...
