Newsfeed
Nachrichtenbote
Digital security is something that human rights activists are concerned about, and they should be…
Here in the lab, we see many examples of targeted malware attacks focused on human rights organizations. Here's one example from September 3rd that ironically uses "digital security training" as the hook.
The spoofed message is very well done; the content uses real names, organizations, e-mail addresses, phone numbers, et cetera.
It looks very legitimate at first glance.
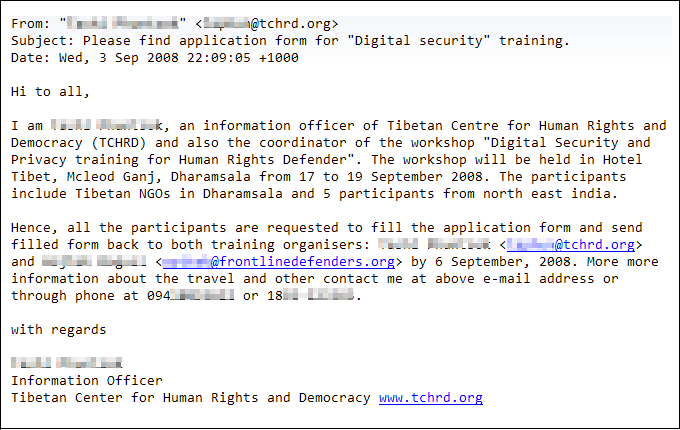
The message was sent to a human rights activist based in the Southeast USA. There was a Word document attached.
It too uses real names, locations, and so on.
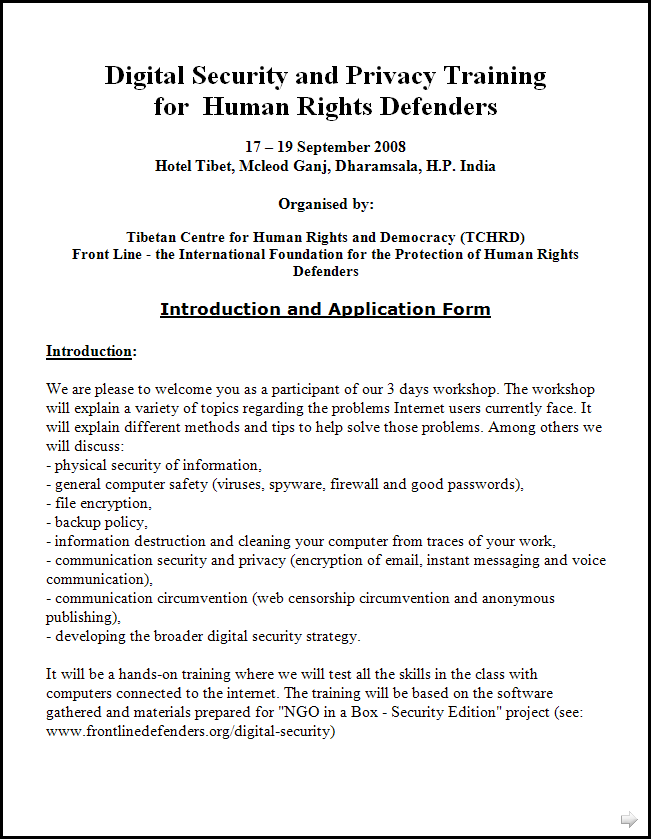
Fortunately, the recipient of this message was knowledgeable enough to avoid opening the attachment. Instead of opening it, he forwarded it to the lab for analysis.
Yep. It was a trap. The Word document had an exploit.
The only thing about this case that seems to indicate "hackers" rather than "spies" is the document's author.
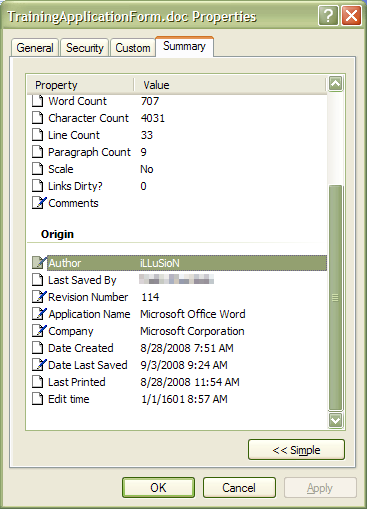
…perhaps the spies are paying the hackers?
Front Line Defenders, mentioned in the e-mail message actually has some very good security advice on their site.
They should perhaps add one more topic — targeted malware attacks.
You can read more on the topic from Wired.com.
P.S. Front Line's Software Installation guide suggests uninstalling ALL unused Windows applications. Great idea.
Human Rights Organizations really concerned with digital security might also consider going one step further by giving something such as Ubuntu a try. It's free, has all of the needed applications, and none of the current exploits being used against activists. On 05/09/08 At 08:26 PM
Weiterlesen...
Here in the lab, we see many examples of targeted malware attacks focused on human rights organizations. Here's one example from September 3rd that ironically uses "digital security training" as the hook.
The spoofed message is very well done; the content uses real names, organizations, e-mail addresses, phone numbers, et cetera.
It looks very legitimate at first glance.

The message was sent to a human rights activist based in the Southeast USA. There was a Word document attached.
It too uses real names, locations, and so on.

Fortunately, the recipient of this message was knowledgeable enough to avoid opening the attachment. Instead of opening it, he forwarded it to the lab for analysis.
Yep. It was a trap. The Word document had an exploit.
The only thing about this case that seems to indicate "hackers" rather than "spies" is the document's author.

…perhaps the spies are paying the hackers?
Front Line Defenders, mentioned in the e-mail message actually has some very good security advice on their site.
They should perhaps add one more topic — targeted malware attacks.
You can read more on the topic from Wired.com.
P.S. Front Line's Software Installation guide suggests uninstalling ALL unused Windows applications. Great idea.
Human Rights Organizations really concerned with digital security might also consider going one step further by giving something such as Ubuntu a try. It's free, has all of the needed applications, and none of the current exploits being used against activists. On 05/09/08 At 08:26 PM
Weiterlesen...
